Comments (46)
A more detailed error message can be found in the /var/log/xroad/jetty/jetty.log log file. Have you checked the log file already?
Best regards,
Petteri
from x-road.
Thanks @petkivim ,
I checked it like this.
from x-road.
According to the error message the key auth key does match with the certificate which indicates that the CSR file was generated using another key. Have you completed the steps listed below in this exact order:
- Create auth key.
- Generate CSR for the auth key.
- Create a certificate using the CSR generated in step 2.
- Import the certificate.
If you have deleted and recreated the auth key after generating the CSR, you must recreate the CSR and certificate too. One possible explanation for the error message is that the auth key has been recreated and therefore, the certificate does not correspond with the current key. Another alternative is, that the current configuration of your CA is not compatible with X-Road.
Best regards,
Petteri
from x-road.
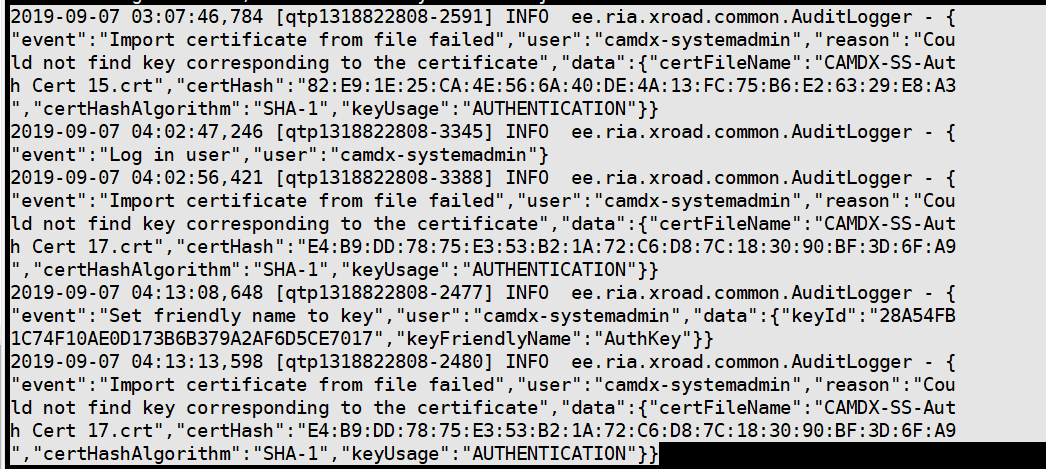
Yes it looks like that Microsoft Windows Server not support the CSR that generated from the XRoad, so I create the new CSR File in Windows server and then create the Certificate from it. So maybe it does not work with XRoad.
Best Regards,
Dara Penhchet
from x-road.
Do you have any solution to make the CSR generated from the XRoad and will support with Windows Server Certificate Authority?
Best Regards,
Dara Penhchet
from x-road.
Unfortunately, creating a new CSR file on Windows server does not work. You must use the CSR file generated by the Security Server.
X-Road requires that the CA must be able to process CSRs conforming to PKCS10:
Certification Request Syntax Standard. RSA Laboratories, PKCS 10.
We have not tried to use certificates issued by a Windows server on X-Road. However, there's a Test-CA that you can use in test and development environments. The easiest way to install and configure it is to use this script. Another alternative to consider is EJBCA.
Best regards,
Petteri
from x-road.
So do you have any plan to try to use the Certificates issued by a Windows Server on X-Road?
Best Regards,
Dara Penhchet
from x-road.
The support is not limited to any specific technologies. However, X-Road requires that the CA is compliant with the two specifications listed below. Based on your description the problem seems to be related to PKCS 10 and Windows server.
- Certification Request Syntax Standard. RSA Laboratories, PKCS 10.
- X.509 Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP. Internet Engineering Task Force, RFC 6960, 2013.
This requirement is also mentioned in the X-Road Architecture document.
By the way, have you tried both PEM and DER formats when creating the CSR on the Security Server?
Best regards,
Petteri
from x-road.
Yes I have tried both PEM and DER Formats, but it doesn't work.
Best Regards,
Dara Penhchet
from x-road.
In that case it seems that the issue is related to Windows server's PKCS 10 implementation. The next logical step would be to find out a more detailed error message on the Windows server, investigate the root cause and see if the problem can be fixed by changing the Windows server's configuration.
Best regards,
Petteri
from x-road.
I will check with the Window Server.
Thank you so much.
Best Regards,
Dara Penhchet
from x-road.
Dear petkivim,
I have changed to use the EJBCA Server to issue the ceritificate, but it still error.

Do you have any guideline to do it with EJBCA Server?
Thanks in advance.
Best Regards,
Dara Penhchet
from x-road.
Have you added the EJBCA under certification services on the Central Server according to these instructions?
What CertificateProfileInfo value did you use when adding EJBCA? With EJBCA you should use the value below:
ee.ria.xroad.common.certificateprofile.impl.EjbcaCertificateProfileInfoProvider
In case you have used some other value, you should update the value on the Central Server, wait few minutes and regenerate the CSR file. Please note that when you regenerate the CSR file, you must select the EJBCA from the Certification Service menu.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
I have tried with it already, but it still error. Could you help to check this one?
Best Regards,
Dara Penhchet
from x-road.
How does the CSR file's content look like? Could you post the output generated by the command below:
openssl req -in <MY_CSR_FILE.pem> -text -noout
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Here is the CSR content

Best Regards,
Dara Penhchet
from x-road.
Thank you! How about the content of the certificate signed using EJBCA?
openssl x509 -in <CERTIFICATE.CRT> -text -noout
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Here is the content of that certificate.

Best Regards,
Dara Penhchet
from x-road.
Thank you! The certificate in the screenshot has not been issued using the CSR that you posted before. Please take a look at the subject fields - they do not match. You should create a certificate using the CSR above and then try to import it.
The certificate above follows the Finnish certificate profile and not the EJBCA certificate profile as it should.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Could you help to check this one for me?
https://34.87.20.107/ejbca/adminweb/
Id: superadmin
Password: ipAnIQ6eftpD0YgIIsU=
Keystore:
superadmin.zip
CS1: https://35.240.251.85:4000/login
SS1: https://34.87.80.93:4000/login
ID: camdx-systemadmin
Password: 123456
You can modify anything
Best Regards,
Dara Penhchet
from x-road.
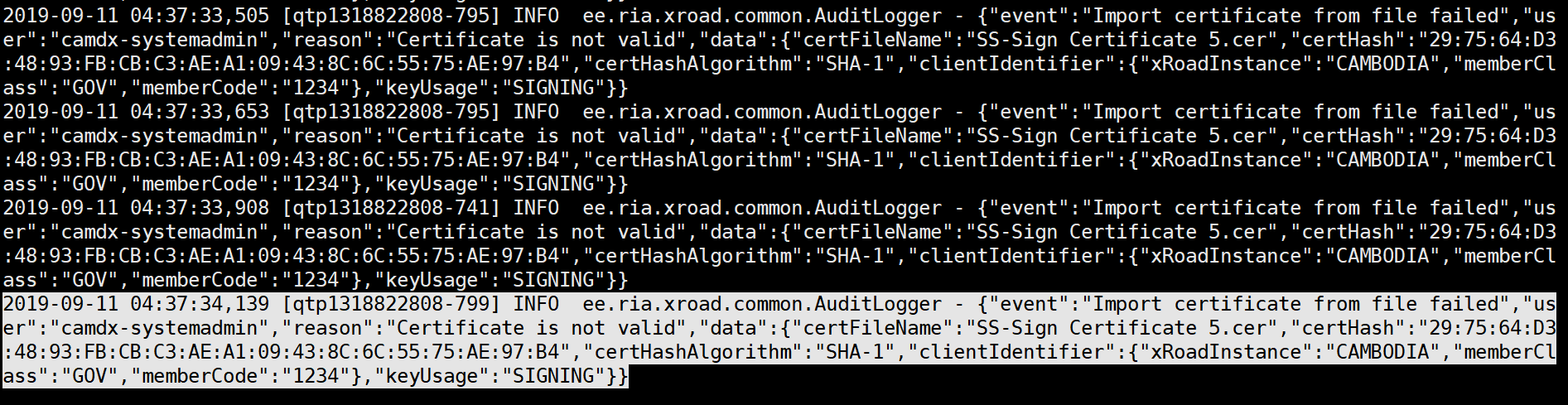
Dear @petkivim ,
I have tried with it again and the error is different. And It Failed to import certificate: Certificate is not valid.
Best Regards,
Dara Penhchet
from x-road.
Dear @darapenhchet
It seems that there's a problem with your EJBCA configuration. Unfortunately, I cannot help you with that, because I have not used EJBCA personally. Maybe @JyrgenSuvalov can help you with configuring EJBCA?
Best regards,
Petteri
from x-road.
Dear @darapenhchet
I also advice you not to share the credentials of your environment publicly. Anyone can copy them from GitHub and access your environment. In case you need to share credentials with someone, it is better to use a private channel for that.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Thanks for you advice. But it is okay because it just the development environment.
Best Regards,
Dara Penhchet
from x-road.
Dear @JyrgenSuvalov ,
Could you help me to configure the EJBCA Server with XRoad?
Best Regards,
Dara Penhchet
from x-road.
For test and development purposes the easiest way to go is install the test-CA using the Ansible script. The test-CA comes with OCSP and TSA which means that it provides all the required trust services.
Your EJBCA installation does not have an OCSP service yet and you also need an additional TSA service to make your X-Road environment operational. Don't forget these components when considering the required effort to get everything up and running. Considering this using the test-CA might be the easiest and fastest way forward.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
I have tried with the test-CA already and it works well, but I want to install the CA for Production but it cannot integrate with XRoad.
And right now I can issue the certificate for Authenticiation and import it to XRoad. But for the SIGNING key is not working it said the certificate is not valid. Do you know what is the problem of this error?
Best Regards,
Dara Penhchet
from x-road.
There's probably something wrong with the EJBCA configuration - most likely it's related to the certificate profile and its attributes.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Here is my Siging Certificate and CSR File. Could you help to check it?
Best Regards,
Dara Penhchet
from x-road.
This is how a valid auth certificate issued by the test-CA looks like:
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 6 (0x6)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=FI, O=Xroad Test Organization X, OU=Xroad Test CA OU, CN=Xroad Test CA CN
Validity
Not Before: Dec 8 14:52:18 2018 GMT
Not After : Dec 3 14:52:18 2038 GMT
Subject: C=FI, O=Test Company, CN=35.176.66.110/serialNumber=PLAYGROUND/testcomss01/COM
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
...
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Data Encipherment, Key Agreement
X509v3 Extended Key Usage:
TLS Web Client Authentication, TLS Web Server Authentication
Signature Algorithm: sha256WithRSAEncryption
...
You should check that your certificate profile contains the same extensions.
In addition, I noticed that you had used the Finnish certificate profile for generating the CSR. That can be seen from the CSR's subject field. You should use the EJBCA profile instead.
Subject: C=FI, O=CAMDX/serialNumber=CAMBODIA/10.10.40.25/GOV, CN=1234
Please check that you have configured the correct certificate profile for your EJBCA on the Central Server. In addition, you must select the EJBCA when you generate the CSR.
ee.ria.xroad.common.certificateprofile.impl.EjbcaCertificateProfileInfoProvider
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Thanks for your help.
Best Regards,
Dara Penhchet
from x-road.
Dear @petkivim ,
Sorry to ask you again.
I have changed the CA to Windows Server and Issued the AUTHENTICATION Certificate Successfully, but for SIGNING Certificate is not working.
Could you help to check this one?
Thanks in advanced,
Best Regards,
Dara Penhchet
from x-road.
Unfortunately, I have no experience with Windows Server's CA. In general, you should check that contents of a sign certificate look like this:
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 3 (0x3)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = FI, O = Xroad Test Organization X, OU = Xroad Test CA OU, CN = Xroad Test CA CN
Validity
Not Before: Dec 8 14:12:41 2018 GMT
Not After : Dec 3 14:12:41 2038 GMT
Subject: C = FI, O = NIIS, CN = 2908758-4, serialNumber = PLAYGROUND/niisss01/ORG
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
...
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Key Usage: critical
Non Repudiation
Signature Algorithm: sha256WithRSAEncryption
...
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Here is my Certificate
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
11:00:00:00:23:4e:cb:f8:04:64:1a:f0:73:00:00:00:00:00:23
Signature Algorithm: sha256WithRSAEncryption
Issuer: DC = kh, DC = gov, DC = camdx, CN = SubCA2019
Validity
Not Before: Sep 11 22:16:56 2019 GMT
Not After : Sep 10 20:35:54 2020 GMT
Subject: serialNumber = CAMBODIA/10.10.40.25/GOV, C = FI, O = CAMDX, CN = 1234
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:93:f9:b2:53:bb:15:5b:f0:16:f4:0e:ab:93:65:
20:31:b5:6a:c2:66:2c:c7:42:ab:73:ef:9a:79:2a:
21:b7:bf:8d:5c:17:d8:d0:0a:2b:ca:cb:1b:49:b8:
50:0d:2e:0f:5b:30:dd:db:3f:eb:bc:e4:d3:10:c5:
af:6c:c2:41:8c:52:10:e7:89:2c:b6:9a:b9:ea:01:
24:ca:f0:06:22:a9:98:9e:59:f2:64:26:0a:d3:df:
4f:28:c9:1c:9b:fb:ec:7d:bc:60:9e:20:e4:94:08:
cd:60:82:0d:cd:88:3f:db:5c:7f:13:4c:3b:8f:75:
5d:87:10:33:35:9d:4c:3c:b7:03:0d:66:b8:a2:d6:
5f:ac:a3:15:94:4e:16:1d:f1:25:a0:3b:9a:67:dc:
9b:9a:5f:69:87:ee:78:64:98:02:c5:7d:35:07:c6:
d9:12:0b:23:fb:95:40:cd:81:8d:73:d8:58:bd:3d:
c2:3b:70:7c:27:00:36:f8:f9:a7:97:95:e8:ef:54:
9a:03:44:1a:08:3f:5c:42:54:a7:bd:90:65:23:22:
60:1f:73:37:ce:10:f4:ac:5f:38:9a:fe:52:df:06:
df:9a:02:d3:4f:c2:27:ed:51:6d:da:93:6e:81:b7:
a5:88:d2:20:75:cf:e7:d1:5f:0a:65:c8:5b:30:54:
8a:01
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
E0:D9:73:98:88:60:FC:51:DC:53:6F:17:EA:0C:52:34:89:05:31:D4
X509v3 Authority Key Identifier:
keyid:86:EE:F1:9C:14:7A:53:38:20:7A:9F:98:41:D8:76:47:2F:1C:42:08
Authority Information Access:
CA Issuers - URI:ldap:///CN=SubCA2019,CN=AIA,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=camdx,DC=gov,DC=kh?cACertificate?base?objectClass=certificationAuthority
X509v3 Key Usage: critical
Non Repudiation
1.3.6.1.4.1.311.21.7:
0,.$+.....7........6...*...4...!m..+...\..d...
Signature Algorithm: sha256WithRSAEncryption
22:f9:3c:a5:04:3d:03:2b:20:90:a7:ce:88:2b:35:ec:17:88:
6a:86:23:1d:f2:33:bb:75:65:00:a1:65:55:90:fb:be:0f:fa:
6c:a4:78:4a:7e:46:2e:68:69:0f:2f:fc:eb:3e:2f:56:6c:eb:
7e:c8:c8:dd:8d:a5:75:ac:ce:be:33:31:8d:e0:31:66:0f:14:
bb:cf:e5:5d:f2:4f:7e:2b:d0:14:f7:d4:77:9a:3b:aa:b5:63:
9b:ff:e4:5e:1b:fa:2d:2f:c0:e7:13:47:84:00:37:ff:b3:32:
e3:3c:8e:8e:e4:05:51:2b:b3:b4:5e:e0:d1:a1:d7:8c:bb:e4:
e2:16:b2:c3:cc:31:5c:59:d0:be:60:22:e9:68:a8:ce:85:b9:
fe:58:67:da:0d:87:99:1d:02:89:b3:28:85:d3:97:7a:32:25:
50:19:4a:25:58:de:a9:29:b8:48:d0:69:ca:71:e0:35:bb:ba:
a6:5a:b5:14:be:ee:0f:1e:07:f2:77:23:91:6e:f3:76:36:8e:
ad:24:9c:18:7c:3f:f0:d2:1e:0d:37:01:3b:77:6b:f9:30:4d:
d7:bc:a6:c2:e6:f5:e9:00:be:12:a1:22:d8:da:ac:1f:0e:92:
70:e1:c9:dc:4f:2c:a6:eb:3e:b8:fc:fd:ba:ea:ad:a9:77:ba:
f2:60:a5:fe
Best Regards,
Dara Penhchet
from x-road.
Dear @petkivim ,
For SIGNING Certificate it works now. Why does it take 1 day to make that certificate is valid to import to SIGNKey?
Best Regards,
Dara Penhchet
from x-road.
Dear @darapenhchet
That's good news! There should not be any delay before the certificate can be imported - it should be possible to import it as soon as it is created. When a certificate is imported, the certificate chain is validated, and in your case the validation failed at first for some reason.
Are your CA's and Security Server's clocks in sync? I noticed that your certificate's validity started from this date/time:Not Before: Sep 11 22:16:56 2019 GMT. Please note that the time zone is GMT (Greenwich Mean Time Zone), and not your local time zone. One potential explanation could be that the certificate was not valid yet when you tried to import it yesterday.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Thanks for your help, I will check that timezone
Best Regards,
Dara Penhchet
from x-road.
Dear brother,
May I ask you one more question?
For CA Certificate is the Root CA or Issuing CA?
Best Regards,
Dara Penhchet
from x-road.
Which certificate are you referring? The screenshot that you tried to add is not showing.
Best regards,
Petteri
from x-road.
Dear @petkivim ,
Here it is
Best Regards,
Dara Penhchet
from x-road.
Dear brother,
For the Timezone is different so how could I update the Timezone in Central Server and Security Server?
Best Regards,
Dara Penhchet
from x-road.
It's the root certificate. In case there are intermediate CAs, they must be configured in the "Intermediate CAs" tab. More information can be found here.
This article explains how to set or change timezone on Ubuntu 18.
Best regards,
Petteri
from x-road.
Thanks you.
Right now I can import both SIGNING and AUTHENTICATION Certificate. but after I clicked the Register it shows error like this
Best Regards,
Dara Penhchet
from x-road.
Dear @petkivim ,
It is caused by the Timezone
Best Regards,
Dara Penhchet
from x-road.
UTC (Coordinated Universal Time) and GMT (Greenwich Mean Time) are equivalent, there is no time difference between them.
You should probably check that the host system clocks are in sync. On Ubuntu/RHEL, one can check the UTC/GMT time with date --utc. If the host system clocks, expressed in GMT / UTC differ, the certificate validity can be in the future from the Security Server point of view. It is recommended to synchronize the host clocks to a NTP time source.
If the clocks are in sync, then you should check how your CA set's the "Not before" date/time in the certificate. Is it the date/time when the certificate is issued or is it a date/time in the future.
Best regards,
Petteri
from x-road.
Dear @petkivim,
Thank you so much for your help. Right now it works well.
Best Regards,
Dara Penhchet
from x-road.
Related Issues (20)
- Ubuntu package 'xroad-base': logic error in 'xroad-base.preinst' HOT 2
- Problem with calling rest service between security Server 1 and Security Server 2 HOT 2
- Error in setting up the TESTCA HOT 3
- Unexpected error writing large object to database. Server.ClientProxy.IOError: LoggingFailed.InternalError: Future timed out after [120 seconds] HOT 5
- Need help in member registration of SS to CS HOT 21
- How to add a new security server in the x-road ecosystem HOT 8
- wrong key usage HOT 2
- Server DNS nane (CN) HOT 4
- expose IP containers HOT 2
- Connect a security server to the central server HOT 3
- Register Auth Cert in Central Server HOT 4
- Change security server ip HOT 12
- I found this tiny typo :) Just wanted to let you know... HOT 1
- As an Ansible user I would like the roles to be in separate repostiories as done usually for Ansible Roles HOT 3
- environment configuration HOT 4
- Support for OpenAPI 3.1 HOT 1
- Required field 'protocolVersion' is missing HOT 6
- Xroad Security Server HOT 1
- X-Road Setup and configuration step by step HOT 3
- X-road issue with building containers (ansible) HOT 1
Recommend Projects
-
 React
React
A declarative, efficient, and flexible JavaScript library for building user interfaces.
-
Vue.js
🖖 Vue.js is a progressive, incrementally-adoptable JavaScript framework for building UI on the web.
-
 Typescript
Typescript
TypeScript is a superset of JavaScript that compiles to clean JavaScript output.
-
TensorFlow
An Open Source Machine Learning Framework for Everyone
-
Django
The Web framework for perfectionists with deadlines.
-
Laravel
A PHP framework for web artisans
-
D3
Bring data to life with SVG, Canvas and HTML. 📊📈🎉
-
Recommend Topics
-
javascript
JavaScript (JS) is a lightweight interpreted programming language with first-class functions.
-
web
Some thing interesting about web. New door for the world.
-
server
A server is a program made to process requests and deliver data to clients.
-
Machine learning
Machine learning is a way of modeling and interpreting data that allows a piece of software to respond intelligently.
-
Visualization
Some thing interesting about visualization, use data art
-
Game
Some thing interesting about game, make everyone happy.
Recommend Org
-
Facebook
We are working to build community through open source technology. NB: members must have two-factor auth.
-
Microsoft
Open source projects and samples from Microsoft.
-
Google
Google ❤️ Open Source for everyone.
-
Alibaba
Alibaba Open Source for everyone
-
D3
Data-Driven Documents codes.
-
Tencent
China tencent open source team.










from x-road.