Comments (83)
Hello,
I just tried and can confirm that is not working. There are a few network calls initiated by classes that explicitly check the certificate (GCDAsyncSocket, FBMQTTNativeClient, RCTSRWebSocket). I will need to think of a way to generically disable this type of certificate check, which might be difficult. Will look into it when I have time.
from ssl-kill-switch2.
I hooked -[FBLigerConfig initWithLigerEnabled: ...] method, change the first argument to NO, then hook -[FBSSLPinningVerifier checkPinning:], change the return value to YES.
Everything works now!
Looks like Facebook have multiple Network Engine's, Liger is one of them, If I disable Liger, it will fallback to use the FBSSLPinningVerifier
I made an repo about this: https://github.com/Naituw/HackingFacebook
from ssl-kill-switch2.
 commented on May 22, 2024
11
commented on May 22, 2024
11
Hi,
I have been doing some research and it appears that these days many applications are conducting ssl pinning by OpenSSL library, usually with stripped symbols.
Thus i have wrote simple patcher for this and similar old school hooking with set of hooks/tasks.
https://github.com/karek314/hexbytescanner - binary patcher with json hooks
https://github.com/karek314/hexbytescanner-hooks - hooks itself
Right now i have found that popular library is OpenSSL 1.0.2, if binary does have symbols, ssl pinning can be easily disabled by hooking ssl_verify_cert_chain. However, often it's not possible because of missing symbols.
It can be solved with .json hook and patcher i've made. Hook below is OpenSSL 1.0.2 hook on aarch64
[
{
"pattern": "94????0034E80340F9FF0218EB??FCFF54E00313AAE10314AA",
"patchBytes": "1F2003D5",
"patchDistance": "0x1"
}
]
In case someone needs it, here is simple shell script assisting in repacking ipa https://github.com/karek314/HandyIPAPatcher
Additionally, those hooks can be also implemented in ssl-kill-switch2 by utilising vm_read and vm_write with more traditional dynamic byte pattern scanning and patching. If i will find some more free time i will prepare pr, however maybe it will interest you @nabla-c0d3.
If anyone finds some other hooks and feels like sharing them, feel free to pr those in https://github.com/karek314/hexbytescanner-hooks
from ssl-kill-switch2.
I tried disabling pinning in FBMQTTNativeClientand, RCTSRWebSocket and FBSSLPinningVerifier but it still wasn't enough. I'll look into again when I have time.
from ssl-kill-switch2.
It also doesn't work with World of Warcraft Armory, It works correctly until you login, then it doesn't catch anything besides the regular google analytics calls
from ssl-kill-switch2.
@liuxuan30 it's relevant because it proves that these other apps could be using the same protection that Facebook is using for Messenger. One of them could have a lighter protection than Messenger, making it easier to crack whatever Messenger is doing here.
from ssl-kill-switch2.
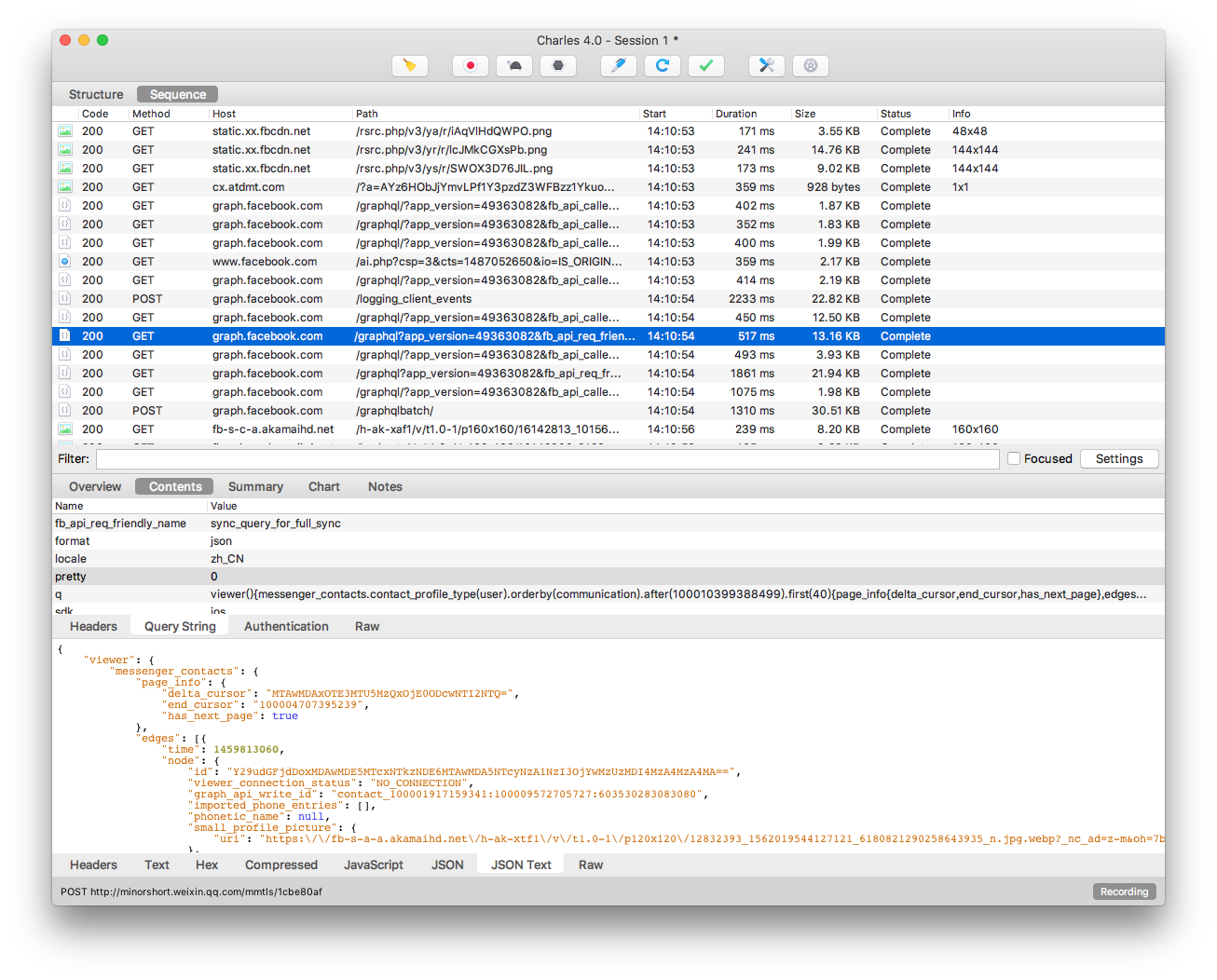
In case anyone is still looking at this: Messenger seems to wrap every request in NSMutableURLRequest objects. If you place the right hooks for this class you'll see exactly where a request is going, with which headers, etc. This is regardless of where it comes from (i.e. GraphApiRequest, MediaStreamingUploadJob, etc etc).
Those NSMutableURLRequest objects get pushed into a dispatch queue that then gets picked up by FBTigonHttpExecutor (this is not the only 'executor' class!). The executor creates queue com.facebook.networkerrequest.internal and it uses it to process requests. I suspect they key to the certificate pinning logic may be in the code blocks that are passed to this queue, which would explain why you cannot immediately see the logic explicitly after disassembling. As an example, take a look at FBMediaStreamingUploadJobStatusFetcher, selector ->(fetchStatusFromURL:config:withSuccess:failure:cancellation:).
I haven't had the time to look at the code blocks though. I may be wrong but I felt I should put it out there in case anyone's hunting for this too. If you are, gimme a shout!
from ssl-kill-switch2.
This is still on my TODO list, I just haven't had time to look at this again.
from ssl-kill-switch2.
@bruno-rocha-movile please don't add irrelevant topic to this thread, as you can see the title is
Not working with Facebook
you should file a new one if needed.
from ssl-kill-switch2.
@liuxuan30 Yes! All request captured by Charles is succeeded.
from ssl-kill-switch2.
 commented on May 22, 2024
2
commented on May 22, 2024
2
The only way to bypass facebook SSL pinning for now is by using frida and objection.
from ssl-kill-switch2.
https://twitter.com/CodeDigging/status/781468522815819776
from ssl-kill-switch2.
actually can we have synergy here not just depending on @nabla-c0d3 ? I was able to track down to FBNetworkerRequest it get the response data, but can't find where it do the ssl pining
from ssl-kill-switch2.
@Naituw I will integrate this to SSL Kill Switch. If you want you can do a pull request (to get the credit / your name in the commits) or I can do it myself. Let me know and thanks!
from ssl-kill-switch2.
Great work @karek314!
from ssl-kill-switch2.
 commented on May 22, 2024
1
commented on May 22, 2024
1
@asad0x01 Doesn't work anymore. It for sure does work with OpenSSL 1.1.0 and 1.0.2 ARM64(which still does work with many apps). Current answer lays in https://github.com/facebookincubator/fizz it does pinning now, it's open source, shouldn't be hard but I haven't had time to play around. In past it relied with pinning on OpenSSL. If anyone finds stable pattern to hook pinning function, feel free to share patch here https://github.com/karek314/hexbytescanner-hooks :)
from ssl-kill-switch2.
Hm, I actually can't reproduce. I'm using facebook 52.0 with mitmproxy and my script is successfully pulling out the email and password from my login attempts.
from ssl-kill-switch2.
Seems that it's certain APIs. graph.facebook.com and api.facebook.com fail, but I could register an account through b-api.facebook.com/ without issue.
from ssl-kill-switch2.
Yes, it is specific APIs.
from ssl-kill-switch2.
It is not working on my phone too, any update ?
from ssl-kill-switch2.
Any update?
from ssl-kill-switch2.
@nabla-c0d3 , I assume it's similar for Facebook's messenger app, tried a bunch of things with no luck, I wish I knew more in this domain to be able to help.
from ssl-kill-switch2.
@alfonsoperez Yes, it's the same.
Same struggle.
from ssl-kill-switch2.
GCDAsyncSocket actually does SSL pinning with the usual SecureTransportAPI that's already taken care of by SSL Kill Switch ( https://github.com/robbiehanson/CocoaAsyncSocket/blob/master/Source/GCD/GCDAsyncSocket.m#L6794 )
The remaining classes to patch are FBMQTTNativeClientand RCTSRWebSocket (most likely this https://github.com/facebook/react-native/blob/master/Libraries/WebSocket/RCTSRWebSocket.h#L114 ) which I will look at whenever I have time.
from ssl-kill-switch2.
Any new clues about facebook ?
Thanks
from ssl-kill-switch2.
 commented on May 22, 2024
commented on May 22, 2024
Simple fix for that is to hook RCTSRWebSocket function called _checkHandshake
from ssl-kill-switch2.
@nabla-c0d3 what you mean by 'still wasn't enough'? It work partially or not work at all?
from ssl-kill-switch2.
@karek314 can you jus tell me how to bypass Facebook app SSL pining for now as a work around? I am ok to inject tweaks? I tried to let _checkHandshake return YES, however, no luck
from ssl-kill-switch2.
From what I found is FBNetworkerRequest class is handling the requests and reponses like graph.facebook.com, however, not finding a way to bypass SSL pinning.
from ssl-kill-switch2.
I did some research, and didn't find yet a solution. @liuxuan30 did you get more results on your side ?
from ssl-kill-switch2.
as I said, I just found that the API requests are sending out by FBNetworkerRequest. I don't find how FBNetworkerRequest enforce SSL pinning.
from ssl-kill-switch2.
@ch3repatz Impatiently awaiting for details 👍
from ssl-kill-switch2.
@alfonsoperez hope the author will share his research, not just the screenshot
from ssl-kill-switch2.
@ch3repatz can't wait.. why just a screenshot
from ssl-kill-switch2.
@liuxuan30 I don't know, ask the author of research please. I just found the tweet and copied here.
from ssl-kill-switch2.
Just asked and get a reply:"Do you mind sharing?"; "No, it's a non-public research for my customer."
So we are still on our own LOL
from ssl-kill-switch2.
@liuxuan30 sad :(
Ok, let's wait for update from @nabla-c0d3
from ssl-kill-switch2.
@nabla-c0d3 I found that I hooked GCDAsyncSocket ssl related functions, but no one get called. Seems it's not using GCDAsyncSocket at all? Can anyone double check?
from ssl-kill-switch2.
It's not used in the flows that I have seen. Same with FBMQTTNativeClientand, RCTSRWebSocket and FBSSLPinningVerifier. Overall it's unclear to me where the pinning validation logic is happening during the login flow, but I haven't had time to look at it that much.
from ssl-kill-switch2.
@nabla-c0d3 np, I just looked into it and want to save your time when you sit down and working on this. What I find is that the upper FBNetworkerRequest is sending the FB api requests, and doing the ssl pining somewhere in the process.
it not uses FBSSLPinningVerifier in its api network e.g. graph.facebook.com
from ssl-kill-switch2.
That's very helpful, thanks!
from ssl-kill-switch2.
@salcho, Thanks, very helpful!
I hooked -[FBTigonHttpExecutor addRequest:delegate:callbackQueue:] and successfully dumped out request informations. I think the response can be inspected by this way too (hook all classes conforms to FBHttpRequestDelegate).
[NSClassFromString(@"FBTigonHttpExecutor") aspect_hookSelector:@selector(addRequest:delegate:callbackQueue:) withOptions:AspectPositionBefore usingBlock:^(id<AspectInfo> aspectInfo) {
id<FBHttpRequest> request = [[aspectInfo arguments] firstObject];
NSURLRequest * urlRequest = [request request];
NSLog(@"Captured Request: %@ %@", urlRequest.HTTPMethod, urlRequest.URL);
} error:&error];
from ssl-kill-switch2.
I also pushed my fb-experiments branch with all the hooks I tried (but that were unsuccessful).
from ssl-kill-switch2.
The request added in FBTigonHttpExecutor has some limitations, for example it doesn't include authentication parameters, If I replay the request, 403 error will occur.
After some digging, I hooked -[FBAccessToken initWithToken:], and append the result to the end of request url like this &access_token=XXX, most of the request works, but some request still fails for certain domain.
So I'm still looking for a way to kill the ssl pinning directly...
I suspect the pinning logic is in the FBLiger or TigonService's C++ code, because Facebook Messenger dose that too according to this article https://serializethoughts.com/2016/08/18/bypassing-ssl-pinning-in-android-applications .
It's there any way to dump the headers or pseudocode for the C++ part? I have little experience about this.
from ssl-kill-switch2.
 commented on May 22, 2024
commented on May 22, 2024
It's there any way to dump the headers or pseudocode for the C++ part? I have little experience about this.
Hopper or IDA Pro with hexray plugin for pseudocode should be enough to generate pseudocode.
I had some workaround solution for this task before, it worked so i have stopped further research on that as i have checked what i needed. Maybe it looks funny, however solutions like this sometimes works just fine to find what you are looking, without unnecessary effort.
Just paste this in Cycript, shortly before request you want to catch since this most likely will crash app shortly after making request.
__NSCFString.prototype['isEqualToString:'] = function (x) {var e; e=this; NSLog("CHECK IF EQUAL:%@/%@",x,e); if(x==e){NSLog("TRUE");return true;} else {NSLog("FALSE");return false;} };Or replace true with false, actually i don't remember which variant made it work.
from ssl-kill-switch2.
@karek314 That's the nuclear option haha.
@Naituw I've never done it for C++ code but I know it can be done (as the symbols for the pinning functions must be public) - will look into this when I have some time.
from ssl-kill-switch2.
Has someone looked at FBLigerSSLCertificateRequestObserver? I remember it will get called when SSL fails, but I can't find who's calling.
from ssl-kill-switch2.
Wow @Naituw nice catch. All graphQL requests are supported?
Could you please do a quick check, if it can also see the news feed requests?
from ssl-kill-switch2.
fantastic :) It's definitely a solution here. Though the magic still lies in liger engine.
from ssl-kill-switch2.
@nabla-c0d3 Thank you! I'm not that familiar with subtrate api and don't have jailbreak device to test it. So I think the best way is integrate this by you, very appreciated!
from ssl-kill-switch2.
One more thing, since this is public now, Facebook must will do something 😂
from ssl-kill-switch2.
@nabla-c0d3 waiting for your integration impatiently. thank you.
from ssl-kill-switch2.
This is slightly more difficult than I thought because initWithLigerEnabled: changes a lot across releases (as @Naituw you mentioned in your code =) ). I have an idea on how to hook this but it will take some time.
from ssl-kill-switch2.
@nabla-c0d3 Yes, the argument list changes. The workaround I use is to hook the longest method for FBLigerConfig, which may seems wired ;). but it works for recent versions (at least from early 2016).
from ssl-kill-switch2.
@Naituw looks like latest FB app (v 93.0) has changed and the killer switch does not work any more? Could you confirm? Thanks
from ssl-kill-switch2.
@karek314 how to detect it use OpenSSL library?
from ssl-kill-switch2.
 commented on May 22, 2024
commented on May 22, 2024
@mdbrelo look for string "openssl", usually it has embedded path, if that fails for some reason you can try locate some openssl specific strings.
https://github.com/openssl/openssl/tree/OpenSSL_1_1_0-stable
from ssl-kill-switch2.
great. I'm trying to learn how to use ida and asm language but it's really hard
from ssl-kill-switch2.
@karek314 any ETA you would file a PR for this? Very interested.
from ssl-kill-switch2.
 commented on May 22, 2024
commented on May 22, 2024
@liuxuan30 I will when I'll have more time, right now you can just use https://github.com/karek314/hexbytescanner and patch binaries manually before deploying them.
from ssl-kill-switch2.
Could please anybody share the final ipa for Facebook with patched ssl pinning? Unfortunately i dont have any framework for patching it myself(
from ssl-kill-switch2.
from ssl-kill-switch2.
U have the facebook patched ipa? Could you please share it?
It is my passion to study https of facebook and that kills me that i am unable to patch it myself to see(((
from ssl-kill-switch2.
@dedfft you can use this guide by @phwd https://www.facebook.com/113702895386410/videos/1466262083463811/ .Let me know if you need IPA :)
from ssl-kill-switch2.
Hello Asad, thank you for the video hint! I have already watched it this year several times, unfortunately i was unable to replicate the procedure several times and was disappointed in myself..
I am curios not in the process of debugging of an ipa, but more in looking at how facebook works inside..
If you could share already patched ipa with me, it would be amazing!
Could you? If that is not too much to ask. Please
from ssl-kill-switch2.
from ssl-kill-switch2.
@asad0x01 I would also want to have one thank you. email is [email protected]
from ssl-kill-switch2.
@dedfft you can use this guide by @phwd https://www.facebook.com/113702895386410/videos/1466262083463811/ .Let me know if you need IPA :)
@asad0x01 can you share .ipa file with me as well? email: [email protected].
Many thanks!
from ssl-kill-switch2.
Hey sorry guys.The latest Facebook app is crashing.Still I'm able to intercept https request of other apps.(Moments,Facebook Page Manager). Let me know if you need any of them.I've the base IPA of Facebook app.Not the modified one.
from ssl-kill-switch2.
For android you can try https://github.com/pouyadarabi/Facebook_SSL_Pinning (Facebook for android Version 175).Also make sure that your android version is Lollipop or above.
from ssl-kill-switch2.
Here is the Stock IPA of Facebook APP:https://mega.nz/#!lmpBHIAI!yEMBmTSVHmHNzmXB-Jq8_TMzTOvV5fbZ-awJUGxvsxs
Here is the Modified Facebook Pages IPA:https://mega.nz/#!omhlQY6A!95c5LW34bcpFyP1u_G8s32kKrYL1Wlf0oEI49AxZuHA
Here is the Modified Moments IPA:https://mega.nz/#!RngjwArB!AjD66ZXnjNVOvPLs_nfIAEkplI-xgOnUc4q5KU8-LPw
You can install those IPA's using Cydia Impactor.Note that you can only intercept request of those TWO IPA(Facebook Page Manager and Moments).
Thanks to @phwd
from ssl-kill-switch2.
Thank you asad, that is fantastic!!
But what about main favebook patched app? Ipa
from ssl-kill-switch2.
It's crashing unfortunately :( But when I tried it a months ago it was working perfectly.However I'll wait for the next update :)
from ssl-kill-switch2.
I'm trying to do this with Instagram, should this process work ? How could I disable it's SSL pinning?
from ssl-kill-switch2.
Maybe any luck with disabled ssl pinning on previous Facebook app versions? I really need at least anything((
from ssl-kill-switch2.
@asad0x01 can you do other apps as well? Please email me: [email protected]
from ssl-kill-switch2.
Hi,
I have been doing some research and it appears that these days many applications are conducting ssl pinning by OpenSSL library, usually with stripped symbols.
Thus i have wrote simple patcher for this and similar old school hooking with set of hooks/tasks.
https://github.com/karek314/hexbytescanner - binary patcher with json hooks
https://github.com/karek314/hexbytescanner-hooks - hooks itselfRight now i have found that popular library is OpenSSL 1.0.2, if binary does have symbols, ssl pinning can be easily disabled by hooking ssl_verify_cert_chain. However, often it's not possible because of missing symbols.
It can be solved with .json hook and patcher i've made. Hook below is OpenSSL 1.0.2 hook on aarch64
[ { "pattern": "94????0034E80340F9FF0218EB??FCFF54E00313AAE10314AA", "patchBytes": "1F2003D5", "patchDistance": "0x1" } ]In case someone needs it, here is simple shell script assisting in repacking ipa https://github.com/karek314/HandyIPAPatcher
Additionally, those hooks can be also implemented in ssl-kill-switch2 by utilising
vm_readandvm_writewith more traditional dynamic byte pattern scanning and patching. If i will find some more free time i will prepare pr, however maybe it will interest you @nabla-c0d3.If anyone finds some other hooks and feels like sharing them, feel free to pr those in https://github.com/karek314/hexbytescanner-hooks
Is it possible to do this without a mac using frida?
from ssl-kill-switch2.
 commented on May 22, 2024
commented on May 22, 2024
@S00164379 Nope. hexbytescanner is written in Objective C++, shouldn't be that hard to rewrite to C++ though.
from ssl-kill-switch2.
@asad0x01 can you do other apps as well? Please email me: [email protected]
ah!NO!Sorry :(
from ssl-kill-switch2.
@asad0x01 any luck with latest Facebook app?
from ssl-kill-switch2.
Hi,
I have been doing some research and it appears that these days many applications are conducting ssl pinning by OpenSSL library, usually with stripped symbols.
Thus i have wrote simple patcher for this and similar old school hooking with set of hooks/tasks.
https://github.com/karek314/hexbytescanner - binary patcher with json hooks
https://github.com/karek314/hexbytescanner-hooks - hooks itselfRight now i have found that popular library is OpenSSL 1.0.2, if binary does have symbols, ssl pinning can be easily disabled by hooking ssl_verify_cert_chain. However, often it's not possible because of missing symbols.
It can be solved with .json hook and patcher i've made. Hook below is OpenSSL 1.0.2 hook on aarch64
[ { "pattern": "94????0034E80340F9FF0218EB??FCFF54E00313AAE10314AA", "patchBytes": "1F2003D5", "patchDistance": "0x1" } ]In case someone needs it, here is simple shell script assisting in repacking ipa https://github.com/karek314/HandyIPAPatcher
Additionally, those hooks can be also implemented in ssl-kill-switch2 by utilising
vm_readandvm_writewith more traditional dynamic byte pattern scanning and patching. If i will find some more free time i will prepare pr, however maybe it will interest you @nabla-c0d3.If anyone finds some other hooks and feels like sharing them, feel free to pr those in https://github.com/karek314/hexbytescanner-hooks
@nabla-c0d3 do you have any plan to implement this in ssl kill switch 2?Thanks in advance :)
from ssl-kill-switch2.
The only way to bypass facebook SSL pinning for now is using frida and objection.
a very complicated way. :( okay…
from ssl-kill-switch2.
 commented on May 22, 2024
commented on May 22, 2024
The only way to bypass facebook SSL pinning for now is using frida and objection.
a very complicated way. :( okay…
https://github.com/tsarpaul/FBUnpinner
from ssl-kill-switch2.
Related Issues (20)
- Step by step manual for MacOS
- do not support flutter app with handshack
- Iphone XR... iOS 14.2 SSL KILL SWITCH not working! HOT 4
- Detecting SSL Kill Switch 2 HOT 1
- can you build a deb file of the latest version? HOT 2
- not work in ip11,14.7.1 ,unc0ver HOT 4
- For windows?
- Question: Will uninstalling this app restore SSL pinning and my device will be back to full security?
- Please add support non jb device HOT 1
- jailbroke 15.3.1 by palera1n, not working HOT 2
- Is ssl-kill-switch2 work on ios 15.5 jailbreak devices HOT 31
- Not working with AppleID login,IOS13.2.3 HOT 1
- Some Packages couldn't be catched on App Store ios16 HOT 1
- Readme doesn't indicate mTLS support, or lack thereof
- How to use iOS 15.7.6 Palera1n Rootless Jailbreak
- How to install ssl-kill-switch2 on iOS 15.4 Dopamine rootless jailbreak HOT 4
- How to install ssl kill switch 2 on palera1n rootless jailbreak ios 16.7
- Does it work on iOS 16 jailbroken with palera1n?
- may be conflict with unc0ver substitute.
- ssl kill switch on IOS Simulator HOT 2
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.
from ssl-kill-switch2.