Download a statistics report of your repositories.
| Plugin version | Nexus repository version |
|---|---|
| v0.2.1 | >=3.37 |
| v0.2.0 | >=3.28 and <3.37 |
| v0.1.2 | >=3.24 and <3.28 |
| v0.1.1 | >=3.24 and <3.28 |
| v0.1.0 | >=3.24 and <3.28 |
You don't need to build the code to install the plugin, pre-built bundle is available for each version in the assets of the releases on Github.
To build the plugin by yourself, clone the repository and run mvn clean install -PbuildKar in nexus-report-plugin directory. The bundle will be availbale in nexus-report-plugin/target/ with name nexus-report-plugin-<version>-bundle.kar
Copy the .kar file in deploy/ folder of your Nexus server and restart the server.
The users needs the "nx-report-download" permission to perform this action. You can create a new role with it or add it to an existing one. Of course, an administrator has this permission by default.
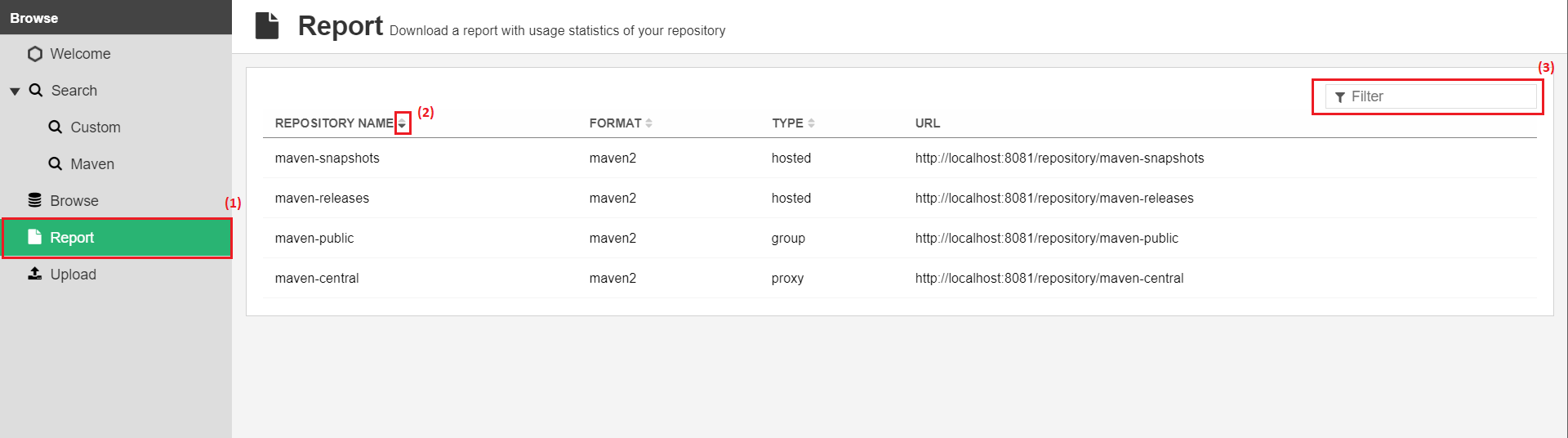
If one of yours roles has the permission "nx-report-download", you should see a "Report" button (1) on the left side menu. When you click on it a list of your granted repositories will be displayed. You have the possibility to sort it (2) or filter it (3) with the field at the top-right. When you click on a repository of the list, it will download the report associated to this repository.
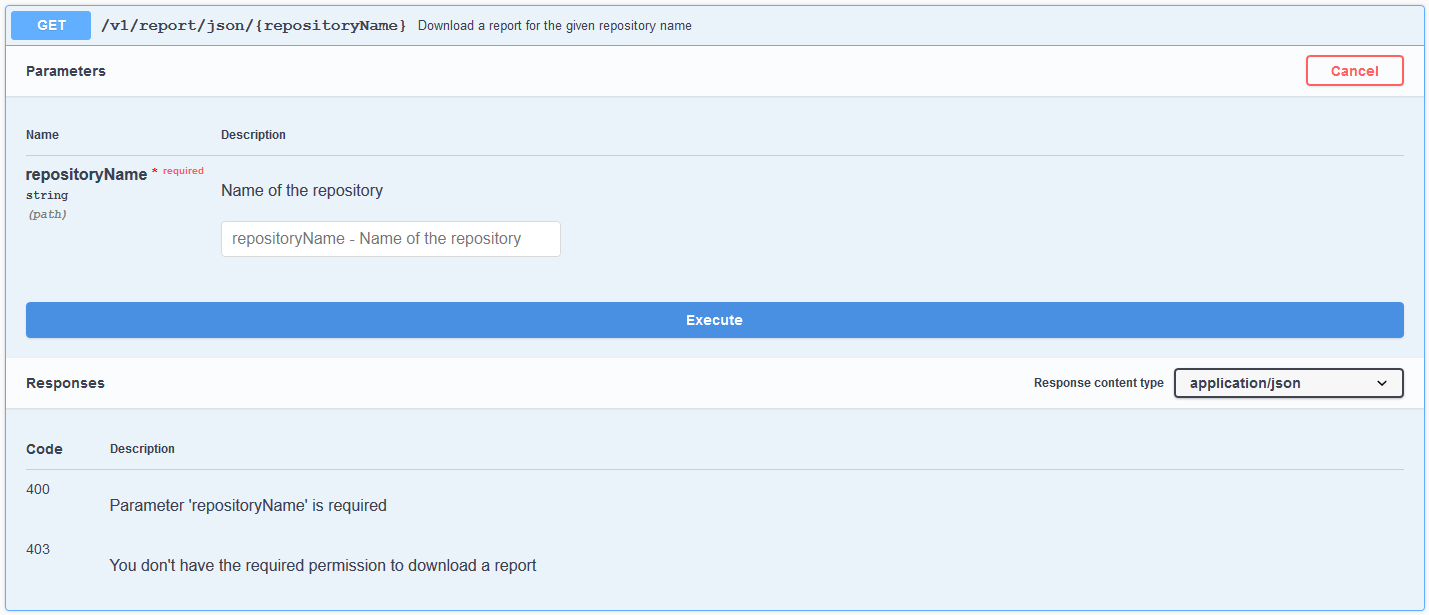
Since 0.1.2, it is possible to get the informations in JSON format contacting the api /service/rest/v1/report/json/.
This api is available in System API on the UI, but you cannot get it directly with the "Report" button.
the right "nx-report-download" and an access to the repository are needed to get the JSON report.
Curl
curl -X GET "http://localhost:8081/service/rest/v1/report/json/maven-releases" -H "accept: application/json"
Response code
200
Response headers
content-length: 735 content-type: application/json date: Wed, 30 Sep 2020 23:21:09 GMT server: Nexus/3.24.0-02 (OSS) x-content-type-options: nosniff
Response body
[
{
"group": "org.sonatype.nexus.plugins",
"name": "nexus-report-plugin",
"version": "0.1.2",
"format": "maven2",
"size": 3686343,
"sizeMB": 3.52,
"sizeGB": 0,
"createdBy": "admin",
"lastUpdated": "2020-10-01T01:17:52",
"lastDownloaded": "never",
"encoded": "bWF2ZW4tcmVsZWFzZXM6ODg0OTFjZDFkMTg1ZGQxMzYzMjY4ZjIyMGU0NWQ3ZGU"
},
{
"group": "org.sonatype.nexus",
"name": "nexus-ui-plugin",
"version": "3.24.0-02",
"format": "maven2",
"size": 5494,
"sizeMB": 0.01,
"sizeGB": 0,
"createdBy": "admin",
"lastUpdated": "2020-10-01T01:20:41",
"lastDownloaded": "never",
"encoded": "bWF2ZW4tcmVsZWFzZXM6YzBhYzJhYjZjNWU5M2E0YTc2Zjc5OTEwMjllMDk0Yzg"
}
]
System/API
Product Owner: Cloudehard
Developer: mat1e
Looking to contribute to our code but need some help? There's a few ways to get information:
- Check out the Nexus3 tag on Stack Overflow
- Check out the Nexus Repository User List
- Open an issue on this repository