Managing Your Clusters (including public, private, hybrid, edge, etc.) as easily as Visiting the Internet.
Out of the Box.
A CNCF(Cloud Native Computing Foundation) Sandbox Project.
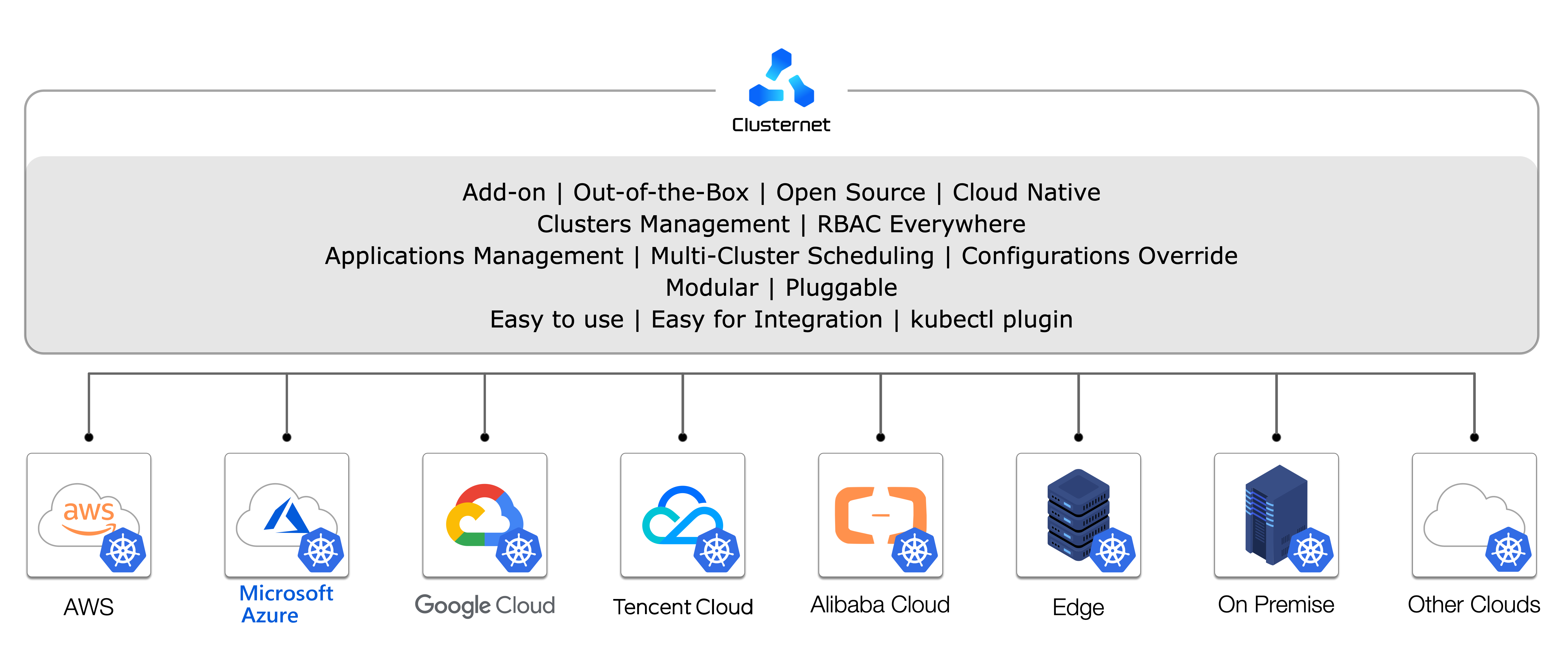
Clusternet (Cluster Internet) is an open source add-on that helps you manage thousands of millions of Kubernetes clusters as easily as visiting the Internet. No matter the clusters are running on public cloud, private cloud, hybrid cloud, or at the edge, Clusternet helps setup network tunnels in a configurable way and lets you manage/visit them all as if they were running locally. This also help eliminate the need to juggle different management tools for each cluster.
Clusternet can also help deploy and coordinate applications to multiple clusters from a single set of APIs in a hosting cluster.
Clusternet also provides a Kubernetes-styled API, where you can continue using the Kubernetes way, such as KubeConfig, to visit a certain Managed Kubernetes cluster, or a Kubernetes service.
Clusternet is multiple platforms supported now, including linux/amd64, linux/arm64, linux/ppc64le, linux/s390x
, linux/386 and linux/arm;
- Kubernetes Multi-Cluster Management and Governance
- managing Kubernetes clusters running in cloud providers, such as AWS, Google Cloud, Tencent Cloud, Alibaba Cloud, etc.
- managing on-premise Kubernetes clusters
- managing any Certified Kubernetes Distributions, such as k3s
- managing Kubernetes clusters running at the edge
- automatically discovering and registering clusters created by cluster-api
- parent cluster can also register itself as a child cluster to run workloads
- managing Kubernetes upper than v1.17.x (Learn more about Kubernetes Version Skew)
- visiting any managed clusters with dynamic RBAC rules (Learn more from this tuorial)
- cluster auto-labelling based on Node Feature Discovery
- Application Coordinations
- Scheduling Framework (
in-treeplugins,out-of-treeplugins) - Cross-Cluster Scheduling
- replication scheduling
- static dividing scheduling by weight
- dynamic dividing scheduling by capacity
- cluster resource predictor framework for
in-treeandout-of-treeimplementations - various deployment topologies for cluster resource predictors
- cluster resource predictor framework for
- subgroup cluster scheduling
- Various Resource Types
- Kubernetes native objects, such as
Deployment,StatefulSet, etc. - CRDs
- helm charts, including OCI-based Helm charts
- Kubernetes native objects, such as
- Resource interpretations with
in-treeorout-of-treecontrollers - Setting Overrides
- two-stage priority based override strategies
- easy to rollback overrides
- cross-cluster canary rollout
- Multi-Cluster Services
- multi-cluster services discovery with mcs-api
- Scheduling Framework (
- CLI
- providing a kubectl plugin, which can be installed with
kubectl krew install clusternet - consistent user experience with
kubectl - create/update/watch/delete multi-cluster resources
- interacting with any child clusters the same as local cluster
- providing a kubectl plugin, which can be installed with
- Client-go
- easy to integrate via a client-go wrapper
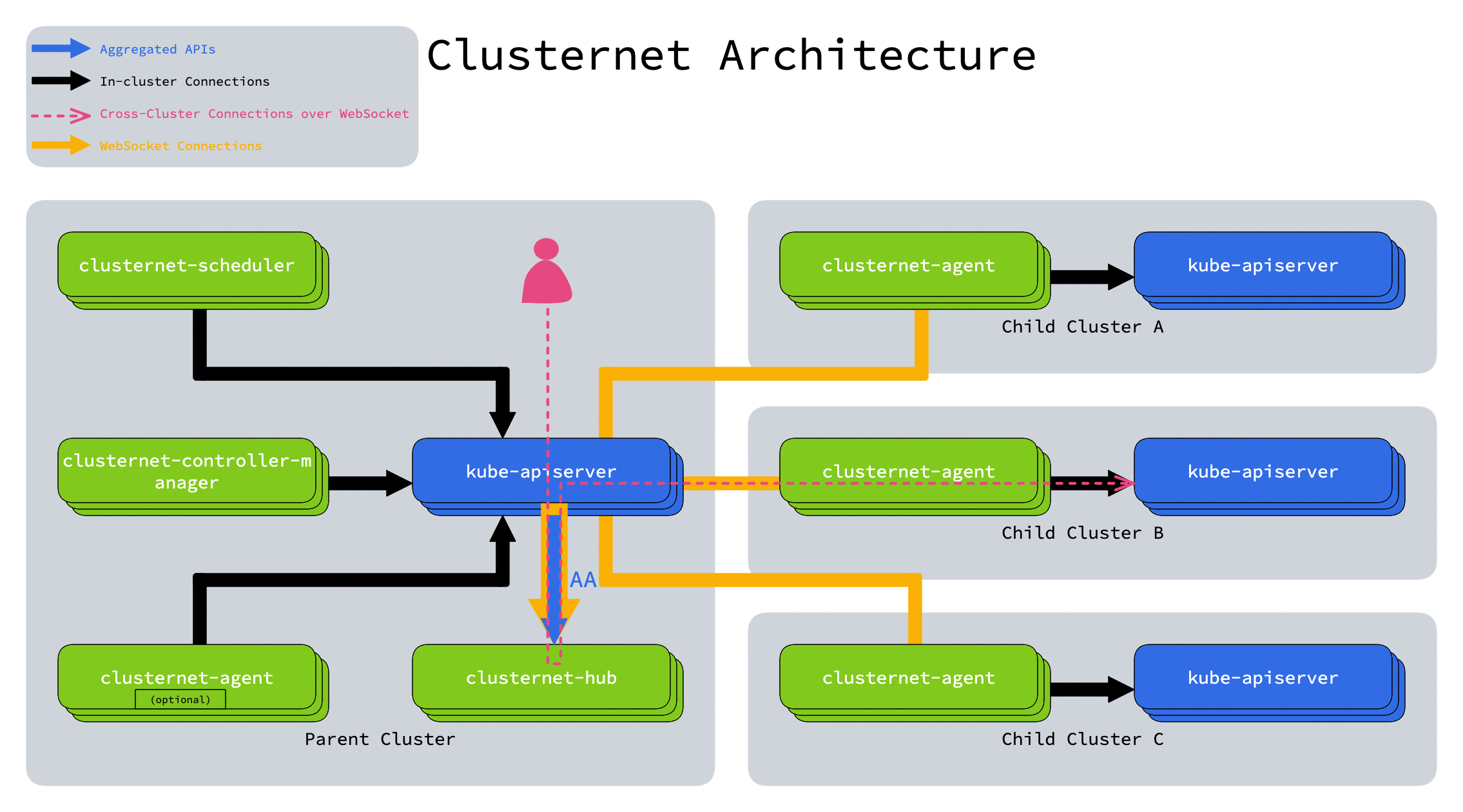
Clusternet is a lightweight addon that consists of four components, clusternet-agent, clusternet-scheduler,
clusternet-controller-manager and clusternet-hub.
Explore the architecture of Clusternet on clusternet.io.
See our documentation on clusternet.io.
The quick start tutorial will walk you through setting up Clusternet locally with kind and deploying applications to multiple clusters.
Try our interactive tutorials that help you understand Clusternet and learn some basic Clusternet features.
If you want to use client-go to interact with Clusternet, we provide a wrapper for easy integration. You can follow demo.go for a quick start.
To use Clusternet APIs and CRDs as a module, please add github.com/clusternet/apis
to your go.mod.
If you've got any questions, please feel free to contact us with following ways:
If you want to get participated and become a contributor to Clusternet, please don't hesitate to refer to our CONTRIBUTING document for details.
A developer guide is ready to help you
- build binaries for all platforms, such as
darwin/amd64,linux/amd64,linux/arm64, etc.; - build docker images for multiple platforms, such as
linux/amd64,linux/arm64, etc.;