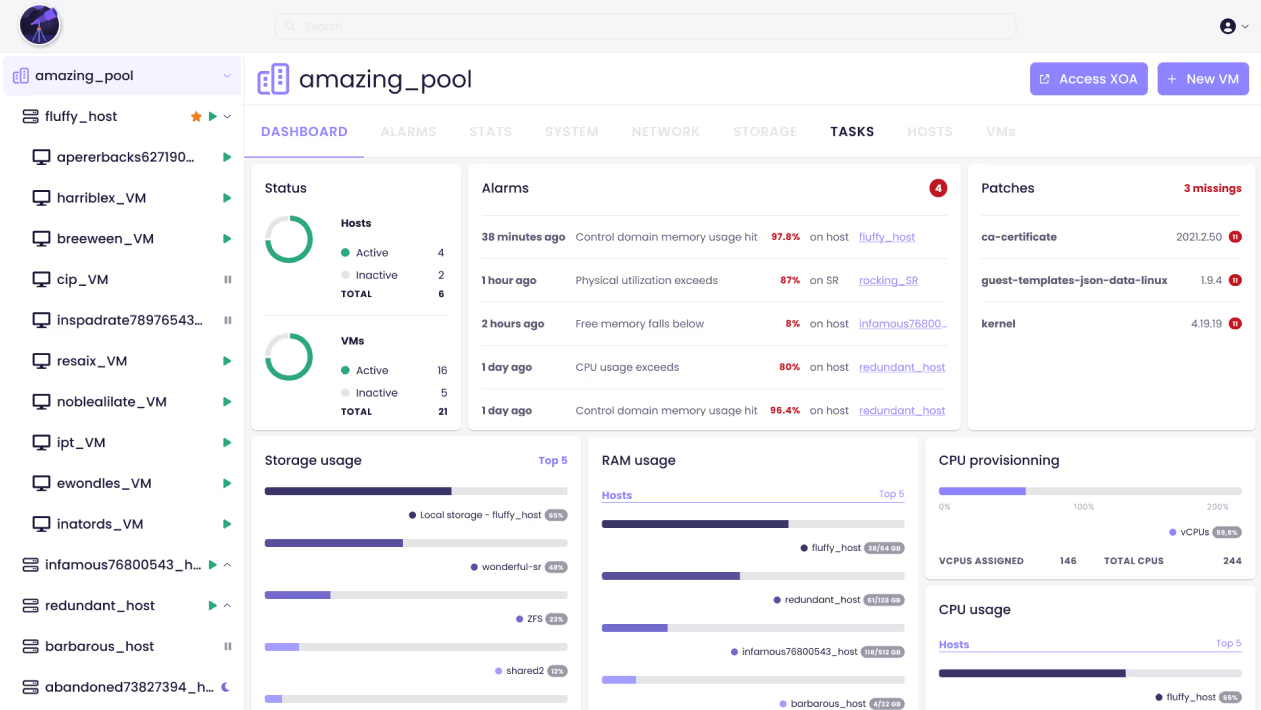
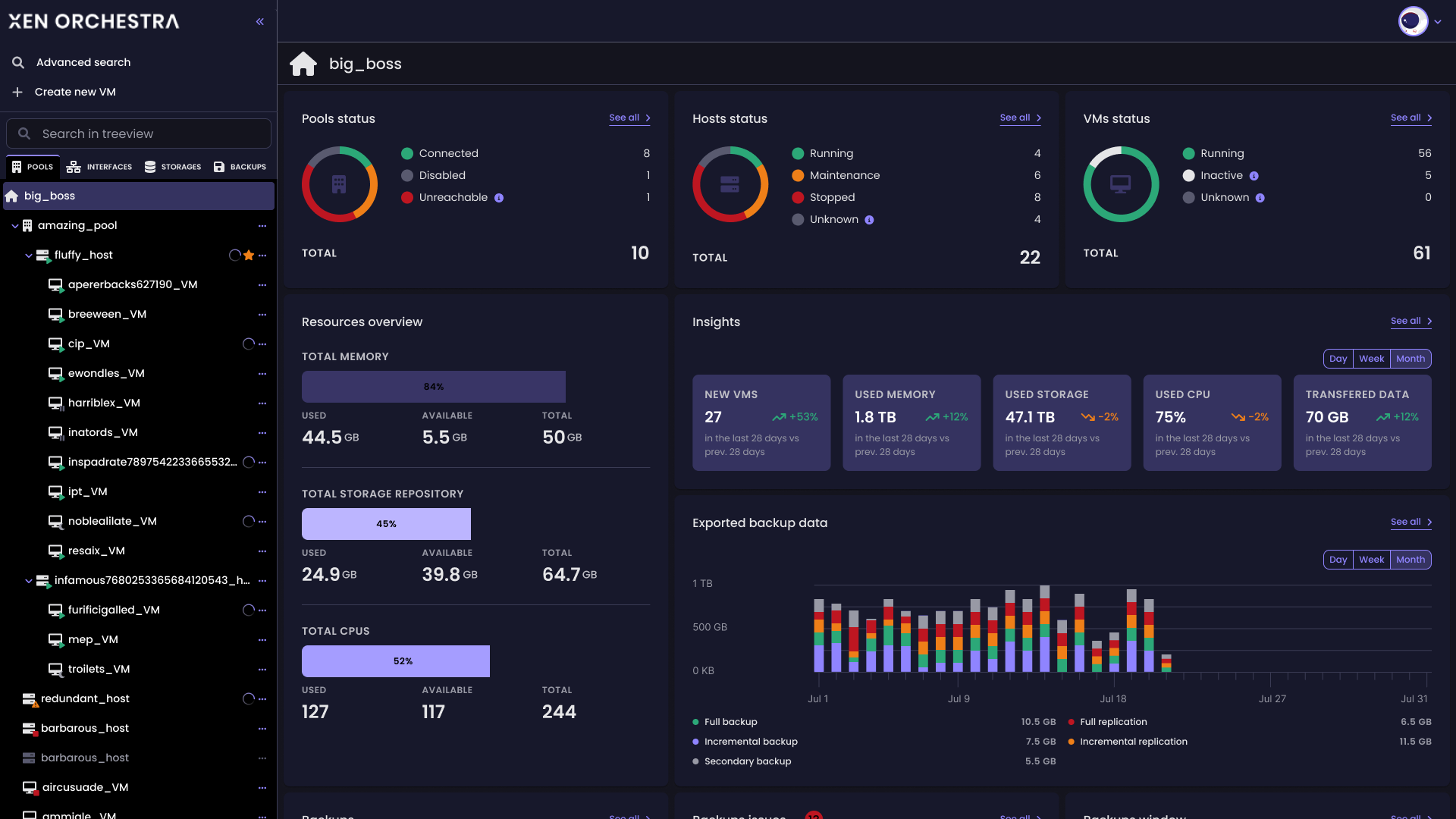
already tested xcp 7.4 and 7.4.1 with no issues.
installed 7.5 from scratch and I cannot enable HA.
Tried with NFS and FC, also with GFS2 and LVM.
Aug 14 12:07:20 xcp-ng-1 SM: [31960] if self._deactivate_locked(sr_uuid, vdi_uuid, caching_params):
Aug 14 12:07:20 xcp-ng-1 SM: [31960] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:07:20 xcp-ng-1 SM: [31960] ret = op(self, *args)
Aug 14 12:07:20 xcp-ng-1 SM: [31960] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:07:20 xcp-ng-1 SM: [31960] self._remove_tag(vdi_uuid)
Aug 14 12:07:20 xcp-ng-1 SM: [31960] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:07:20 xcp-ng-1 SM: [31960] assert sm_config.has_key(host_key)
Aug 14 12:07:20 xcp-ng-1 SM: [31960]
Aug 14 12:07:20 xcp-ng-1 SM: [31960] lock: closed /var/lock/sm/b7b8b6a2-6326-4402-9f95-96135bb1d2f7/vdi
Aug 14 12:07:20 xcp-ng-1 SM: [31960] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:51 xcp-ng-1 SM: [32437] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:51 xcp-ng-1 SM: [32437] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:51 xcp-ng-1 SM: [32437] lock: opening lock file /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:51 xcp-ng-1 SM: [32437] LVMCache created for VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb
Aug 14 12:08:51 xcp-ng-1 SM: [32437] ['/sbin/vgs', 'VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:51 xcp-ng-1 SM: [32437] pread SUCCESS
Aug 14 12:08:51 xcp-ng-1 SM: [32437] lock: acquired /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:51 xcp-ng-1 SM: [32437] LVMCache: will initialize now
Aug 14 12:08:51 xcp-ng-1 SM: [32437] LVMCache: refreshing
Aug 14 12:08:51 xcp-ng-1 SM: [32437] ['/sbin/lvs', '--noheadings', '--units', 'b', '-o', '+lv_tags', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:51 xcp-ng-1 SM: [32437] pread SUCCESS
Aug 14 12:08:51 xcp-ng-1 SM: [32437] lock: released /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:51 xcp-ng-1 SM: [32437] Entering _checkMetadataVolume
Aug 14 12:08:51 xcp-ng-1 SM: [32437] vdi_generate_config {'sr_uuid': 'e6c74423-9152-b3b9-f503-efccde0e3edb', 'subtask_of': 'OpaqueRef:5b5a6883-145d-404a-b9e3-e0715b227549', 'vdi_ref': 'OpaqueRef:94e45b2c-d99f-44e9-a4b5-e9660c99ecb4', 'vdi_on_boot': 'persist', 'args': [], 'vdi_location': 'ed1ae7c2-a5cb-4989-8bd2-7e351b77c835', 'host_ref': 'OpaqueRef:e4c37665-3b24-4b25-9da3-cf3567000e4b', 'session_ref': 'OpaqueRef:7f0ea971-e941-448f-a4a8-26af782c34a3', 'device_config': {'device': '/dev/disk/by-id/scsi-3600000e00d00000000012a6b00000000', 'SCSIid': '3600000e00d00000000012a6b00000000', 'SRmaster': 'true'}, 'command': 'vdi_generate_config', 'vdi_allow_caching': 'false', 'sr_ref': 'OpaqueRef:ddd6717d-987e-4618-9686-21af1f6bd7ff', 'vdi_uuid': 'ed1ae7c2-a5cb-4989-8bd2-7e351b77c835'}
Aug 14 12:08:51 xcp-ng-1 SM: [32437] LVHDoHBAVDI.generate_config
Aug 14 12:08:51 xcp-ng-1 SM: [32437] ['/sbin/lvdisplay', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb/LV-ed1ae7c2-a5cb-4989-8bd2-7e351b77c835']
Aug 14 12:08:51 xcp-ng-1 SM: [32437] pread SUCCESS
Aug 14 12:08:51 xcp-ng-1 SM: [32437] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:52 xcp-ng-1 SM: [32462] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:52 xcp-ng-1 SM: [32462] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:52 xcp-ng-1 SM: [32462] Caught exception while looking up PBD for host SR None: 'NoneType' object has no attribute 'xenapi'
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: opening lock file /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:52 xcp-ng-1 SM: [32462] LVMCache created for VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb
Aug 14 12:08:52 xcp-ng-1 SM: [32462] ['/sbin/vgs', 'VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:52 xcp-ng-1 SM: [32462] pread SUCCESS
Aug 14 12:08:52 xcp-ng-1 SM: [32462] LVMCache: will initialize now
Aug 14 12:08:52 xcp-ng-1 SM: [32462] LVMCache: refreshing
Aug 14 12:08:52 xcp-ng-1 SM: [32462] ['/sbin/lvs', '--noheadings', '--units', 'b', '-o', '+lv_tags', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:52 xcp-ng-1 SM: [32462] pread SUCCESS
Aug 14 12:08:52 xcp-ng-1 SM: [32462] vdi_attach_from_config {'sr_uuid': 'e6c74423-9152-b3b9-f503-efccde0e3edb', 'device_config': {'device': '/dev/disk/by-id/scsi-3600000e00d00000000012a6b00000000', 'multipathing': 'false', 'SCSIid': '3600000e00d00000000012a6b00000000', 'SRmaster': 'true', 'multipathhandle': 'null'}, 'command': 'vdi_attach_from_config', 'vdi_uuid': 'ed1ae7c2-a5cb-4989-8bd2-7e351b77c835'}
Aug 14 12:08:52 xcp-ng-1 SM: [32462] LVHDoHBAVDI.attach_from_config
Aug 14 12:08:52 xcp-ng-1 SM: [32462] LVHDVDI.attach for ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:ed1ae7c2-a5cb-4989-8bd2-7e351b77c835 (0, 0) + (0, 1) => (0, 1)
Aug 14 12:08:52 xcp-ng-1 SM: [32462] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:ed1ae7c2-a5cb-4989-8bd2-7e351b77c835 set => (0, 1b)
Aug 14 12:08:52 xcp-ng-1 SM: [32462] ['/sbin/lvchange', '-ay', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb/LV-ed1ae7c2-a5cb-4989-8bd2-7e351b77c835']
Aug 14 12:08:52 xcp-ng-1 SM: [32462] pread SUCCESS
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:08:52 xcp-ng-1 SM: [32462] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:52 xcp-ng-1 SM: [32523] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:52 xcp-ng-1 SM: [32523] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:52 xcp-ng-1 SM: [32523] lock: opening lock file /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:52 xcp-ng-1 SM: [32523] LVMCache created for VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb
Aug 14 12:08:52 xcp-ng-1 SM: [32523] ['/sbin/vgs', 'VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:52 xcp-ng-1 SM: [32523] pread SUCCESS
Aug 14 12:08:52 xcp-ng-1 SM: [32523] lock: acquired /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:52 xcp-ng-1 SM: [32523] LVMCache: will initialize now
Aug 14 12:08:52 xcp-ng-1 SM: [32523] LVMCache: refreshing
Aug 14 12:08:52 xcp-ng-1 SM: [32523] ['/sbin/lvs', '--noheadings', '--units', 'b', '-o', '+lv_tags', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:52 xcp-ng-1 SM: [32523] pread SUCCESS
Aug 14 12:08:52 xcp-ng-1 SM: [32523] lock: released /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:52 xcp-ng-1 SM: [32523] Entering _checkMetadataVolume
Aug 14 12:08:52 xcp-ng-1 SM: [32523] vdi_generate_config {'sr_uuid': 'e6c74423-9152-b3b9-f503-efccde0e3edb', 'subtask_of': 'OpaqueRef:8d0fbda6-bf9c-47cc-a625-f4f2eb6af9b6', 'vdi_ref': 'OpaqueRef:b34971ea-0441-4266-8413-23a22ef5a226', 'vdi_on_boot': 'persist', 'args': [], 'vdi_location': 'b7b8b6a2-6326-4402-9f95-96135bb1d2f7', 'host_ref': 'OpaqueRef:e4c37665-3b24-4b25-9da3-cf3567000e4b', 'session_ref': 'OpaqueRef:e17028c1-a39d-4751-a809-84b2a25c6920', 'device_config': {'device': '/dev/disk/by-id/scsi-3600000e00d00000000012a6b00000000', 'SCSIid': '3600000e00d00000000012a6b00000000', 'SRmaster': 'true'}, 'command': 'vdi_generate_config', 'vdi_allow_caching': 'false', 'sr_ref': 'OpaqueRef:ddd6717d-987e-4618-9686-21af1f6bd7ff', 'vdi_uuid': 'b7b8b6a2-6326-4402-9f95-96135bb1d2f7'}
Aug 14 12:08:52 xcp-ng-1 SM: [32523] LVHDoHBAVDI.generate_config
Aug 14 12:08:52 xcp-ng-1 SM: [32523] ['/sbin/lvdisplay', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb/LV-b7b8b6a2-6326-4402-9f95-96135bb1d2f7']
Aug 14 12:08:52 xcp-ng-1 SM: [32523] pread SUCCESS
Aug 14 12:08:52 xcp-ng-1 SM: [32523] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:53 xcp-ng-1 SM: [32553] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:53 xcp-ng-1 SM: [32553] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:08:53 xcp-ng-1 SM: [32553] Caught exception while looking up PBD for host SR None: 'NoneType' object has no attribute 'xenapi'
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: opening lock file /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:08:53 xcp-ng-1 SM: [32553] LVMCache created for VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb
Aug 14 12:08:53 xcp-ng-1 SM: [32553] ['/sbin/vgs', 'VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:53 xcp-ng-1 SM: [32553] pread SUCCESS
Aug 14 12:08:53 xcp-ng-1 SM: [32553] LVMCache: will initialize now
Aug 14 12:08:53 xcp-ng-1 SM: [32553] LVMCache: refreshing
Aug 14 12:08:53 xcp-ng-1 SM: [32553] ['/sbin/lvs', '--noheadings', '--units', 'b', '-o', '+lv_tags', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:08:53 xcp-ng-1 SM: [32553] pread SUCCESS
Aug 14 12:08:53 xcp-ng-1 SM: [32553] vdi_attach_from_config {'sr_uuid': 'e6c74423-9152-b3b9-f503-efccde0e3edb', 'device_config': {'device': '/dev/disk/by-id/scsi-3600000e00d00000000012a6b00000000', 'multipathing': 'false', 'SCSIid': '3600000e00d00000000012a6b00000000', 'SRmaster': 'true', 'multipathhandle': 'null'}, 'command': 'vdi_attach_from_config', 'vdi_uuid': 'b7b8b6a2-6326-4402-9f95-96135bb1d2f7'}
Aug 14 12:08:53 xcp-ng-1 SM: [32553] LVHDoHBAVDI.attach_from_config
Aug 14 12:08:53 xcp-ng-1 SM: [32553] LVHDVDI.attach for b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:b7b8b6a2-6326-4402-9f95-96135bb1d2f7 (0, 0) + (0, 1) => (0, 1)
Aug 14 12:08:53 xcp-ng-1 SM: [32553] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:b7b8b6a2-6326-4402-9f95-96135bb1d2f7 set => (0, 1b)
Aug 14 12:08:53 xcp-ng-1 SM: [32553] ['/sbin/lvchange', '-ay', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb/LV-b7b8b6a2-6326-4402-9f95-96135bb1d2f7']
Aug 14 12:08:53 xcp-ng-1 SM: [32553] pread SUCCESS
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:08:53 xcp-ng-1 SM: [32553] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:09:02 xcp-ng-1 SM: [32739] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:09:02 xcp-ng-1 SM: [32739] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: opening lock file /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:09:02 xcp-ng-1 SM: [32739] LVMCache created for VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ['/sbin/vgs', 'VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:09:02 xcp-ng-1 SM: [32739] pread SUCCESS
Aug 14 12:09:02 xcp-ng-1 SM: [32739] Entering _checkMetadataVolume
Aug 14 12:09:02 xcp-ng-1 SM: [32739] LVMCache: will initialize now
Aug 14 12:09:02 xcp-ng-1 SM: [32739] LVMCache: refreshing
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ['/sbin/lvs', '--noheadings', '--units', 'b', '-o', '+lv_tags', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:09:02 xcp-ng-1 SM: [32739] pread SUCCESS
Aug 14 12:09:02 xcp-ng-1 SM: [32739] vdi_deactivate {'sr_uuid': 'e6c74423-9152-b3b9-f503-efccde0e3edb', 'subtask_of': 'OpaqueRef:57f4932a-adc1-421c-b94e-0af161d6cc3b', 'vdi_ref': 'OpaqueRef:94e45b2c-d99f-44e9-a4b5-e9660c99ecb4', 'vdi_on_boot': 'persist', 'args': [], 'vdi_location': 'ed1ae7c2-a5cb-4989-8bd2-7e351b77c835', 'host_ref': 'OpaqueRef:e4c37665-3b24-4b25-9da3-cf3567000e4b', 'session_ref': 'OpaqueRef:4163f1d4-23b4-4bfb-b381-8fa437e66ce8', 'device_config': {'device': '/dev/disk/by-id/scsi-3600000e00d00000000012a6b00000000', 'SCSIid': '3600000e00d00000000012a6b00000000', 'SRmaster': 'true'}, 'command': 'vdi_deactivate', 'vdi_allow_caching': 'false', 'sr_ref': 'OpaqueRef:ddd6717d-987e-4618-9686-21af1f6bd7ff', 'vdi_uuid': 'ed1ae7c2-a5cb-4989-8bd2-7e351b77c835'}
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: opening lock file /var/lock/sm/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835/vdi
Aug 14 12:09:02 xcp-ng-1 SM: [32739] blktap2.deactivate
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: acquired /var/lock/sm/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835/vdi
Aug 14 12:09:02 xcp-ng-1 SM: [32739] Backend path /dev/sm/backend/e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835 does not exist
Aug 14 12:09:02 xcp-ng-1 SM: [32739] LVHDVDI.detach for ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:ed1ae7c2-a5cb-4989-8bd2-7e351b77c835 (0, 1) + (0, -1) => (0, 0)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:ed1ae7c2-a5cb-4989-8bd2-7e351b77c835 set => (0, 0b)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ['/sbin/lvchange', '-an', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb/LV-ed1ae7c2-a5cb-4989-8bd2-7e351b77c835']
Aug 14 12:09:02 xcp-ng-1 SM: [32739] pread SUCCESS
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ['/sbin/dmsetup', 'status', 'VG_XenStorage--e6c74423--9152--b3b9--f503--efccde0e3edb-LV--ed1ae7c2--a5cb--4989--8bd2--7e351b77c835']
Aug 14 12:09:02 xcp-ng-1 SM: [32739] pread SUCCESS
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ***** BLKTAP2:<function _deactivate_locked at 0x1356500>: EXCEPTION <type 'exceptions.AssertionError'>,
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ret = op(self, *args)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:09:02 xcp-ng-1 SM: [32739] self._remove_tag(vdi_uuid)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:09:02 xcp-ng-1 SM: [32739] assert sm_config.has_key(host_key)
Aug 14 12:09:02 xcp-ng-1 SM: [32739]
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: released /var/lock/sm/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835/vdi
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ***** generic exception: vdi_deactivate: EXCEPTION <type 'exceptions.AssertionError'>,
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 110, in run
Aug 14 12:09:02 xcp-ng-1 SM: [32739] return self._run_locked(sr)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 159, in _run_locked
Aug 14 12:09:02 xcp-ng-1 SM: [32739] rv = self._run(sr, target)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 274, in _run
Aug 14 12:09:02 xcp-ng-1 SM: [32739] caching_params)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1647, in deactivate
Aug 14 12:09:02 xcp-ng-1 SM: [32739] if self._deactivate_locked(sr_uuid, vdi_uuid, caching_params):
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ret = op(self, *args)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:09:02 xcp-ng-1 SM: [32739] self._remove_tag(vdi_uuid)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:09:02 xcp-ng-1 SM: [32739] assert sm_config.has_key(host_key)
Aug 14 12:09:02 xcp-ng-1 SM: [32739]
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ***** LVHD over FC: EXCEPTION <type 'exceptions.AssertionError'>,
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 372, in run
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ret = cmd.run(sr)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 110, in run
Aug 14 12:09:02 xcp-ng-1 SM: [32739] return self._run_locked(sr)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 159, in _run_locked
Aug 14 12:09:02 xcp-ng-1 SM: [32739] rv = self._run(sr, target)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/SRCommand.py", line 274, in _run
Aug 14 12:09:02 xcp-ng-1 SM: [32739] caching_params)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1647, in deactivate
Aug 14 12:09:02 xcp-ng-1 SM: [32739] if self._deactivate_locked(sr_uuid, vdi_uuid, caching_params):
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:09:02 xcp-ng-1 SM: [32739] ret = op(self, *args)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:09:02 xcp-ng-1 SM: [32739] self._remove_tag(vdi_uuid)
Aug 14 12:09:02 xcp-ng-1 SM: [32739] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:09:02 xcp-ng-1 SM: [32739] assert sm_config.has_key(host_key)
Aug 14 12:09:02 xcp-ng-1 SM: [32739]
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: closed /var/lock/sm/ed1ae7c2-a5cb-4989-8bd2-7e351b77c835/vdi
Aug 14 12:09:02 xcp-ng-1 SM: [32739] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:09:03 xcp-ng-1 SM: [330] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:09:03 xcp-ng-1 SM: [330] Setting LVM_DEVICE to /dev/disk/by-scsid/3600000e00d00000000012a6b00000000
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: opening lock file /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr
Aug 14 12:09:03 xcp-ng-1 SM: [330] LVMCache created for VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb
Aug 14 12:09:03 xcp-ng-1 SM: [330] ['/sbin/vgs', 'VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:09:03 xcp-ng-1 SM: [330] pread SUCCESS
Aug 14 12:09:03 xcp-ng-1 SM: [330] Entering _checkMetadataVolume
Aug 14 12:09:03 xcp-ng-1 SM: [330] LVMCache: will initialize now
Aug 14 12:09:03 xcp-ng-1 SM: [330] LVMCache: refreshing
Aug 14 12:09:03 xcp-ng-1 SM: [330] ['/sbin/lvs', '--noheadings', '--units', 'b', '-o', '+lv_tags', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb']
Aug 14 12:09:03 xcp-ng-1 SM: [330] pread SUCCESS
Aug 14 12:09:03 xcp-ng-1 SM: [330] vdi_deactivate {'sr_uuid': 'e6c74423-9152-b3b9-f503-efccde0e3edb', 'subtask_of': 'OpaqueRef:57f4932a-adc1-421c-b94e-0af161d6cc3b', 'vdi_ref': 'OpaqueRef:b34971ea-0441-4266-8413-23a22ef5a226', 'vdi_on_boot': 'persist', 'args': [], 'vdi_location': 'b7b8b6a2-6326-4402-9f95-96135bb1d2f7', 'host_ref': 'OpaqueRef:e4c37665-3b24-4b25-9da3-cf3567000e4b', 'session_ref': 'OpaqueRef:2561aac2-7579-4ad7-8e9e-232bd6b64efa', 'device_config': {'device': '/dev/disk/by-id/scsi-3600000e00d00000000012a6b00000000', 'SCSIid': '3600000e00d00000000012a6b00000000', 'SRmaster': 'true'}, 'command': 'vdi_deactivate', 'vdi_allow_caching': 'false', 'sr_ref': 'OpaqueRef:ddd6717d-987e-4618-9686-21af1f6bd7ff', 'vdi_uuid': 'b7b8b6a2-6326-4402-9f95-96135bb1d2f7'}
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: opening lock file /var/lock/sm/b7b8b6a2-6326-4402-9f95-96135bb1d2f7/vdi
Aug 14 12:09:03 xcp-ng-1 SM: [330] blktap2.deactivate
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: acquired /var/lock/sm/b7b8b6a2-6326-4402-9f95-96135bb1d2f7/vdi
Aug 14 12:09:03 xcp-ng-1 SM: [330] Backend path /dev/sm/backend/e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7 does not exist
Aug 14 12:09:03 xcp-ng-1 SM: [330] LVHDVDI.detach for b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: opening lock file /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: acquired /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:b7b8b6a2-6326-4402-9f95-96135bb1d2f7 (0, 1) + (0, -1) => (0, 0)
Aug 14 12:09:03 xcp-ng-1 SM: [330] Refcount for lvm-e6c74423-9152-b3b9-f503-efccde0e3edb:b7b8b6a2-6326-4402-9f95-96135bb1d2f7 set => (0, 0b)
Aug 14 12:09:03 xcp-ng-1 SM: [330] ['/sbin/lvchange', '-an', '/dev/VG_XenStorage-e6c74423-9152-b3b9-f503-efccde0e3edb/LV-b7b8b6a2-6326-4402-9f95-96135bb1d2f7']
Aug 14 12:09:03 xcp-ng-1 SM: [330] pread SUCCESS
Aug 14 12:09:03 xcp-ng-1 SM: [330] ['/sbin/dmsetup', 'status', 'VG_XenStorage--e6c74423--9152--b3b9--f503--efccde0e3edb-LV--b7b8b6a2--6326--4402--9f95--96135bb1d2f7']
Aug 14 12:09:03 xcp-ng-1 SM: [330] pread SUCCESS
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: released /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: closed /var/lock/sm/lvm-e6c74423-9152-b3b9-f503-efccde0e3edb/b7b8b6a2-6326-4402-9f95-96135bb1d2f7
Aug 14 12:09:03 xcp-ng-1 SM: [330] ***** BLKTAP2:<function _deactivate_locked at 0x16cc500>: EXCEPTION <type 'exceptions.AssertionError'>,
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:09:03 xcp-ng-1 SM: [330] ret = op(self, *args)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:09:03 xcp-ng-1 SM: [330] self._remove_tag(vdi_uuid)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:09:03 xcp-ng-1 SM: [330] assert sm_config.has_key(host_key)
Aug 14 12:09:03 xcp-ng-1 SM: [330]
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: released /var/lock/sm/b7b8b6a2-6326-4402-9f95-96135bb1d2f7/vdi
Aug 14 12:09:03 xcp-ng-1 SM: [330] ***** generic exception: vdi_deactivate: EXCEPTION <type 'exceptions.AssertionError'>,
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 110, in run
Aug 14 12:09:03 xcp-ng-1 SM: [330] return self._run_locked(sr)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 159, in _run_locked
Aug 14 12:09:03 xcp-ng-1 SM: [330] rv = self._run(sr, target)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 274, in _run
Aug 14 12:09:03 xcp-ng-1 SM: [330] caching_params)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1647, in deactivate
Aug 14 12:09:03 xcp-ng-1 SM: [330] if self._deactivate_locked(sr_uuid, vdi_uuid, caching_params):
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:09:03 xcp-ng-1 SM: [330] ret = op(self, *args)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:09:03 xcp-ng-1 SM: [330] self._remove_tag(vdi_uuid)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:09:03 xcp-ng-1 SM: [330] assert sm_config.has_key(host_key)
Aug 14 12:09:03 xcp-ng-1 SM: [330]
Aug 14 12:09:03 xcp-ng-1 SM: [330] ***** LVHD over FC: EXCEPTION <type 'exceptions.AssertionError'>,
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 372, in run
Aug 14 12:09:03 xcp-ng-1 SM: [330] ret = cmd.run(sr)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 110, in run
Aug 14 12:09:03 xcp-ng-1 SM: [330] return self._run_locked(sr)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 159, in _run_locked
Aug 14 12:09:03 xcp-ng-1 SM: [330] rv = self._run(sr, target)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/SRCommand.py", line 274, in _run
Aug 14 12:09:03 xcp-ng-1 SM: [330] caching_params)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1647, in deactivate
Aug 14 12:09:03 xcp-ng-1 SM: [330] if self._deactivate_locked(sr_uuid, vdi_uuid, caching_params):
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 83, in wrapper
Aug 14 12:09:03 xcp-ng-1 SM: [330] ret = op(self, *args)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1666, in _deactivate_locked
Aug 14 12:09:03 xcp-ng-1 SM: [330] self._remove_tag(vdi_uuid)
Aug 14 12:09:03 xcp-ng-1 SM: [330] File "/opt/xensource/sm/blktap2.py", line 1452, in _remove_tag
Aug 14 12:09:03 xcp-ng-1 SM: [330] assert sm_config.has_key(host_key)
Aug 14 12:09:03 xcp-ng-1 SM: [330]
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: closed /var/lock/sm/b7b8b6a2-6326-4402-9f95-96135bb1d2f7/vdi
Aug 14 12:09:03 xcp-ng-1 SM: [330] lock: closed /var/lock/sm/e6c74423-9152-b3b9-f503-efccde0e3edb/sr